CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Facebook is warning that a FreeType vulnerability in all versions up to 2.13 can lead to arbitrary code execution, with reports that the flaw has been exploited in attacks. [...]
March 12th, 2025 (4 months ago)
|

|
Description: Bypass/Injection vulnerability in Apache Camel.
This issue affects Apache Camel: from 4.9.0 before 4.10.2, from 4.0.0 before 4.8.5, from 3.10.0 before 3.22.4.
Users are recommended to upgrade to version 4.10.2 for 4.10.x LTS, 4.8.5 for 4.8.x LTS and 3.22.4 for 3.x releases.
This vulnerability is present in Camel's default incoming header filter, that allows an attacker to include Camel specific headers that for some Camel components can alter the behaviours such as the camel-bean component, or the camel-exec component.
If you have Camel applications that are directly connected to the internet via HTTP, then an attacker could include parameters in the HTTP requests that are sent to the Camel application that incorrectly get translated into headers.
The headers could be both provided as request parameters for an HTTP methods invocation or as part of the payload of the HTTP methods invocation.
All the known Camel HTTP component such as camel-servlet, camel-jetty, camel-undertow, camel-platform-http, and camel-netty-http would be vulnerable out of the box.
This CVE is related to the CVE-2025-27636: while they have the same root cause and are fixed with the same fix, CVE-2025-27636 was assumed to only be exploitable if an attacker could add malicious HTTP headers, while we have now determined that it is also exploitable via HTTP parameters. Like in CVE-2025-27636, exploitation is only possible if the Camel route uses particular vulnerable components.
References
https://nvd.ni...
EPSS Score: 20.46%
March 12th, 2025 (4 months ago)
|

|
Description: A flaw was found in Smallrye, where smallrye-fault-tolerance is vulnerable to an out-of-memory (OOM) issue. This vulnerability is externally triggered when calling the metrics URI. Every call creates a new object within meterMap and may lead to a denial of service (DoS) issue.
References
https://nvd.nist.gov/vuln/detail/CVE-2025-2240
https://access.redhat.com/security/cve/CVE-2025-2240
https://bugzilla.redhat.com/show_bug.cgi?id=2351452
https://github.com/smallrye/smallrye-fault-tolerance/commit/e8bcad3d5e8bbac0a3219bd5c13661adf6ed6bbb
https://github.com/advisories/GHSA-gfh6-3pqw-x2j4
EPSS Score: 0.07%
March 12th, 2025 (4 months ago)
|

|
Description: A threat actor leveraged the vulnerability in an "extremely sophisticated" attack on targeted iOS users, the company says.
March 12th, 2025 (4 months ago)
|
|
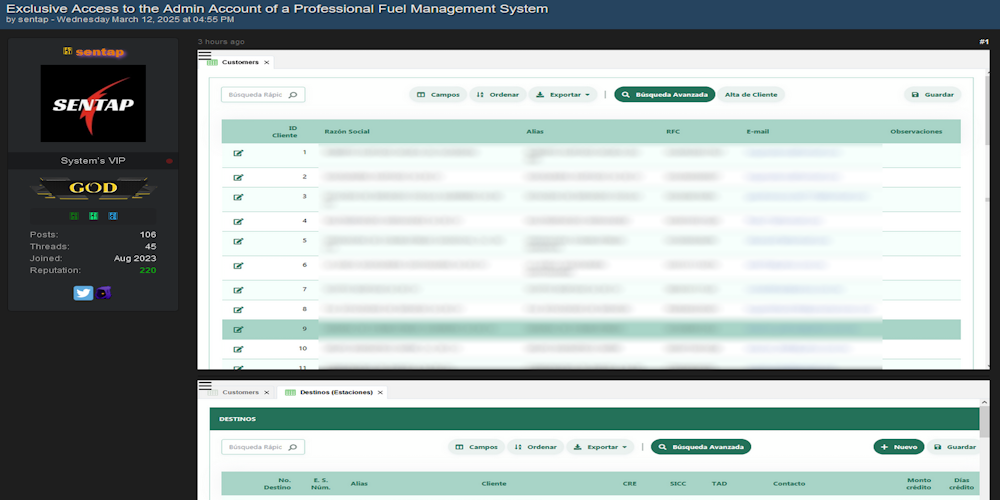
Description: Alleged Sale of Unauthorized Access to a Fuel Management System in Mexico
March 12th, 2025 (4 months ago)
|
|
CVE-2025-2216 |
Description: A vulnerability, which was classified as critical, has been found in zzskzy Warehouse Refinement Management System 1.3. Affected by this issue is the function UploadCrash of the file /crash/log/SaveCrash.ashx. The manipulation of the argument file leads to unrestricted upload. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way. Eine kritische Schwachstelle wurde in zzskzy Warehouse Refinement Management System 1.3 entdeckt. Betroffen davon ist die Funktion UploadCrash der Datei /crash/log/SaveCrash.ashx. Dank der Manipulation des Arguments file mit unbekannten Daten kann eine unrestricted upload-Schwachstelle ausgenutzt werden. Die Umsetzung des Angriffs kann dabei über das Netzwerk erfolgen. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (5.3) EPSS Score: 0.04% SSVC Exploitation: none
March 12th, 2025 (4 months ago)
|
|
CVE-2024-26290 |
Description: Improper Input Validation vulnerability in Avid Avid NEXIS E-series on Linux, Avid Avid NEXIS F-series on Linux, Avid Avid NEXIS PRO+ on Linux, Avid System Director Appliance (SDA+) on Linux allows code execution on underlying operating system with root permissions.This issue affects Avid NEXIS E-series: before 2024.6.0; Avid NEXIS F-series: before 2024.6.0; Avid NEXIS PRO+: before 2024.6.0; System Director Appliance (SDA+): before 2024.6.0.
CVSS: HIGH (8.7) EPSS Score: 0.1% SSVC Exploitation: none
March 12th, 2025 (4 months ago)
|

