CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Homeyer Consulting Services, Inc. is a global water consulting fi
rm. We have a multimillion dollar laboratory dedicated to testing
treated water, and a structured team of field consultants who co
nsult to over 6,800 sites worldwide.
We are going to upload about 169 GB of corporate data. There are
a lot of employee personal documents (passport scans of each empl
oyee), lots of confidential contracts, agreements correspondence,
detailed financial data (audits, payment details, reports), clie
nts data, NDAs, etc.
June 6th, 2025 (22 days ago)
|

|
Description: [AI generated] Synopsys is a leading company in electronic design automation (EDA) and semiconductor IP. It also provides software integrity tools. Founded in 1986 and headquartered in Mountain View, California, Synopsys offers innovative solutions that help designers manage complexity, develop high-quality, and high-performance silicon, meet critical time to market and power consumption requirements, and avoid costly redesigns.
June 6th, 2025 (22 days ago)
|
|
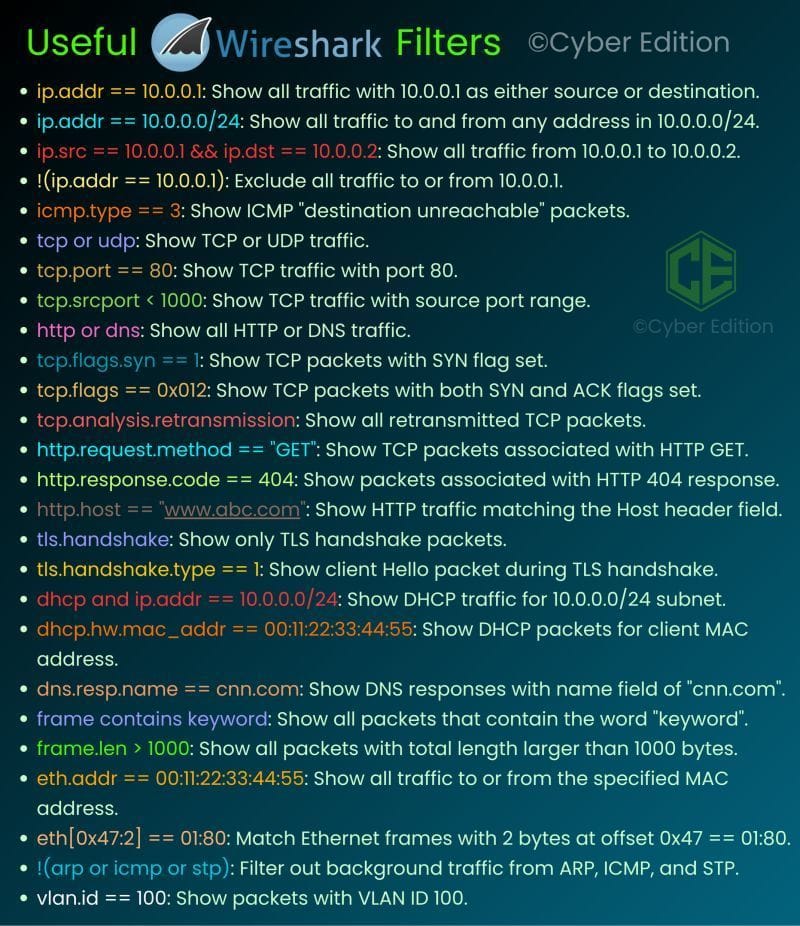
Description: Wireshark Filters
June 6th, 2025 (22 days ago)
|
|
CVE-2025-5783 |
Description: A vulnerability, which was classified as critical, was found in PHPGurukul Employee Record Management System 1.3. This affects an unknown part of the file /editmyexp.php. The manipulation of the argument emp3workduration leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. Es wurde eine kritische Schwachstelle in PHPGurukul Employee Record Management System 1.3 gefunden. Hiervon betroffen ist ein unbekannter Codeblock der Datei /editmyexp.php. Durch das Beeinflussen des Arguments emp3workduration mit unbekannten Daten kann eine sql injection-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk angegangen werden. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (6.3) EPSS Score: 0.04% SSVC Exploitation: poc
June 6th, 2025 (22 days ago)
|
|
CVE-2025-5782 |
Description: A vulnerability, which was classified as critical, has been found in PHPGurukul Employee Record Management System 1.3. Affected by this issue is some unknown functionality of the file /resetpassword.php. The manipulation of the argument newpassword leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. Eine kritische Schwachstelle wurde in PHPGurukul Employee Record Management System 1.3 entdeckt. Davon betroffen ist unbekannter Code der Datei /resetpassword.php. Durch Manipulieren des Arguments newpassword mit unbekannten Daten kann eine sql injection-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk erfolgen. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (6.3) EPSS Score: 0.03% SSVC Exploitation: poc
June 6th, 2025 (22 days ago)
|
|
CVE-2025-5780 |
Description: A vulnerability was found in code-projects Patient Record Management System 1.0 and classified as critical. Affected by this issue is some unknown functionality of the file /view_dental.php. The manipulation of the argument itr_no leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. Eine Schwachstelle wurde in code-projects Patient Record Management System 1.0 gefunden. Sie wurde als kritisch eingestuft. Hierbei geht es um eine nicht exakt ausgemachte Funktion der Datei /view_dental.php. Mit der Manipulation des Arguments itr_no mit unbekannten Daten kann eine sql injection-Schwachstelle ausgenutzt werden. Umgesetzt werden kann der Angriff über das Netzwerk. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (6.3) EPSS Score: 0.03%
