CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Erie Insurance has reported a cybersecurity incident involving unusual network activity discovered on June 7, 2025. The company is now working with federal law enforcement and external cybersecurity firms to investigate and contain the breach. The disclosure was made in an 8-K filing with the U.S. Securities and Exchange Commission submitted yesterday. According to it, …
The post Erie Insurance Discloses Cybersecurity Incident, Forensic Investigation Underway appeared first on CyberInsider.
June 12th, 2025 (about 5 hours ago)
|

|
Description: Cybersecurity researchers have uncovered a new account takeover (ATO) campaign that leverages an open-source penetration testing framework called TeamFiltration to breach Microsoft Entra ID (formerly Azure Active Directory) user accounts.
The activity, codenamed UNK_SneakyStrike by Proofpoint, has affected over 80,000 targeted user accounts across hundreds of organizations' cloud tenants since a
June 12th, 2025 (about 9 hours ago)
|

|
Description: The Texas Department of Transportation (TxDOT) is warning that it suffered a data breach after a threat actor downloaded 300,000 crash records from its database. [...]
June 10th, 2025 (2 days ago)
|
|
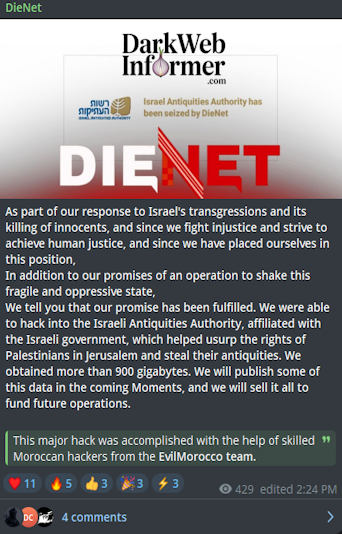
Description: Alleged Data Breach of Israeli Antiquities Authority
June 10th, 2025 (2 days ago)
|
|
Description: AI acts like Pac-Man—devouring sensitive data across clouds, apps, and copilots. Varonis analyzed 1,000 orgs and found 99% have exposed data AI can access, exposing them to data risks. [...]
June 10th, 2025 (2 days ago)
|

|
Description: In May 2022, the now defunct social media influencer platform WiredBucks suffered a data breach that was later redistributed as part of a larger corpus of data. The incident exposed over 900k email and IP addresses alongside names, usernames, earnings via the platform, physical addresses and passwords stored as plain text.
June 10th, 2025 (2 days ago)
|

|
Description: SentinelOne has shared more details on an attempted supply chain attack by Chinese hackers through an IT services and logistics firm that manages hardware logistics for the cybersecurity firm. [...]
June 9th, 2025 (3 days ago)
|
|
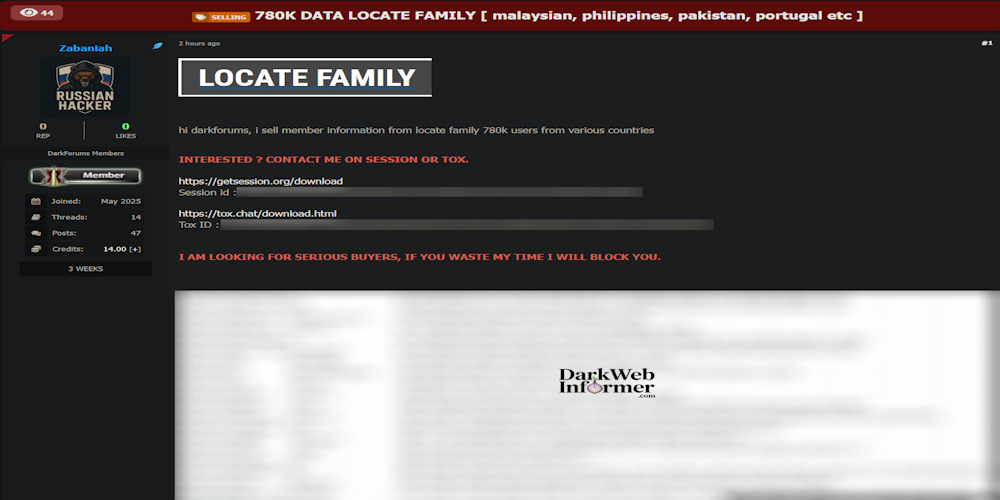
Description: Alleged Data Breach of Locate Family
June 9th, 2025 (3 days ago)
|

|
Description: Sensata Technologies is warning former and current employees it suffered a data breach after concluding an investigation into an April ransomware attack. [...]
June 9th, 2025 (3 days ago)
|

|
Description: Alleged data breach of IMS Consultores
June 9th, 2025 (3 days ago)
|
