CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
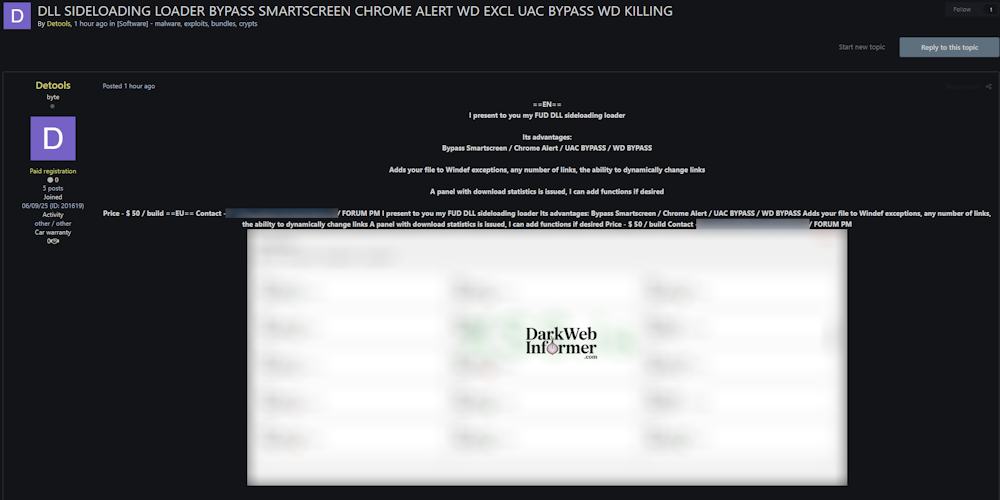
Description: Alleged Sale of Chrome Alert Bypass and WD Exclusion
June 10th, 2025 (12 days ago)
|
|
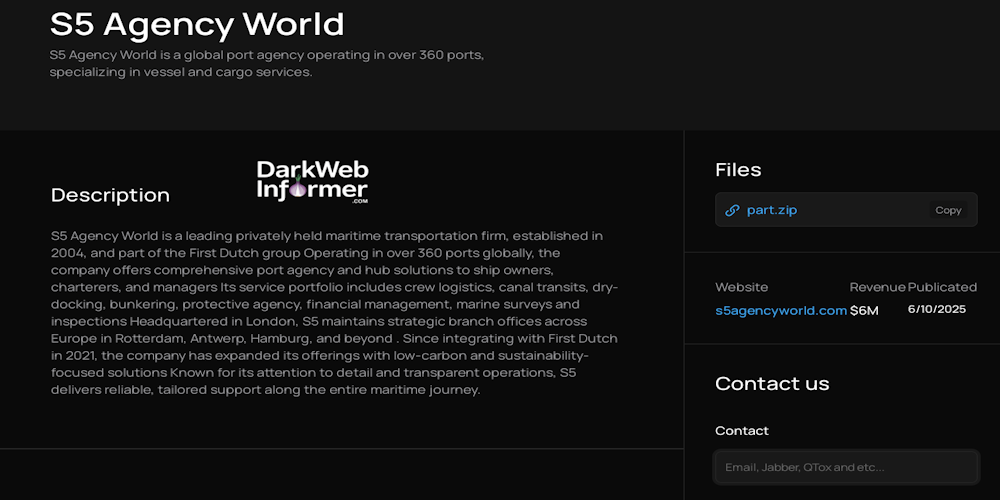
Description: S5 Agency World Ltd falls victim to BERT Ransomware
June 10th, 2025 (12 days ago)
|

|
Description: SSH keys enable critical system access but often lack proper management. This security blind spot creates significant risk through untracked, unrotated credentials that persist across your infrastructure.
June 10th, 2025 (12 days ago)
|

|
Description: Backdoors lurking in legitimate-looking code contain file-deletion commands that can destroy production systems and cause massive disruptions to software supply chains.
June 10th, 2025 (12 days ago)
|

|
Description: Boost employee security awareness with Threat Simulator from Huntress Managed SAT. It features hands-on training, game-like sessions, and real results. Start your free trial today.
June 10th, 2025 (12 days ago)
|

|
Description: Cybersecurity researchers have shed light on a previously undocumented Rust-based information stealer called Myth Stealer that's being propagated via fraudulent gaming websites.
"Upon execution, the malware displays a fake window to appear legitimate while simultaneously decrypting and executing malicious code in the background," Trellix security researchers Niranjan Hegde, Vasantha Lakshmanan
June 10th, 2025 (12 days ago)
|

|
Description: A contract obtained by 404 Media shows that an airline-owned data broker forbids the feds from revealing it sold them detailed passenger data.
June 10th, 2025 (12 days ago)
|
|
Description: A new website and API called AI.gov is set to launch on the Fourth of July.
June 10th, 2025 (12 days ago)
|

|
Description: Air traffic control (ATC) audio unearthed by an aviation tracking enthusiast then reviewed by 404 Media shows two Predator drones leaving, and heading towards, Los Angeles.
June 10th, 2025 (12 days ago)
|
|
CVE-2025-5484 |
Description: View CSAF
1. EXECUTIVE SUMMARY
CVSS v4 8.8
ATTENTION: Exploitable remotely/Low attack complexity
Vendor: SinoTrack
Equipment: All Known SinoTrack Devices
Vulnerabilities: Weak Authentication, Observable Response Discrepency
2. RISK EVALUATION
Successful exploitation of these vulnerabilities could allow an attacker to access device profiles without authorization through the common web management interface. Access to the device profile may allow an attacker to perform some remote functions on connected vehicles such as tracking the vehicle location and disconnecting power to the fuel pump where supported.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
The following SinoTrack products are affected:
SinoTrack IOT PC Platform: All versions
3.2 VULNERABILITY OVERVIEW
3.2.1 WEAK AUTHENTICATION CWE-1390
A username and password are required to authenticate to the central SinoTrack device management interface. The username for all devices is an identifier printed on the receiver. The default password is well-known and common to all devices. Modification of the default password is not enforced during device setup. A malicious actor can retrieve device identifiers with either physical access or by capturing identifiers from pictures of the devices posted on publicly accessible websites such as eBay.
CVE-2025-5484 has been assigned to this vulnerability. A CVSS v3 base score of 8.3 has been calculated; the CVSS vector string is (AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:L).
A CVSS v4 score has...
CVSS: HIGH (8.3) EPSS Score: 0.04%
June 10th, 2025 (12 days ago)
|