June 6th, 2025 (22 days ago)
|
|
CVE-2025-5751 |
Description: WOLFBOX Level 2 EV Charger Management Card Hard-coded Credentials Authentication Bypass Vulnerability. This vulnerability allows physically present attackers to bypass authentication on affected installations of WOLFBOX Level 2 EV Charger. Authentication is not required to exploit this vulnerability.
The specific flaw exists within the handling of management cards. The issue results from the lack of personalization of management cards. An attacker can leverage this vulnerability to bypass authentication on the system. Was ZDI-CAN-26292.
CVSS: MEDIUM (4.6) EPSS Score: 0.03% SSVC Exploitation: none
June 6th, 2025 (22 days ago)
|
|
CVE-2025-5750 |
Description: WOLFBOX Level 2 EV Charger tuya_svc_devos_activate_result_parse Heap-based Buffer Overflow Remote Code Execution Vulnerability. This vulnerability allows network-adjacent attackers to execute arbitrary code on affected installations of WOLFBOX Level 2 EV Charger. Authentication is not required to exploit this vulnerability.
The specific flaw exists within the handling of the secKey, localKey, stdTimeZone and devId parameters. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length heap-based buffer. An attacker can leverage this vulnerability to execute code in the context of the device. Was ZDI-CAN-26294.
CVSS: HIGH (8.8) EPSS Score: 0.09% SSVC Exploitation: none
June 6th, 2025 (22 days ago)
|
|
CVE-2025-5749 |
Description: WOLFBOX Level 2 EV Charger BLE Encryption Keys Uninitialized Variable Authentication Bypass Vulnerability. This vulnerability allows network-adjacent attackers to bypass authentication on affected installations of WOLFBOX Level 2 EV Charger devices. Authentication is not required to exploit this vulnerability.
The specific flaw exists within the handling of cryptographic keys used in vendor-specific encrypted communications. The issue results from the lack of proper initialization of a variable prior to accessing it. An attacker can leverage this vulnerability to bypass authentication on the system. Was ZDI-CAN-26295.
CVSS: MEDIUM (6.3) EPSS Score: 0.02% SSVC Exploitation: none
June 6th, 2025 (22 days ago)
|
|
CVE-2025-5748 |
Description: WOLFBOX Level 2 EV Charger LAN OTA Exposed Dangerous Method Remote Code Execution Vulnerability. This vulnerability allows network-adjacent attackers to execute arbitrary code on affected installations of WOLFBOX Level 2 EV Charger. Although authentication is required to exploit this vulnerability, the existing authentication mechanism can be bypassed.
The specific flaw exists within the Tuya communications module software. The issue results from the exposure of a method allowing the upload of crafted software images to the module. An attacker can leverage this vulnerability to execute code in the context of the device. Was ZDI-CAN-26349.
CVSS: HIGH (8.0) EPSS Score: 0.16% SSVC Exploitation: none
June 6th, 2025 (22 days ago)
|
