CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: In its latest campaign this spring, DarkGaboon was observed deploying LockBit 3.0 ransomware against victims in Russia, Positive Technologies said in a report last week.
June 9th, 2025 (about 1 month ago)
|

|
Description: Impact
The application is vulnerable to Cross-Site Scripting (XSS) attacks due to incorrect input validation and sanitization of user-input data. An attacker can inject arbitrary HTML code, including JavaScript scripts, into the page processed by the user's browser, allowing them to steal sensitive data, hijack user sessions, or conduct other malicious activities.
Patches
The issue is fixed in https://github.com/barryvdh/laravel-translation-manager/pull/475 which is released in version 0.6.8
Workarounds
Only authenticated users with access to the translation manager are impacted.
References
[PT-2025-04] laravel translation manager.pdf
Reported by
Positive Technologies (Artem Deikov, Ilya Tsaturov, Daniil Satyaev, Roman Cheremnykh, Artem Danilov, Stanislav Gleym)
References
https://github.com/barryvdh/laravel-translation-manager/security/advisories/GHSA-j226-63j7-qrqh
https://github.com/barryvdh/laravel-translation-manager/pull/475
https://github.com/barryvdh/laravel-translation-manager/commit/527446ed419f90f2319675fc5211cb8f851d7a1f
https://github.com/barryvdh/laravel-translation-manager/releases/tag/v0.6.8
https://github.com/advisories/GHSA-j226-63j7-qrqh
June 9th, 2025 (about 1 month ago)
|

|
Description: Phone numbers are a goldmine for SIM swappers. A researcher found how to get this precious piece of information from any Google account.
June 9th, 2025 (about 1 month ago)
|

|
Description: United Natural Foods (UNFI), North America's largest publicly traded wholesale distributor, was forced to shut down some systems following a recent cyberattack. [...]
June 9th, 2025 (about 1 month ago)
|
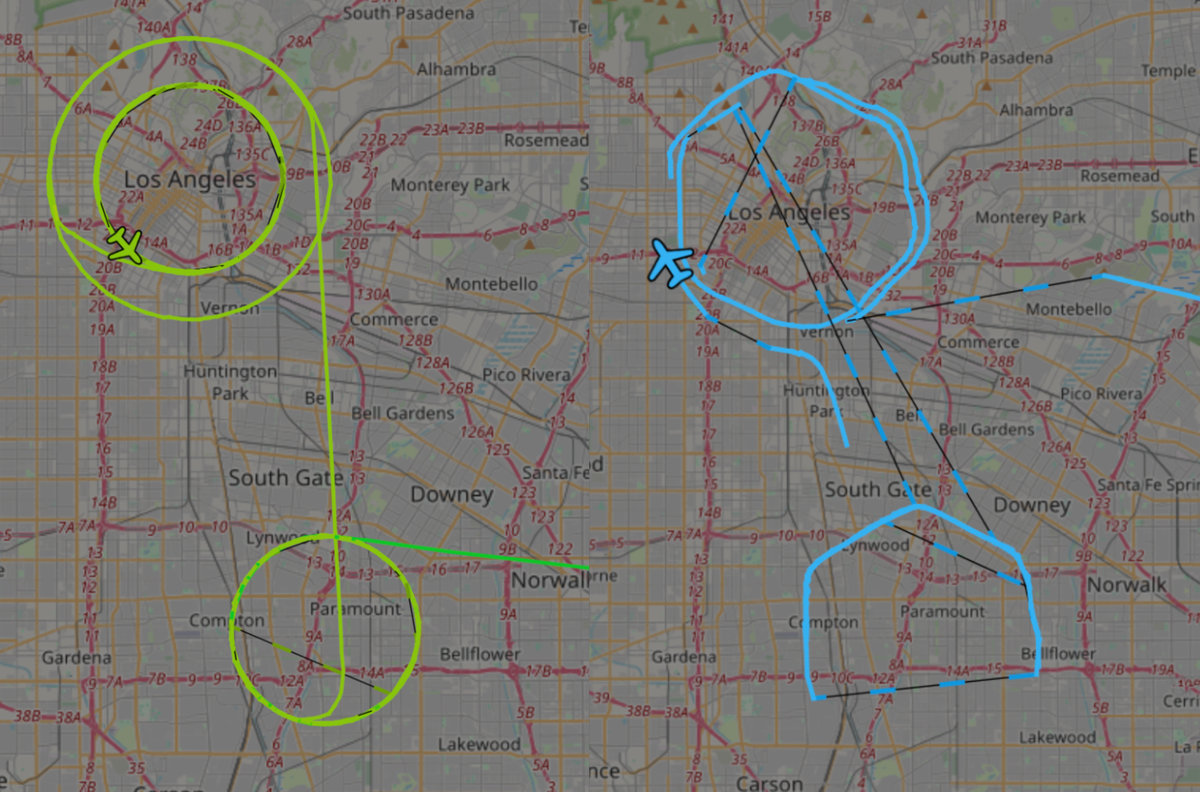
|
Description: Local police, state authorities, DHS, and the military all flew aircraft over the Los Angeles protests this weekend, according to flight path data.
June 9th, 2025 (about 1 month ago)
|

