Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-49113 |
🚨 Marked as known exploited on June 5th, 2025 (1 day ago).
Description: Roundcube Webmail before 1.5.10 and 1.6.x before 1.6.11 allows remote code execution by authenticated users because the _from parameter in a URL is not validated in program/actions/settings/upload.php, leading to PHP Object Deserialization.
CVSS: CRITICAL (9.9) EPSS Score: 0.66%
June 2nd, 2025 (5 days ago)
|
|
CVE-2025-20674 |
Description: In wlan AP driver, there is a possible way to inject arbitrary packet due to a missing permission check. This could lead to remote escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation. Patch ID: WCNCR00413202; Issue ID: MSV-3303.
CVSS: CRITICAL (9.8) EPSS Score: 0.15%
June 2nd, 2025 (5 days ago)
|
|
CVE-2025-20672 |
Description: In Bluetooth driver, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with User execution privileges needed. User interaction is not needed for exploitation. Patch ID: WCNCR00412257; Issue ID: MSV-3292.
CVSS: CRITICAL (9.8) EPSS Score: 0.07%
June 2nd, 2025 (5 days ago)
|
|
CVE-2025-5408 |
Description: A vulnerability was found in WAVLINK QUANTUM D2G, QUANTUM D3G, WL-WN530G3A, WL-WN530HG3, WL-WN532A3 and WL-WN576K1 up to V1410_240222 and classified as critical. Affected by this issue is the function sys_login of the file /cgi-bin/login.cgi of the component HTTP POST Request Handler. The manipulation of the argument login_page leads to buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way. Eine Schwachstelle wurde in WAVLINK QUANTUM D2G, QUANTUM D3G, WL-WN530G3A, WL-WN530HG3, WL-WN532A3 and WL-WN576K1 bis V1410_240222 gefunden. Sie wurde als kritisch eingestuft. Betroffen davon ist die Funktion sys_login der Datei /cgi-bin/login.cgi der Komponente HTTP POST Request Handler. Durch das Beeinflussen des Arguments login_page mit unbekannten Daten kann eine buffer overflow-Schwachstelle ausgenutzt werden. Die Umsetzung des Angriffs kann dabei über das Netzwerk erfolgen. Der Exploit steht zur öffentlichen Verfügung.
CVSS: CRITICAL (9.8) EPSS Score: 0.04%
June 1st, 2025 (5 days ago)
|
|
CVE-2025-40908 |
Description: YAML-LibYAML prior to 0.903.0 for Perl uses 2-args open, allowing existing files to be modified
CVSS: CRITICAL (9.1) EPSS Score: 0.03%
June 1st, 2025 (5 days ago)
|

|
Description: Technical details about a maximum-severity Cisco IOS XE WLC arbitrary file upload flaw tracked as CVE-2025-20188 have been made publicly available, bringing us closer to a working exploit. [...]
CVSS: CRITICAL (10.0) EPSS Score: 3.8%
May 31st, 2025 (6 days ago)
|
|
CVE-2025-4631 |
Description: The Profitori plugin for WordPress is vulnerable to Privilege Escalation due to a missing capability check on the stocktend_object endpoint in versions 2.0.6.0 to 2.1.1.3. This makes it possible to trigger the save_object_as_user() function for objects whose '_datatype' is set to 'users',. This allows unauthenticated attackers to write arbitrary strings straight into the user’s wp_capabilities meta field, potentially elevating the privileges of an existing user account or a newly created one to that of an administrator.
CVSS: CRITICAL (9.8) EPSS Score: 0.09%
May 31st, 2025 (6 days ago)
|
|
CVE-2025-4607 |
Description: The PSW Front-end Login & Registration plugin for WordPress is vulnerable to Privilege Escalation in all versions up to, and including, 1.12 via the customer_registration() function. This is due to the use of a weak, low-entropy OTP mechanism in the forget() function. This makes it possible for unauthenticated attackers to initiate a password reset for any user, including administrators, and elevate their privileges for full site takeover.
CVSS: CRITICAL (9.8) EPSS Score: 0.08%
May 31st, 2025 (6 days ago)
|
|
CVE-2024-24332 |
Description: TOTOLINK A3300R V17.0.0cu.557_B20221024 was discovered to contain a command injection vulnerability via the url parameter in the setUrlFilterRules function.
CVSS: CRITICAL (9.8) EPSS Score: 2.04% SSVC Exploitation: poc
May 30th, 2025 (7 days ago)
|
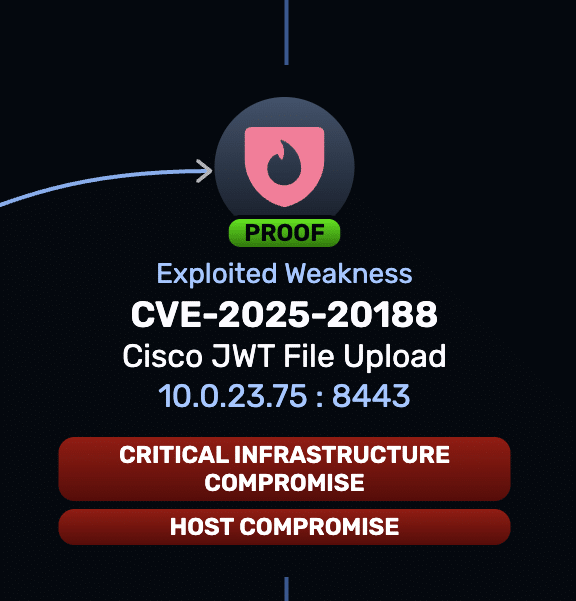
|
Description: Explore how a hard-coded JWT in Cisco IOS XE WLC enables unauthenticated file upload and potential RCE—and how to mitigate it.
CVSS: CRITICAL (10.0) EPSS Score: 3.8%
May 30th, 2025 (7 days ago)
|
