CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Exclusive: Following 404 Media’s investigation into Meta's AI Studio chatbots that pose as therapists and provided license numbers and credentials, four senators urged Meta to limit "blatant deception" from its chatbots.
June 9th, 2025 (15 days ago)
|

|
Description: As rare as it is specialized, the profession of naturalist engineer—or ecologist—aims to diagnose a natural ecosystem in order to understand the ecological challenges of a site and guide development projects in intelligent collaboration w ...
June 9th, 2025 (15 days ago)
|

|
Description: Dugoni is a company that operates in the Facilities Management & Commercial Cleaning industry. It employs 20to49 people and has 1Mto5M of revenue. The company is headquartered in Mantova, Lombardy, Italy.
June 9th, 2025 (15 days ago)
|

|
Description: Girva International Broker Srl is a company that operates in the Automobile Dealers industry. It employs 10to19 people and has 1Mto5M of revenue. The company is headquartered in Castellammare di Stabia, Campania, Italy.GI.R.VA. INTERNATIONAL ...
June 9th, 2025 (15 days ago)
|
|
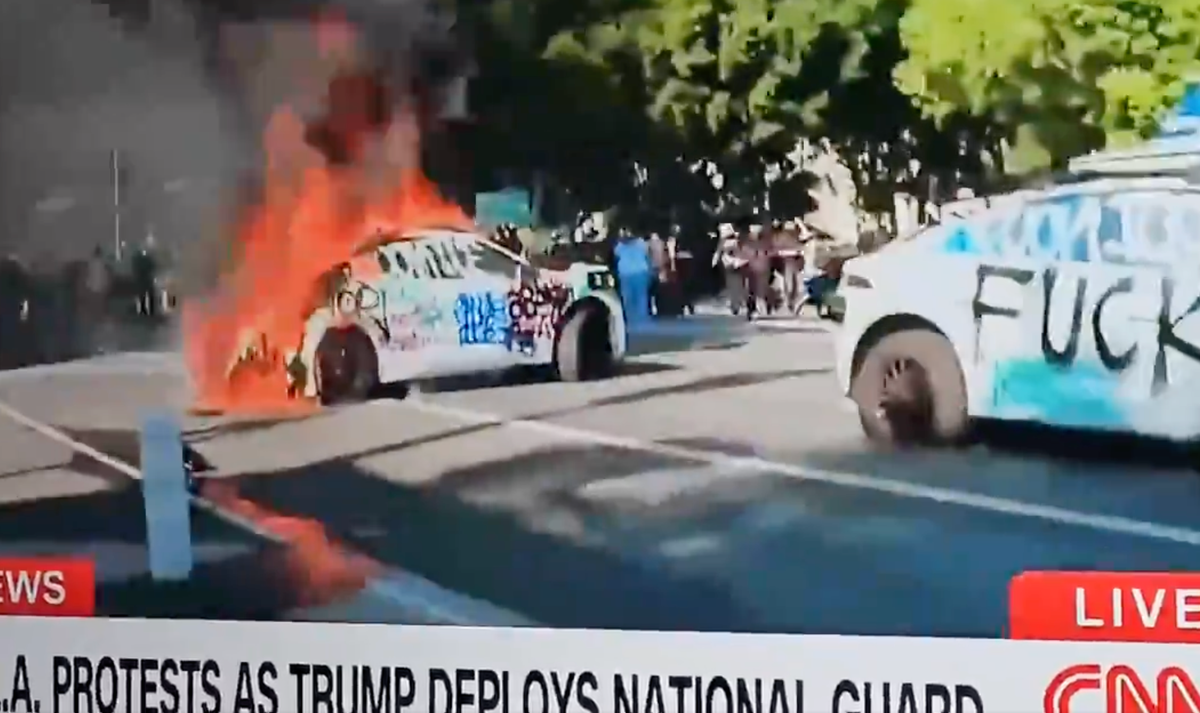
Description: A company spokesperson said it is working with law enforcement to determine when it can move the cars that have been.
June 9th, 2025 (15 days ago)
|
|
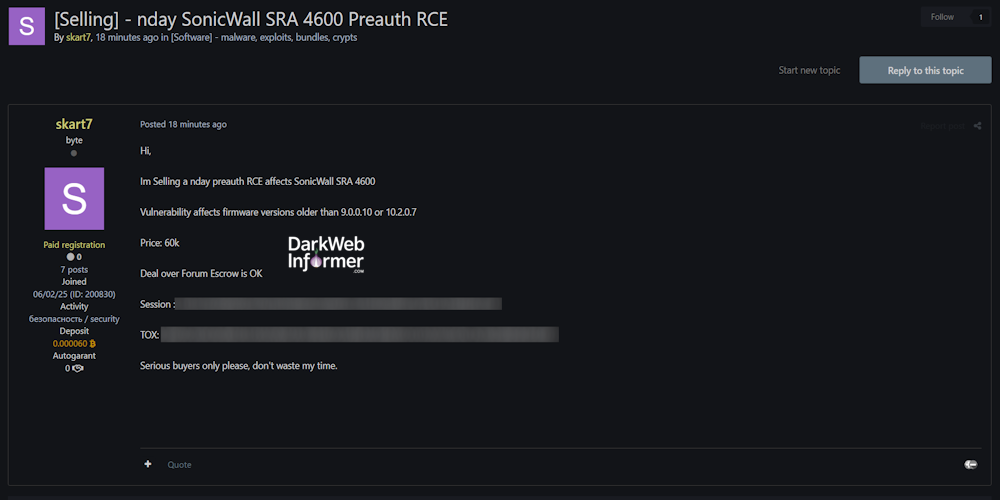
Description: Alleged sale of 0-day SonicWall SRA 4600 Preauth RCE
June 9th, 2025 (15 days ago)
|
|
CVE-2025-5880 |
Description: A vulnerability has been found in Whistle 2.9.98 and classified as problematic. This vulnerability affects unknown code of the file /cgi-bin/sessions/get-temp-file. The manipulation of the argument filename leads to path traversal. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way. In Whistle 2.9.98 wurde eine problematische Schwachstelle gefunden. Dabei geht es um eine nicht genauer bekannte Funktion der Datei /cgi-bin/sessions/get-temp-file. Durch Manipulieren des Arguments filename mit unbekannten Daten kann eine path traversal-Schwachstelle ausgenutzt werden. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (4.3) EPSS Score: 0.03%
June 9th, 2025 (15 days ago)
|
|
CVE-2025-5879 |
Description: A vulnerability, which was classified as problematic, was found in WuKongOpenSource WukongCRM 9.0. This affects an unknown part of the file AdminSysConfigController.java of the component File Upload. The manipulation of the argument File leads to cross site scripting. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way. Es wurde eine problematische Schwachstelle in WuKongOpenSource WukongCRM 9.0 gefunden. Es geht dabei um eine nicht klar definierte Funktion der Datei AdminSysConfigController.java der Komponente File Upload. Durch das Manipulieren des Arguments File mit unbekannten Daten kann eine cross site scripting-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk passieren. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (5.1) EPSS Score: 0.03% SSVC Exploitation: poc
June 9th, 2025 (15 days ago)
|

|
Description: AI coding tools promise productivity but deliver security problems, too. As developers embrace "vibe coding," enterprises face mounting risks from insecure code generation that security teams can't keep pace with.
June 9th, 2025 (15 days ago)
|

|
Description: Blue Team playbooks are essential—but tools like Wazuh take them to the next level. From credential dumping to web shells and brute-force attacks, see how Wazuh strengthens real-time detection and automated response. [...]
June 9th, 2025 (15 days ago)
|
