Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Cisco has released security patches to address a critical security flaw impacting the Identity Services Engine (ISE) that, if successfully exploited, could allow unauthenticated actors to carry out malicious actions on susceptible systems.
The security defect, tracked as CVE-2025-20286, carries a CVSS score of 9.9 out of 10.0. It has been described as a static credential vulnerability.
"A
CVSS: CRITICAL (9.9)
June 5th, 2025 (about 20 hours ago)
|
|
CVE-2025-20286 |
Description: A vulnerability in Amazon Web Services (AWS), Microsoft Azure, and Oracle Cloud Infrastructure (OCI) cloud deployments of Cisco Identity Services Engine (ISE) could allow an unauthenticated, remote attacker to access sensitive data, execute limited administrative operations, modify system configurations, or disrupt services within the impacted systems.
This vulnerability exists because credentials are improperly generated when Cisco ISE is being deployed on cloud platforms, resulting in different Cisco ISE deployments sharing the same credentials. These credentials are shared across multiple Cisco ISE deployments as long as the software release and cloud platform are the same. An attacker could exploit this vulnerability by extracting the user credentials from Cisco ISE that is deployed in the cloud and then using them to access Cisco ISE that is deployed in other cloud environments through unsecured ports. A successful exploit could allow the attacker to access sensitive data, execute limited administrative operations, modify system configurations, or disrupt services within the impacted systems.
Note: If the Primary Administration node is deployed in the cloud, then Cisco ISE is affected by this vulnerability. If the Primary Administration node is on-premises, then it is not affected.
CVSS: CRITICAL (9.9)
June 4th, 2025 (1 day ago)
|

|
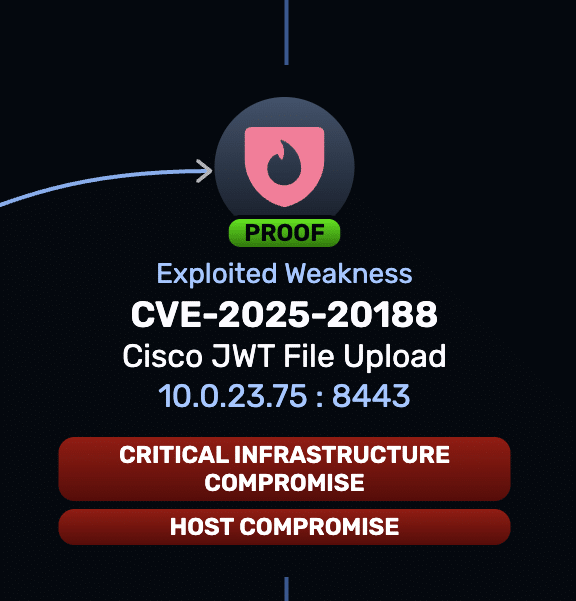
Description: Technical details about a maximum-severity Cisco IOS XE WLC arbitrary file upload flaw tracked as CVE-2025-20188 have been made publicly available, bringing us closer to a working exploit. [...]
CVSS: CRITICAL (10.0) EPSS Score: 5.82%
May 31st, 2025 (5 days ago)
|
|
Description: Explore how a hard-coded JWT in Cisco IOS XE WLC enables unauthenticated file upload and potential RCE—and how to mitigate it.
CVSS: CRITICAL (10.0) EPSS Score: 5.82%
May 30th, 2025 (6 days ago)
|
|
Description: Cisco IOS XE Wireless Controller Software Arbitrary File Upload Vulnerability
CVSS: CRITICAL (10.0) EPSS Score: 5.82%
May 30th, 2025 (6 days ago)
|
|
CVE-2024-20253 |
Description: A vulnerability in multiple Cisco Unified Communications and Contact Center Solutions products could allow an unauthenticated, remote attacker to execute arbitrary code on an affected device. This vulnerability is due to the improper processing of user-provided data that is being read into memory. An attacker could exploit this vulnerability by sending a crafted message to a listening port of an affected device. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system with the privileges of the web services user. With access to the underlying operating system, the attacker could also establish root access on the affected device.
CVSS: CRITICAL (9.9) EPSS Score: 1.17% SSVC Exploitation: none
May 29th, 2025 (7 days ago)
|

|
Description: Cisco IOS XE Wireless Controllers Vulnerable to Unauthenticated Root Exploits via JWT (CVE-2025-20188)
CVSS: CRITICAL (10.0) EPSS Score: 5.82%
May 8th, 2025 (28 days ago)
|

|
Description: Cisco has released software fixes to address a maximum-severity security flaw in its IOS XE Wireless Controller that could enable an unauthenticated, remote attacker to upload arbitrary files to a susceptible system.
The vulnerability, tracked as CVE-2025-20188, has been rated 10.0 on the CVSS scoring system.
"This vulnerability is due to the presence of a hard-coded JSON Web Token (JWT) on an
CVSS: CRITICAL (10.0) EPSS Score: 5.82%
May 8th, 2025 (29 days ago)
|
|
CVE-2025-20188 |
Description: A vulnerability in the Out-of-Band Access Point (AP) Image Download feature of Cisco IOS XE Software for Wireless LAN Controllers (WLCs) could allow an unauthenticated, remote attacker to upload arbitrary files to an affected system.
This vulnerability is due to the presence of a hard-coded JSON Web Token (JWT) on an affected system. An attacker could exploit this vulnerability by sending crafted HTTPS requests to the AP image download interface. A successful exploit could allow the attacker to upload files, perform path traversal, and execute arbitrary commands with root privileges.
Note: For exploitation to be successful, the Out-of-Band AP Image Download feature must be enabled on the device. It is not enabled by default.
CVSS: CRITICAL (10.0) EPSS Score: 5.82%
May 7th, 2025 (29 days ago)
|
|
CVE-2025-32433 |
Description:
On April 16, 2025, a critical vulnerability in the Erlang/OTP SSH server was disclosed. This vulnerability could allow an unauthenticated, remote attacker to perform remote code execution (RCE) on an affected device.
The vulnerability is due to a flaw in the handling of SSH messages during the authentication phase.
For a description of this vulnerability, see the Erlang announcement.
This advisory will be updated as additional information becomes available.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-erlang-otp-ssh-xyZZy
Security Impact Rating: Critical
CVE: CVE-2025-32433
CVSS: CRITICAL (10.0) EPSS Score: 37.73%
April 23rd, 2025 (about 1 month ago)
|