|
Description: A U.S. federal court has ordered OpenAI to indefinitely preserve all user-generated content from ChatGPT and its API services, including chats that users have deleted. The preservation order, signed by Magistrate Judge Ona T. Wang of the Southern District of New York, stems from ongoing copyright litigation initiated by The New York Times and other …
The post US Court Orders OpenAI to Preserve All ChatGPT Logs Indefinitely appeared first on CyberInsider.
June 9th, 2025 (about 1 month ago)
|

|
Description: A wide-ranging executive order issued before the weekend makes changes to directives from previously presidential administrations and issues some policy deadlines on quantum computing and artificial intelligence.
June 9th, 2025 (about 1 month ago)
|
|
CVE-2025-5877 |
Fengoffice Feng Office Document Upload ApplicationDataObject.class.php xml external entity reference
Description: A vulnerability, which was classified as problematic, has been found in Fengoffice Feng Office 3.2.2.1. Affected by this issue is some unknown functionality of the file /application/models/ApplicationDataObject.class.php of the component Document Upload Handler. The manipulation leads to xml external entity reference. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way. Eine problematische Schwachstelle wurde in Fengoffice Feng Office 3.2.2.1 entdeckt. Es geht hierbei um eine nicht näher spezifizierte Funktion der Datei /application/models/ApplicationDataObject.class.php der Komponente Document Upload Handler. Mittels Manipulieren mit unbekannten Daten kann eine xml external entity reference-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk angegangen werden. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (6.3) EPSS Score: 0.04%
June 9th, 2025 (about 1 month ago)
|
|
CVE-2025-5876 |
Description: A vulnerability classified as problematic was found in Lucky LM-520-SC, LM-520-FSC and LM-520-FSC-SAM up to 20250321. Affected by this vulnerability is an unknown functionality. The manipulation leads to missing authentication. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way. In Lucky LM-520-SC, LM-520-FSC and LM-520-FSC-SAM bis 20250321 wurde eine problematische Schwachstelle entdeckt. Es geht um eine nicht näher bekannte Funktion. Mittels dem Manipulieren mit unbekannten Daten kann eine missing authentication-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk erfolgen. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (5.3) EPSS Score: 0.07%
June 9th, 2025 (about 1 month ago)
|
|
CVE-2025-49131 |
Description: FastGPT is an open-source project that provides a platform for building, deploying, and operating AI-driven workflows and conversational agents. The Sandbox container (fastgpt-sandbox) is a specialized, isolated environment used by FastGPT to safely execute user-submitted or dynamically generated code in isolation. The sandbox before version 4.9.11 has insufficient isolation and inadequate restrictions on code execution by allowing overly permissive syscalls, which allows attackers to escape the intended sandbox boundaries. Attackers could exploit this to read and overwrite arbitrary files and bypass Python module import restrictions. This is patched in version 4.9.11 by restricting the allowed system calls to a safer subset and additional descriptive error messaging.
CVSS: MEDIUM (6.3) EPSS Score: 0.06%
June 9th, 2025 (about 1 month ago)
|