|
Description: Summary
Loading a malicious schema definition in GraphQL::Schema.from_introspection (or GraphQL::Schema::Loader.load) can result in remote code execution. Any system which loads a schema by JSON from an untrusted source is vulnerable, including those that use GraphQL::Client to load external schemas via GraphQL introspection.
References
https://github.com/rmosolgo/graphql-ruby/security/advisories/GHSA-q92j-grw3-h492
https://github.com/rmosolgo/graphql-ruby/commit/e58676c70aa695e3052ba1fbc787efee4ba7d67e
https://github.com/advisories/GHSA-q92j-grw3-h492
March 12th, 2025 (4 months ago)
|

|
Description: Summary
There are 2 new Critical Signature Wrapping Vulnerabilities (CVE-2025-25292, CVE-2025-25291) and a potential DDOS Moderated Vulneratiblity (CVE-2025-25293) affecting ruby-saml, a dependency of omniauth-saml.
The fix will be applied to ruby-saml and released 12 March 2025, under version 1.18.0.
Please upgrade the ruby-saml requirement to v1.18.0.
Impact
Signature Wrapping Vulnerabilities allows an attacker to impersonate a user.
References
https://github.com/omniauth/omniauth-saml/security/advisories/GHSA-hw46-3hmr-x9xv
https://github.com/omniauth/omniauth-saml/commit/0d5eaa0d808acb2ac96deadf5c750ac1cf2d92b5
https://github.com/omniauth/omniauth-saml/commit/2c8a482801808bbcb0188214bde74680b8018a35
https://github.com/omniauth/omniauth-saml/commit/7a348b49083462a566af41a5ae85e9f3af15b985
https://github.com/omniauth/omniauth-saml/blob/master/omniauth-saml.gemspec#L16
https://rubygems.org/gems/omniauth-saml/versions/2.2.3
https://github.com/advisories/GHSA-hw46-3hmr-x9xv
EPSS Score: 1.05%
March 12th, 2025 (4 months ago)
|

|
Description: Name: ISA-2025-002: x/group can halt when erroring in EndBlocker
Component: CosmosSDK
Criticality: High (Considerable Impact; Likely Likelihood per ACMv1.2)
Affected versions: <= v0.47.16, <= 0.50.12
Affected users: Validators, Full nodes, Users on chains that utilize the groups module
Cosmos SDK chains in unpatched releases that use the x/group module are affected.
Description
An issue was discovered in the groups module where malicious proposals would result in an errors triggered in the module's end blocker that could result in a chain halt. Any set of users that can interact with the groups module could introduce this state.
Patches
Has the problem been patched? What versions should users upgrade to?
The new Cosmos SDK release v0.50.13 and v0.47.17 fix this issue.
Testing
Testing we have done to gain more confidence in this release:
In addition to testing Cosmos SDK we also did the following:
Ran a patched node in a local v0.50 testnet with the failing state and did not halt (an unpatched network confirmed to halt)
Ran a patched node on Xion Mainnet (uses x/group)
Ran a patched node on Zetachain Mainnet (uses x/xgroup)
Workarounds
Is there a way for users to fix or remediate the vulnerability without upgrading?
There are no known workarounds for this issue. It is advised that chains apply the update.
This issue was reported to the Cosmos Bug Bounty Program by dongsam on HackerOne on February 28, 2025. If you believe you have found a bug in the Interchain Stack or wo...
March 12th, 2025 (4 months ago)
|
