CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-49008 |
Description: Atheos is a self-hosted browser-based cloud integrated development environment. Prior to version 6.0.4, improper use of `escapeshellcmd()` in `/components/codegit/traits/execute.php` allows argument injection, leading to arbitrary command execution. Atheos administrators and users of vulnerable versions are at risk of data breaches or server compromise. Version 6.0.4 introduces a `Common::safe_execute` function that sanitizes all arguments using `escapeshellarg()` prior to execution and migrated all components potentially vulnerable to similar exploits to use this new templated execution system.
CVSS: CRITICAL (9.4) EPSS Score: 0.1%
June 5th, 2025 (8 days ago)
|

|
Description: In an update to a joint advisory with CISA and the Australian Cyber Security Centre, the FBI said that the Play ransomware gang had breached roughly 900 organizations as of May 2025, three times the number of victims reported in October 2023. [...]
June 4th, 2025 (9 days ago)
|

|
Description: The Ukrainian police arrested a 35-year-old hacker who breached 5,000 accounts at an international hosting company and used them to mine cryptocurrency, resulting in $4.5 million in damages. [...]
June 4th, 2025 (9 days ago)
|

|
Description: Nearly four months after a ransomware attack paralyzed Lee Enterprises’ nationwide newspaper operations, the company has confirmed the breach also compromised sensitive personal data of 39,779 individuals. According to a filing with the Maine Attorney General’s Office, the attackers gained unauthorized access to Lee's systems as early as February 1, 2025, exfiltrating personal data during …
The post Ransomware Attack at Lee Enterprises Impacted Nearly 40,000 Individuals appeared first on CyberInsider.
June 4th, 2025 (9 days ago)
|

|
Description: Google has disclosed details of a financially motivated threat cluster that it said "specialises" in voice phishing (aka vishing) campaigns designed to breach organizations' Salesforce instances for large-scale data theft and subsequent extortion.
The tech giant's threat intelligence team is tracking the activity under the moniker UNC6040, which it said exhibits characteristics that align with
June 4th, 2025 (9 days ago)
|
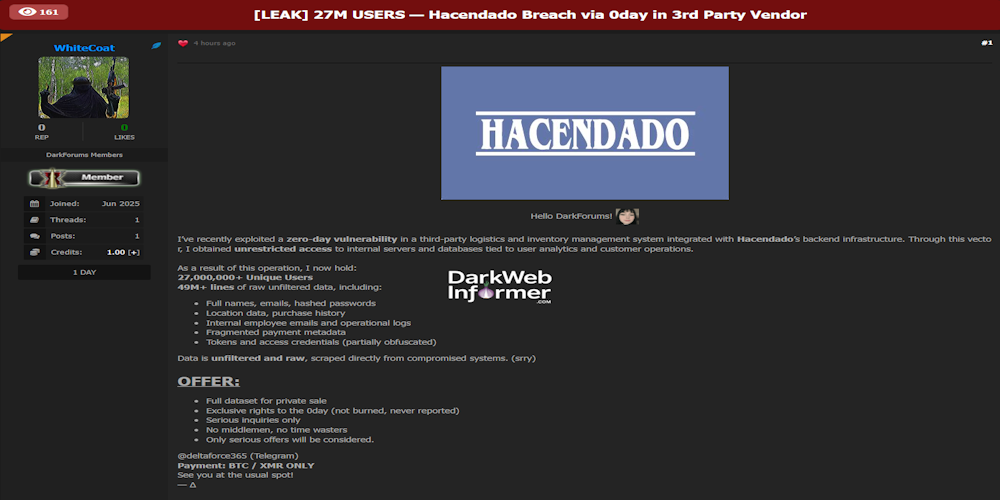
|
Description: Alleged breach of Hacendado via 0-day in third-party vendor – 27M User Records Exposed
June 4th, 2025 (9 days ago)
|

|
Description: Introduction
Google Threat Intelligence Group (GTIG) is tracking UNC6040, a financially motivated threat cluster that specializes in voice phishing (vishing) campaigns specifically designed to compromise organization’s Salesforce instances for large-scale data theft and subsequent extortion. Over the past several months, UNC6040 has demonstrated repeated success in breaching networks by having its operators impersonate IT support personnel in convincing telephone-based social engineering engagements. This approach has proven particularly effective in tricking employees, often within English-speaking branches of multinational corporations, into actions that grant the attackers access or lead to the sharing of sensitive credentials, ultimately facilitating the theft of organization’s Salesforce data. In all observed cases, attackers relied on manipulating end users, not exploiting any vulnerability inherent to Salesforce.
A prevalent tactic in UNC6040's operations involves deceiving victims into authorizing a malicious connected app to their organization's Salesforce portal. This application is often a modified version of Salesforce’s Data Loader, not authorized by Salesforce. During a vishing call, the actor guides the victim to visit Salesforce's connected app setup page to approve a version of the Data Loader app with a name or branding that differs from the legitimate version. This step inadvertently grants UNC6040 significant capabilities to access, query, and exfiltrat...
June 4th, 2025 (9 days ago)
|
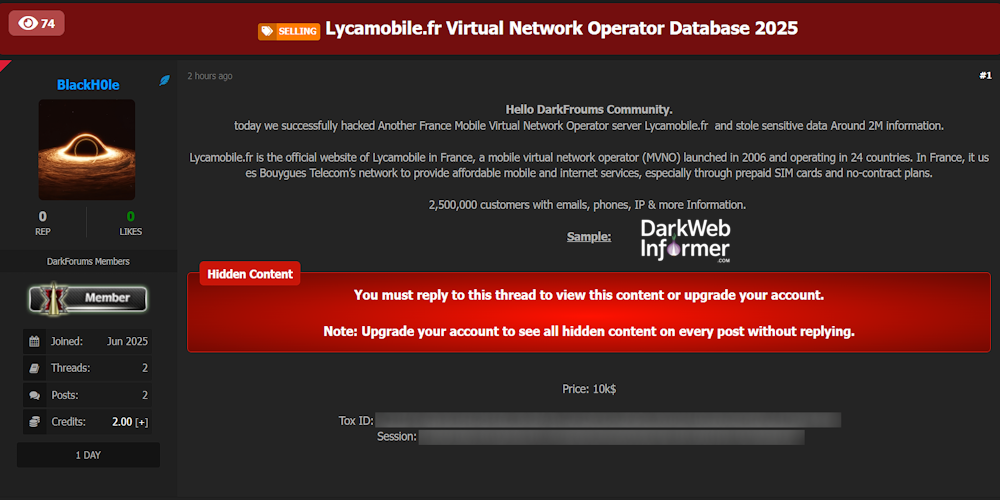
|
Description: Alleged data breach of Lyca Mobile France – 2.5 Million Customer Records for Sale
June 4th, 2025 (9 days ago)
|

|
Description: Publishing giant Lee Enterprises is notifying over 39,000 people whose personal information was stolen in a February 2025 ransomware attack. [...]
June 4th, 2025 (9 days ago)
|

|
Description: The parent company of apparel brand The North Face sent data breach notification letters to about 3,000 customer accounts, saying attackers used the technique known as credential stuffing.
June 4th, 2025 (9 days ago)
|
