CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: QSC Employee Database Allegedly Leaked on Breach Forums
April 8th, 2025 (2 months ago)
|

|
Description: With the just-In-time (JIT) access control method, privileges are granted temporarily on an as-needed basis. This reduces static entitlements, lowering the risk of compromised accounts and preventing privilege creep. In this blog, we’ll share how we implemented JIT access internally at Tenable using Tenable Cloud Security, and offer recommendations we hope you’ll find useful.Just-in-time access (JIT) is a valuable security practice that allows organizations to limit the time and the scope of users’ access to resources, such as applications and systems. However, implementing JIT access successfully is challenging, as it requires careful planning and ample communication between the security team and all other departments. At Tenable, we went through this process. Here, we share the lessons we learned and the best practices we adopted, as well as explain how you can leverage Tenable Cloud Security when implementing JIT access.Benefits of JIT accessThe most notable benefit of just-in-time (JIT) provisioning is its ability to restrict access duration. By granting permissions only upon request, JIT can reduce identity and entitlement risks by 75% or more in most scenarios. For example, a user who requests permissions for a 40-hour work week will not have access during the remaining 128 hours, thereby significantly minimizing the user’s identity-breach risks.Another significant risk reduction made possible by JIT is the prevention of privilege creep. Over time, users tend to accu...
April 8th, 2025 (2 months ago)
|

|
Description: EncryptHub, a notorious threat actor linked to breaches at 618 organizations, is believed to have reported two Windows zero-day vulnerabilities to Microsoft, revealing a conflicted figure straddling the line between cybercrime and security research. [...]
April 7th, 2025 (2 months ago)
|

|
Description: We have breached the internal systems of Guangzhou Shiyuan Electronic Technology, securing sensitive files that, if exposed, would cause serious disruption across operations and partnerships.
April 7th, 2025 (2 months ago)
|

|
Description: We have breached a U.S.-based financial services firm. 381GB of sensitive data has been secured. The name will be made public in a few hours. This is a warning.
April 7th, 2025 (2 months ago)
|
|
CVE-2024-6221 |
Description: A vulnerability in corydolphin/flask-cors version 4.0.1 allows the `Access-Control-Allow-Private-Network` CORS header to be set to true by default. This behavior can expose private network resources to unauthorized external access, leading to significant security risks such as data breaches, unauthorized access to sensitive information, and potential network intrusions.
CVSS: MEDIUM (6.5) EPSS Score: 0.03% SSVC Exploitation: poc
April 7th, 2025 (2 months ago)
|

|
Description: US food giant WK Kellogg Co is warning employees and vendors that company data was stolen during the 2024 Cleo data theft attacks. [...]
April 7th, 2025 (2 months ago)
|
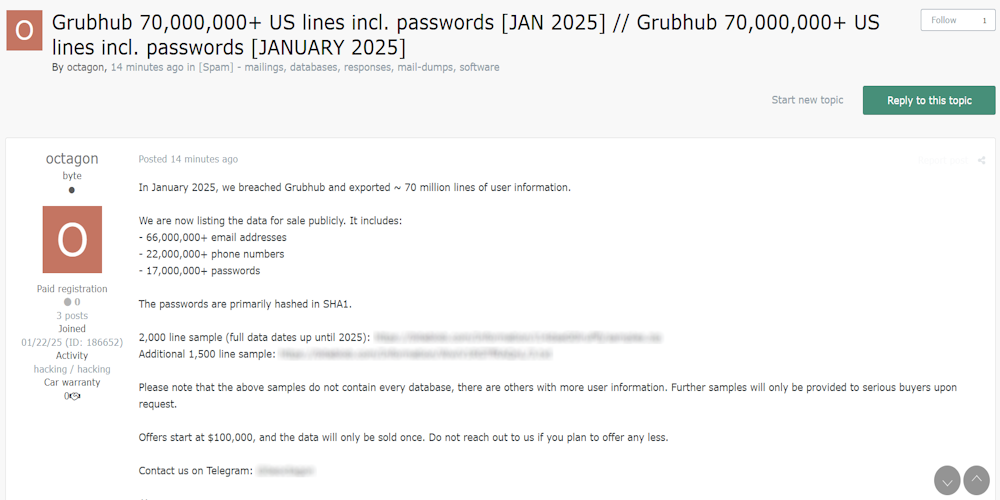
|
Description: Alleged Grubhub Data Breach Exposes 70 Million User Records
April 7th, 2025 (2 months ago)
|

|
Description: Each Monday, the Tenable Exposure Management Academy provides the practical, real-world guidance you need to shift from vulnerability management to exposure management. In this post, we explore the five steps to take on your journey to exposure management. You can read the entire Exposure Management Academy series here.Chances are, you’re buried in vulnerabilities and other cyber risks and there’s simply no way to address them all. But they keep on coming. You could work day and night and never hope to close them all. Of course, hope is not a strategy — especially with breaches like those that impacted SolarWinds and Colonial Pipeline, which cost millions to mitigate. And even after those companies cleaned up their issues, the damage was done — to their brands, to customer loyalty and to stakeholder confidence. So, faced with building threats, what can you do? In the cyber world, the key to getting ahead of your exposures is focus. That doesn’t mean trying to boil the ocean of threats you face. In fact, it might mean doing less. Pour that ocean into a paper cup. Economist Michael E. Porter wrote in a seminal Harvard Business Review article: "The essence of strategy is choosing what not to do." The upshot here: How can you be strategic if you have to do everything? Or, as the great philosopher Bob Seger once sang in “Against The Wind”: Deadlines and commitmentsWhat to leave in, what to leave outSo, what should you leave in and what should you leave out? Let’s think about it...
April 7th, 2025 (2 months ago)
|

|
Description: VF Outdoor, the parent company behind The North Face and Timberland, has disclosed a security breach that exposed personal information belonging to over 15,000 customers. The security breach began in March 2023 but was only discovered and remediated two years later, on March 13, 2025. The breach was uncovered after VF Outdoor noticed suspicious activity …
The post The North Face and Timberland Inform Customers of Two-Year-Long Breach appeared first on CyberInsider.
April 7th, 2025 (2 months ago)
|
