CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
Description: Alleged Data Breach of an Unidentified Job Portal in Argentina
May 23rd, 2025 (22 days ago)
|
|
Description: Alleged Data Breach of Herbies Seeds
May 23rd, 2025 (22 days ago)
|

|
Description: Chinese hackers have been exploiting a remote code execution flaw in Ivanti Endpoint Manager Mobile (EPMM) to breach high-profile organizations worldwide. [...]
May 22nd, 2025 (23 days ago)
|

|
Description: Chinese-speaking hackers have exploited a now-patched Trimble Cityworks zero-day to breach multiple local governing bodies across the United States. [...]
May 22nd, 2025 (23 days ago)
|
|
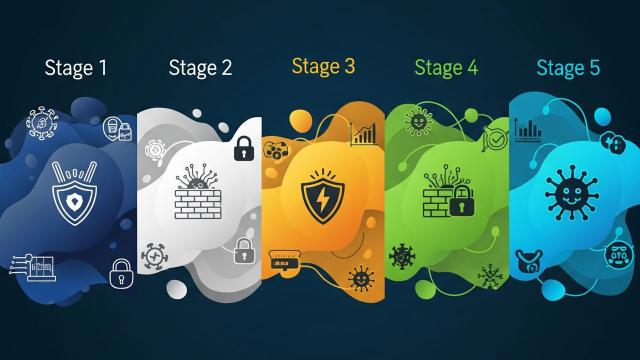
Description: While credential abuse is a primary initial access vector, identity compromise plays a key role in most stages of a cyber attack. Here’s what you need to know — and how Tenable can help.Identity compromise plays a pivotal role in how attackers move laterally through an organization. Credential abuse is the top initial access vector, implicated in 22% of breaches, according to the 2025 Verizon Data Breach Investigations Report, followed closely by vulnerability exploitation (20%). But identity compromise doesn’t stop after initial access. It plays a key role in five stages of a cyber attack.Understanding the following stages of an attack helps illuminate where identity becomes a threat vector:Initial accessReconnaissanceLateral movement and privilege escalationPersistence and detection evasionDeploymentBelow, we explore actions security teams can take to protect identities in each of these stages. While the guidance we share here is based on protecting on-premises Microsoft Active Directory environments, it’s worth considering how credential compromise can affect Microsoft Entra ID and hybrid identity infrastructure. We also discuss how Tenable Identity Exposure, available in the Tenable One Exposure Management Platform, can be used at each stage to provide security teams with valuable insights to help them proactively reduce their exposure to cyber attacks.Stage 1: Initial accessAttackers need a foothold and credential abuse enables them to get one. To prevent credentials ...
May 22nd, 2025 (23 days ago)
|

|
Description: The Federal Trade Commission (FTC) has finalized an order requiring web hosting giant GoDaddy to secure its services to settle charges of data security failures that led to several data breaches since 2018. [...]
May 22nd, 2025 (23 days ago)
|
|
Description: A Russian state-sponsored cyberespionage campaign attributed to APT28 (Fancy Bear/Forest Blizzard) hackers has been targeting and compromising international organizations since 2022 to disrupt aid efforts to Ukraine. [...]
May 21st, 2025 (24 days ago)
|

|
Description: A 3AM ransomware affiliate is conducting highly targeted attacks using email bombing and spoofed IT support calls to socially engineer employees into giving credentials for remote access to corporate systems. [...]
May 21st, 2025 (24 days ago)
|

|
Description: In documents filed with regulators in Maine on Tuesday, Coinbase said the information leaked included details like photos of passports and government IDs, as well as account information such as balances and transaction history.
May 21st, 2025 (24 days ago)
|

|
Description: It takes just one email to compromise an entire system. A single well-crafted message can bypass filters, trick employees, and give attackers the access they need. Left undetected, these threats can lead to credential theft, unauthorized access, and even full-scale breaches. As phishing techniques become more evasive, they can no longer be reliably caught by automated solutions alone.
Let’s take
May 21st, 2025 (24 days ago)
|
