CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
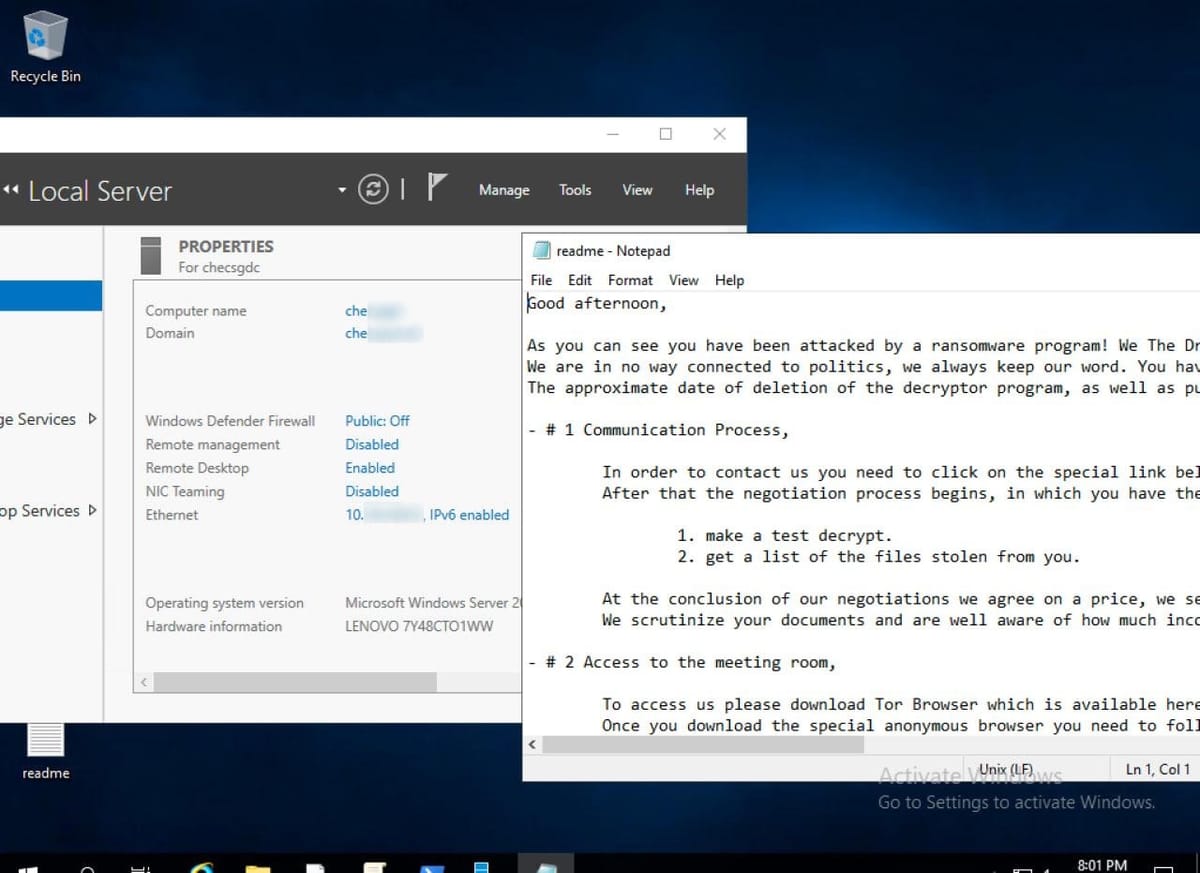
Description: Alleged Ransomware Attack and Data Leak Targeting China Harbour Engineering Company
April 20th, 2025 (about 2 months ago)
|

|
Description: 450k USD
April 20th, 2025 (about 2 months ago)
|

|
Description: A new report from iVerify has revealed a far-reaching global surveillance threat enabled by China’s state-owned telecom interconnect providers. By exploiting outdated mobile signaling protocols, entities such as China Mobile International (CMI) and China Telecom Global have gained alarming access to sensitive mobile communications worldwide, with implications ranging from mass user profiling to covert malware …
The post Global Telecom Networks Host Hidden Chinese Surveillance Nodes appeared first on CyberInsider.
April 17th, 2025 (about 2 months ago)
|
|
CVE-2025-22771 |
Description: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Studio Hyperset The Great Firewords of China allows Stored XSS. This issue affects The Great Firewords of China: from n/a through 1.2.
CVSS: MEDIUM (6.5) EPSS Score: 0.03% SSVC Exploitation: none
April 17th, 2025 (about 2 months ago)
|

|
Description: The China-linked threat actor known as Mustang Panda has been attributed to a cyber attack targeting an unspecified organization in Myanmar with previously unreported tooling, highlighting continued effort by the threat actors to increase the sophistication and effectiveness of their malware.
This includes updated versions of a known backdoor called TONESHELL, as well as a new lateral movement
April 17th, 2025 (about 2 months ago)
|

|
Description: Explore how Iran is leveraging AI for cyberwarfare, influence ops, military tech, and domestic surveillance. A deep dive into Tehran’s top-down AI strategy, partnerships with China and Russia, and implications for global security.
April 17th, 2025 (about 2 months ago)
|

|
Description: Researchers discovered new variants of the malware, which is tied to a China-nexus threat group, targeting Windows environments of critical infrastructure networks in Europe.
April 16th, 2025 (about 2 months ago)
|

|
Description: China on Tuesday accused three alleged employees of the U.S. National Security Agency of carrying out cyberattacks on the Asian Winter Games in February.
April 15th, 2025 (about 2 months ago)
|

|
April 15th, 2025 (about 2 months ago)
|

|
Description: The China-linked threat actor known as UNC5174 has been attributed to a new campaign that leverages a variant of a known malware dubbed SNOWLIGHT and a new open-source tool called VShell to infect Linux systems.
"Threat actors are increasingly using open source tools in their arsenals for cost-effectiveness and obfuscation to save money and, in this case, plausibly blend in with the pool of
April 15th, 2025 (about 2 months ago)
|
