CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
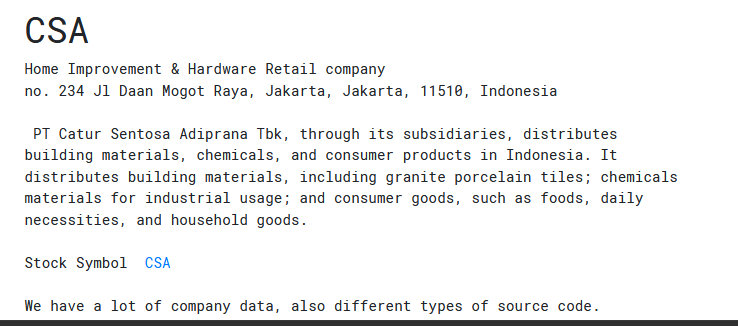
Description: PT Catur Sentosa Adiprana Tbk Falls Victim to RansomHub Ransomware; 112 GB Data at Risk
March 10th, 2025 (4 months ago)
|

|
Description: The Laravel framework versions between 11.9.0 and 11.35.1 are susceptible to reflected cross-site scripting due to an improper encoding of request parameters in the debug-mode error page.
References
https://nvd.nist.gov/vuln/detail/CVE-2024-13918
https://github.com/laravel/framework/pull/53869
https://github.com/laravel/framework/releases/tag/v11.36.0
https://github.com/sbaresearch/advisories/tree/public/2024/SBA-ADV-20241209-01_Laravel_Reflected_XSS_via_Request_Parameter_in_Debug-Mode_Error_Page
http://www.openwall.com/lists/oss-security/2025/03/10/3
https://github.com/laravel/framework/commit/45287fb2a91c69bb1c110539b9b7341faf5aee33
https://github.com/advisories/GHSA-546h-56qp-8jmw
CVSS: HIGH (8.0) EPSS Score: 0.01%
March 10th, 2025 (4 months ago)
|

|
Description: Impact
Due to lack of limits by default in the explode() function, malicious clients were able to abuse some packets to waste server CPU and memory.
This is similar to a previous security issue published in https://github.com/pmmp/PocketMine-MP/security/advisories/GHSA-gj94-v4p9-w672, but with a wider impact, including but not limited to:
Sign editing
LoginPacket JWT parsing
Command parsing
However, the estimated impact of these issues is low, due to other limits such as the packet decompression limit.
Patches
The issue was fixed in 5.25.2 via d0d84d4c5195fb0a68ea7725424fda63b85cd831.
A custom PHPStan rule has also been introduced to the project, which will henceforth require that all calls to explode() within the codebase must specify the limit parameter.
Workarounds
No simple way to fix this.
Given that sign editing is the easiest way this could be exploited, workarounds could include plugins pre-processing BlockActorDataPacket to check that the incoming text doesn't have more than 4 parts when split by \n.
References
https://github.com/pmmp/PocketMine-MP/security/advisories/GHSA-g274-c6jj-h78p
https://github.com/pmmp/PocketMine-MP/security/advisories/GHSA-gj94-v4p9-w672
https://github.com/pmmp/PocketMine-MP/commit/d0d84d4c5195fb0a68ea7725424fda63b85cd831
https://github.com/advisories/GHSA-g274-c6jj-h78p
March 10th, 2025 (4 months ago)
|

|
Description: The Laravel framework versions between 11.9.0 and 11.35.1 are susceptible to reflected cross-site scripting due to an improper encoding of route parameters in the debug-mode error page.
References
https://nvd.nist.gov/vuln/detail/CVE-2024-13919
https://github.com/laravel/framework/pull/53869
https://github.com/laravel/framework/releases/tag/v11.36.0
https://github.com/sbaresearch/advisories/tree/public/2024/SBA-ADV-20241209-02_Laravel_Reflected_XSS_via_Route_Parameter_in_Debug-Mode_Error_Page
http://www.openwall.com/lists/oss-security/2025/03/10/4
https://github.com/laravel/framework/commit/45287fb2a91c69bb1c110539b9b7341faf5aee33
https://github.com/advisories/GHSA-83wp-f5c3-hqqr
CVSS: HIGH (8.0) EPSS Score: 0.01%
March 10th, 2025 (4 months ago)
|

|
March 10th, 2025 (4 months ago)
|
|
CVE-2024-54560 |
Description: A logic issue was addressed with improved checks. This issue is fixed in iOS 18 and iPadOS 18, watchOS 11, tvOS 18, macOS Sequoia 15. A malicious app may be able to modify other apps without having App Management permission.
EPSS Score: 0.01%
March 10th, 2025 (4 months ago)
|
|
CVE-2024-54558 |
Description: A clickjacking issue was addressed with improved out-of-process view handling. This issue is fixed in iOS 18 and iPadOS 18, macOS Sequoia 15. An app may be able to trick a user into granting access to photos from the user's photo library.
EPSS Score: 0.01%
March 10th, 2025 (4 months ago)
|
|
CVE-2024-54546 |
Description: The issue was addressed with improved memory handling. This issue is fixed in macOS Sequoia 15. An app may be able to cause unexpected system termination or corrupt kernel memory.
EPSS Score: 0.04%
March 10th, 2025 (4 months ago)
|
|
CVE-2024-54473 |
Description: This issue was addressed with improved redaction of sensitive information. This issue is fixed in macOS Sequoia 15. An app may be able to access user-sensitive data.
EPSS Score: 0.02%
March 10th, 2025 (4 months ago)
|
|
CVE-2024-54469 |
Description: The issue was addressed with improved checks. This issue is fixed in macOS Ventura 13.7, macOS Sequoia 15, macOS Sonoma 14.7, visionOS 2, iOS 18 and iPadOS 18. A local user may be able to leak sensitive user information.
EPSS Score: 0.01%
March 10th, 2025 (4 months ago)
|
