CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: BAF Management Consulting. The company provides consulting servic
es.
We are going to upload company data soon. They claim to process y
our data exclusively in accordance with applicable legal regulati
ons but failed. Lots of client accounting and financial data, emp
loyee information, etc.
July 15th, 2025 (about 4 hours ago)
|

|
Description: Based in Green Bay, Wis. ProActive Solutions USA, LLC is a privately held, ISO 9001 company that is a manufacturer of sanitizers, cleaning chemicals and herd health products for the farm and food industries. They are also a distributor of com ...
July 15th, 2025 (about 4 hours ago)
|
|
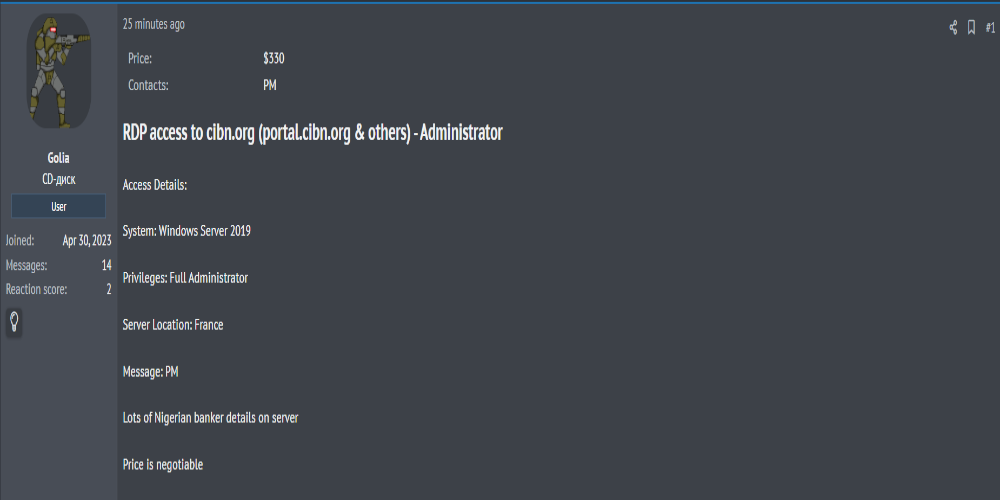
Description: Alleged Sale of The Chartered Institute of Bankers of Nigeria Access
July 15th, 2025 (about 4 hours ago)
|

|
Description: Cybersecurity researchers have shed light on a new ransomware-as-a-service (RaaS) operation called GLOBAL GROUP that has targeted a wide range of sectors in Australia, Brazil, Europe, and the United States since its emergence in early June 2025.
GLOBAL GROUP was "promoted on the Ramp4u forum by the threat actor known as '$$$,'" EclecticIQ researcher Arda Büyükkaya said. "The same actor controls
July 15th, 2025 (about 4 hours ago)
|

|
Description: Nearly two minutes of Mark Zuckerberg's thoughts about AI have been lost to the sands of time. Can Meta's all-powerful AI recover this artifact?
July 15th, 2025 (about 4 hours ago)
|
|
CVE-2025-53622 |
Description: DSpace open source software is a repository application which provides durable access to digital resources. Prior to versions 7.6.4, 8.2, and 9.1, a path traversal vulnerability is possible during the import of an archive (in Simple Archive Format), either from command-line (`./dspace import` command) or from the "Batch Import (Zip)" user interface feature. An attacker may craft a malicious Simple Archive Format (SAF) package where the `contents` file references any system files (using relative traversal sequences) which are readable by the Tomcat user. If such a package is imported, this will result in sensitive content disclose, including retrieving arbitrary files or configurations from the server where DSpace is running. The Simple Archive Format (SAF) importer / Batch Import (Zip) is only usable by site administrators (from user interface / REST API) or system administrators (from command-line). Therefore, to exploit this vulnerability, the malicious payload would have to be provided by an attacker and trusted by an administrator (who would trigger the import). The fix is included in DSpace 7.6.4, 8.2 and 9.1. For those who cannot upgrade immediately, it is possible to manually patch the DSpace backend. (No changes are necessary to the frontend.) A pull request exists which can be used to patch systems running DSpace 7.6.x, 8.x or 9.0. Although it is not possible to fully protect the system via workarounds, one may can apply a best practice. Administrators must care...
CVSS: MEDIUM (5.2)
July 15th, 2025 (about 4 hours ago)
|
|
CVE-2025-53621 |
Description: DSpace open source software is a repository application which provides durable access to digital resources. Two related XML External Entity (XXE) injection possibilities impact all versions of DSpace prior to 7.6.4, 8.2, and 9.1. External entities are not disabled when parsing XML files during import of an archive (in Simple Archive Format), either from command-line (`./dspace import` command) or from the "Batch Import (Zip)" user interface feature. External entities are also not explicitly disabled when parsing XML responses from some upstream services (ArXiv, Crossref, OpenAIRE, Creative Commons) used in import from external sources via the user interface or REST API. An XXE injection in these files may result in a connection being made to an attacker's site or a local path readable by the Tomcat user, with content potentially being injected into a metadata field. In the latter case, this may result in sensitive content disclosure, including retrieving arbitrary files or configurations from the server where DSpace is running. The Simple Archive Format (SAF) importer / Batch Import (Zip) is only usable by site administrators (from user interface / REST API) or system administrators (from command-line). Therefore, to exploit this vulnerability, the malicious payload would have to be provided by an attacker and trusted by an administrator, who would trigger the import. The fix is included in DSpace 7.6.4, 8.2, and 9.1. Please upgrade to one of these versions. For those who ...
CVSS: MEDIUM (6.9) SSVC Exploitation: none
July 15th, 2025 (about 4 hours ago)
|
|
CVE-2025-52379 |
Description: Nexxt Solutions NCM-X1800 Mesh Router firmware UV1.2.7 and below contains an authenticated command injection vulnerability in the firmware update feature. The /web/um_fileName_set.cgi and /web/um_web_upgrade.cgi endpoints fail to properly sanitize the upgradeFileName parameter, allowing authenticated attackers to execute arbitrary OS commands on the device, resulting in remote code execution.
July 15th, 2025 (about 4 hours ago)
|
|
CVE-2025-52378 |
Description: Cross-Site Scripting (XSS) vulnerability in Nexxt Solutions NCM-X1800 Mesh Router firmware UV1.2.7 and below allowing attackers to inject JavaScript code that is executed in the context of administrator sessions when viewing the device management page via the DEVICE_ALIAS parameter to the /web/um_device_set_aliasname endpoint.
July 15th, 2025 (about 4 hours ago)
|
|
CVE-2025-52377 |
Description: Command injection vulnerability in Nexxt Solutions NCM-X1800 Mesh Router versions UV1.2.7 and below, allowing authenticated attackers to execute arbitrary commands on the device. The vulnerability is present in the web management interface's ping and traceroute functionality, specifically in the /web/um_ping_set.cgi endpoint. The application fails to properly sanitize user input in the `Ping_host_text` parameter before passing it to the underlying system command, allowing attackers to inject and execute arbitrary shell commands as the root user.
July 15th, 2025 (about 4 hours ago)
|
