Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2024-20270 |
Description: A vulnerability in the web-based management interface of Cisco BroadWorks Application Delivery Platform and Cisco BroadWorks Xtended Services Platform could allow an authenticated, remote attacker to conduct a stored cross-site scripting (XSS) attack against a user of the interface.
This vulnerability exists because the web-based management interface does not properly validate user-supplied input. An attacker could exploit this vulnerability by persuading a user of the interface to click a crafted link. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive, browser-based information.
CVSS: MEDIUM (4.8) EPSS Score: 0.05% SSVC Exploitation: none
June 2nd, 2025 (5 days ago)
|
|
CVE-2024-20509 |
Description:
A vulnerability in the Cisco AnyConnect VPN server of Cisco Meraki MX and Cisco Meraki Z Series Teleworker Gateway devices could allow an unauthenticated, remote attacker to hijack an AnyConnect VPN session or cause a denial of service (DoS) condition for individual users of the AnyConnect VPN service on an affected device.
This vulnerability is due to weak entropy for handlers that are used during the VPN authentication process as well as a race condition that exists in the same process. An attacker could exploit this vulnerability by correctly guessing an authentication handler and then sending crafted HTTPS requests to an affected device. A successful exploit could allow the attacker to take over the AnyConnect VPN session from a target user or prevent the target user from establishing an AnyConnect VPN session with the affected device.
Cisco Meraki has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-meraki-mx-vpn-dos-by-QWUkqV7X
Security Impact Rating: Medium
CVE: CVE-2024-20509
CVSS: MEDIUM (5.8) EPSS Score: 0.04%
June 2nd, 2025 (5 days ago)
|
|
CVE-2024-20498 |
Description:
Multiple vulnerabilities in the Cisco AnyConnect VPN server of Cisco Meraki MX and Cisco Meraki Z Series Teleworker Gateway devices could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition to the AnyConnect VPN service on an affected device.
For more information about these vulnerabilities, see the Details section of this advisory.
Cisco Meraki has released software updates that address these vulnerabilities. There are no workarounds that address these vulnerabilities.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-meraki-mx-vpn-dos-QTRHzG2
Security Impact Rating: High
CVE: CVE-2024-20498,CVE-2024-20499,CVE-2024-20500,CVE-2024-20501,CVE-2024-20502,CVE-2024-20513
CVSS: HIGH (8.6) EPSS Score: 0.04%
June 2nd, 2025 (5 days ago)
|

|
Description: Technical details about a maximum-severity Cisco IOS XE WLC arbitrary file upload flaw tracked as CVE-2025-20188 have been made publicly available, bringing us closer to a working exploit. [...]
CVSS: CRITICAL (10.0) EPSS Score: 3.8%
May 31st, 2025 (7 days ago)
|

|
Description: [AI generated] Founded in 1868, sfhumanesociety.org is associated with the San Francisco Society for the Prevention of Cruelty to Animals (SFSPCA). As one of the world's pioneer animal welfare organizations, its mission is to save and protect animals, provide care and treatment, advocate for their welfare, and enhance the human-animal bond. It offers services including animal adoption, veterinary care, and community education.
May 30th, 2025 (8 days ago)
|
|
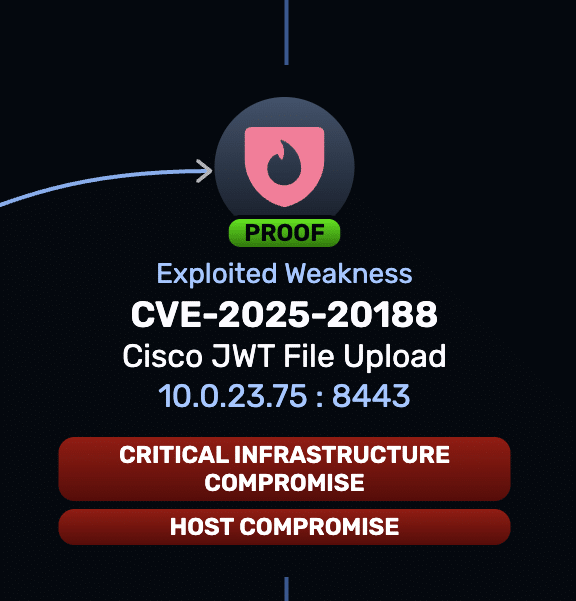
Description: Explore how a hard-coded JWT in Cisco IOS XE WLC enables unauthenticated file upload and potential RCE—and how to mitigate it.
CVSS: CRITICAL (10.0) EPSS Score: 3.8%
May 30th, 2025 (8 days ago)
|
|
Description: Cisco IOS XE Wireless Controller Software Arbitrary File Upload Vulnerability
CVSS: CRITICAL (10.0) EPSS Score: 3.8%
May 30th, 2025 (8 days ago)
|

|
Description: Cisco Talos has uncovered a destructive malware dubbed Numero, a Windows-targeting threat that disguises itself as a legitimate AI video tool installer but ultimately renders victims’ systems unusable. Alongside Numero, Talos also discovered two ransomware families, CyberLock and Lucky_Gh0$t, spreading under the guise of AI software, all part of a rising wave of cyberattacks exploiting …
The post New Malware “Numero” Masquerading as AI Tool Wrecks Windows Systems appeared first on CyberInsider.
May 30th, 2025 (8 days ago)
|

|
Description: Fake installers for popular artificial intelligence (AI) tools like OpenAI ChatGPT and InVideo AI are being used as lures to propagate various threats, such as the CyberLock and Lucky_Gh0$t ransomware families, and a new malware dubbed Numero.
"CyberLock ransomware, developed using PowerShell, primarily focuses on encrypting specific files on the victim's system," Cisco Talos researcher Chetan
May 29th, 2025 (9 days ago)
|
|
CVE-2024-20253 |
Description: A vulnerability in multiple Cisco Unified Communications and Contact Center Solutions products could allow an unauthenticated, remote attacker to execute arbitrary code on an affected device. This vulnerability is due to the improper processing of user-provided data that is being read into memory. An attacker could exploit this vulnerability by sending a crafted message to a listening port of an affected device. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system with the privileges of the web services user. With access to the underlying operating system, the attacker could also establish root access on the affected device.
CVSS: CRITICAL (9.9) EPSS Score: 1.17% SSVC Exploitation: none
May 29th, 2025 (9 days ago)
|
