CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: MTT Expertises is a Franco-Moroccan firm specializing in asset valuation and post-incident expertise. Founded in 2004, the company offers services such as insurance capital estimation, risk management, and assistance after incidents. With a multidisciplinary team of over 40 professionals, including engineers, technicians, and financial experts, MTT Expertises operates from offices in Casablanca, Agadir, and Tangier, and maintains a presence in France and other African countries. The firm is accredited by the Moroccan Federation of Insurance and Reinsurance Companies (FMSAR), ensuring quality and reliability in its services. Under the leadership of Director Mohamed Tahiri, MTT Expertises is committed to delivering precise and professional services to meet the diverse needs of its clients.
June 6th, 2025 (22 days ago)
|

|
Description: U.S. tax resolution firm Optima Tax Relief suffered a Chaos ransomware attack, with the threat actors now leaking data stolen from the company. [...]
June 6th, 2025 (22 days ago)
|

|
Description: Town of Kittery, Maine falls victim to INC RANSOM Ransomware
June 6th, 2025 (22 days ago)
|

|
Description: Country: USA
Views: 161
June 6th, 2025 (22 days ago)
|

|
Description: Farmacisti Più Rinaldi S.p.A. disctributes homeopathic products,
herbal products, veterinary products, phytotherapeutic products,
chemical substances and substances of plant origin including thos
e of non-pharmaceutical use, medical and surgical devices, biocid
es, medical devices, sanitary and hygienic items.
We are going to upload about 15 GB of corporate data. There are a
lot of employee personal documents, lots of contracts and agreem
ents, detailed financial data (audits, payment details, reports),
clients data, NDAs, etc.
June 6th, 2025 (22 days ago)
|

|
Description: Homeyer Consulting Services, Inc. is a global water consulting fi
rm. We have a multimillion dollar laboratory dedicated to testing
treated water, and a structured team of field consultants who co
nsult to over 6,800 sites worldwide.
We are going to upload about 169 GB of corporate data. There are
a lot of employee personal documents (passport scans of each empl
oyee), lots of confidential contracts, agreements correspondence,
detailed financial data (audits, payment details, reports), clie
nts data, NDAs, etc.
June 6th, 2025 (22 days ago)
|

|
Description: [AI generated] Synopsys is a leading company in electronic design automation (EDA) and semiconductor IP. It also provides software integrity tools. Founded in 1986 and headquartered in Mountain View, California, Synopsys offers innovative solutions that help designers manage complexity, develop high-quality, and high-performance silicon, meet critical time to market and power consumption requirements, and avoid costly redesigns.
June 6th, 2025 (22 days ago)
|
|
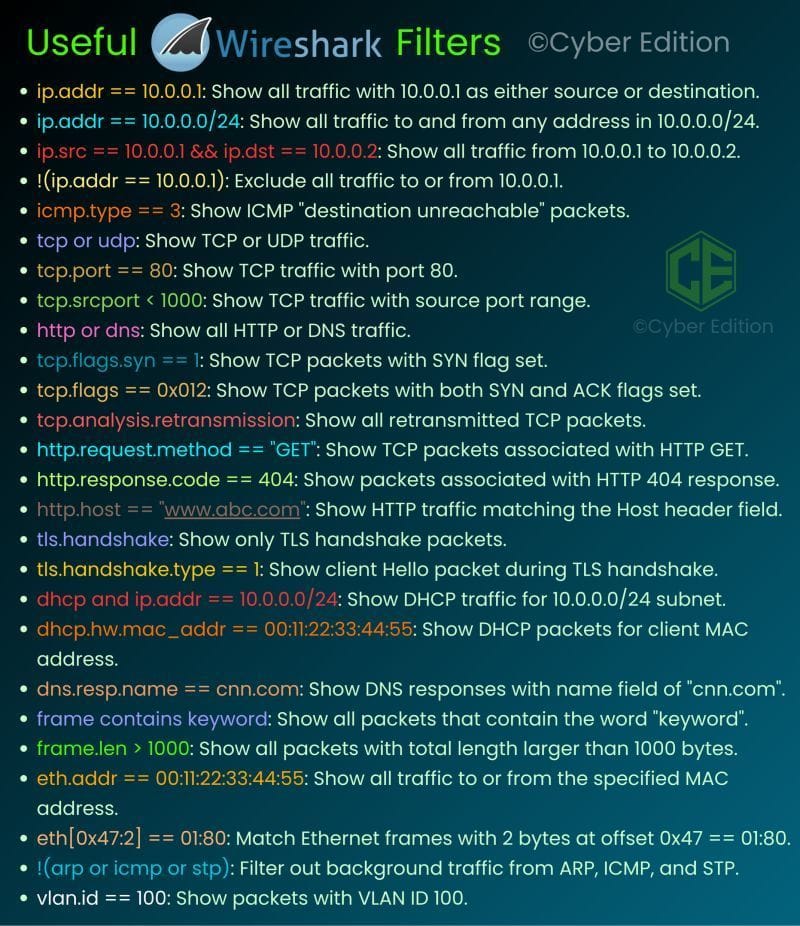
Description: Wireshark Filters
June 6th, 2025 (22 days ago)
|
|
CVE-2025-5783 |
Description: A vulnerability, which was classified as critical, was found in PHPGurukul Employee Record Management System 1.3. This affects an unknown part of the file /editmyexp.php. The manipulation of the argument emp3workduration leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. Es wurde eine kritische Schwachstelle in PHPGurukul Employee Record Management System 1.3 gefunden. Hiervon betroffen ist ein unbekannter Codeblock der Datei /editmyexp.php. Durch das Beeinflussen des Arguments emp3workduration mit unbekannten Daten kann eine sql injection-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk angegangen werden. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (6.3) EPSS Score: 0.04% SSVC Exploitation: poc
June 6th, 2025 (22 days ago)
|
|
CVE-2025-5782 |
Description: A vulnerability, which was classified as critical, has been found in PHPGurukul Employee Record Management System 1.3. Affected by this issue is some unknown functionality of the file /resetpassword.php. The manipulation of the argument newpassword leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. Eine kritische Schwachstelle wurde in PHPGurukul Employee Record Management System 1.3 entdeckt. Davon betroffen ist unbekannter Code der Datei /resetpassword.php. Durch Manipulieren des Arguments newpassword mit unbekannten Daten kann eine sql injection-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk erfolgen. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (6.3) EPSS Score: 0.03% SSVC Exploitation: poc
June 6th, 2025 (22 days ago)
|
