Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2024-20499 |
Description: Multiple vulnerabilities in the Cisco AnyConnect VPN server of Cisco Meraki MX and Cisco Meraki Z Series Teleworker Gateway devices could allow an unauthenticated, remote attacker to cause a DoS condition in the AnyConnect service on an affected device.
These vulnerabilities are due to insufficient validation of client-supplied parameters while establishing an SSL VPN session. An attacker could exploit these vulnerabilities by sending a crafted HTTPS request to the VPN server of an affected device. A successful exploit could allow the attacker to cause the Cisco AnyConnect VPN server to restart, resulting in the failure of the established SSL VPN connections and forcing remote users to initiate a new VPN connection and reauthenticate. A sustained attack could prevent new SSL VPN connections from being established.
Note: When the attack traffic stops, the Cisco AnyConnect VPN server recovers gracefully without requiring manual intervention.
CVSS: HIGH (8.6) EPSS Score: 0.04% SSVC Exploitation: none
June 4th, 2025 (3 days ago)
|
|
CVE-2024-20498 |
Description: Multiple vulnerabilities in the Cisco AnyConnect VPN server of Cisco Meraki MX and Cisco Meraki Z Series Teleworker Gateway devices could allow an unauthenticated, remote attacker to cause a DoS condition in the AnyConnect service on an affected device.
These vulnerabilities are due to insufficient validation of client-supplied parameters while establishing an SSL VPN session. An attacker could exploit these vulnerabilities by sending a crafted HTTPS request to the VPN server of an affected device. A successful exploit could allow the attacker to cause the Cisco AnyConnect VPN server to restart, resulting in the failure of the established SSL VPN connections and forcing remote users to initiate a new VPN connection and reauthenticate. A sustained attack could prevent new SSL VPN connections from being established.
Note: When the attack traffic stops, the Cisco AnyConnect VPN server recovers gracefully without requiring manual intervention.
CVSS: HIGH (8.6) EPSS Score: 0.04% SSVC Exploitation: none
June 4th, 2025 (3 days ago)
|

|
Description: Cisco has released patches to address three vulnerabilities with public exploit code in its Identity Services Engine (ISE) and Customer Collaboration Platform (CCP) solutions. [...]
June 4th, 2025 (3 days ago)
|
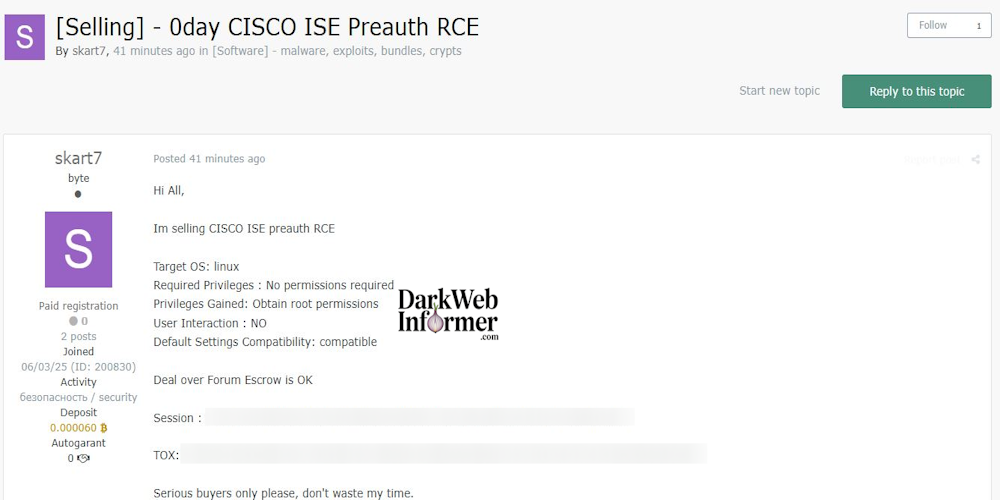
|
Description: Alleged sale of Cisco ISE Pre-auth Remote Code Execution (0day) Exploit
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20286 |
Description: A vulnerability in Amazon Web Services (AWS), Microsoft Azure, and Oracle Cloud Infrastructure (OCI) cloud deployments of Cisco Identity Services Engine (ISE) could allow an unauthenticated, remote attacker to access sensitive data, execute limited administrative operations, modify system configurations, or disrupt services within the impacted systems.
This vulnerability exists because credentials are improperly generated when Cisco ISE is being deployed on cloud platforms, resulting in different Cisco ISE deployments sharing the same credentials. These credentials are shared across multiple Cisco ISE deployments as long as the software release and cloud platform are the same. An attacker could exploit this vulnerability by extracting the user credentials from Cisco ISE that is deployed in the cloud and then using them to access Cisco ISE that is deployed in other cloud environments through unsecured ports. A successful exploit could allow the attacker to access sensitive data, execute limited administrative operations, modify system configurations, or disrupt services within the impacted systems.
Note: If the Primary Administration node is deployed in the cloud, then Cisco ISE is affected by this vulnerability. If the Primary Administration node is on-premises, then it is not affected.
CVSS: CRITICAL (9.9) EPSS Score: 0.13%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20279 |
Description: A vulnerability in the web-based management interface of Cisco Unified CCX could allow an authenticated, remote attacker to conduct a stored XSS attack on an affected system. To exploit this vulnerability, the attacker must have valid administrative credentials.
This vulnerability is due to improper sanitization of user input to the web-based management interface. An attacker could exploit this vulnerability by submitting a malicious script through the interface. A successful exploit could allow the attacker to conduct a stored XSS attack on the affected system.
CVSS: MEDIUM (4.8) EPSS Score: 0.03%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20278 |
Description: A vulnerability in the CLI of multiple Cisco Unified Communications products could allow an authenticated, local attacker to execute arbitrary commands on the underlying operating system of an affected device as the root user.
This vulnerability is due to improper validation of user-supplied command arguments. An attacker could exploit this vulnerability by executing crafted commands on the CLI of an affected device. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system of an affected device as the root user. To exploit this vulnerability, the attacker must have valid administrative credentials.
CVSS: MEDIUM (6.0) EPSS Score: 0.01%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20277 |
Description: A vulnerability in the web-based management interface of Cisco Unified CCX could allow an authenticated, local attacker to execute arbitrary code on an affected device. To exploit this vulnerability, the attacker must have valid administrative credentials.
This vulnerability is due to improper limitation of a pathname to a restricted directory (path traversal). An attacker could exploit this vulnerability by sending a crafted web request to an affected device, followed by a specific command through an SSH session. A successful exploit could allow the attacker to execute arbitrary code on the underlying operating system of an affected device as a low-privilege user. A successful exploit could also allow the attacker to undertake further actions to elevate their privileges to root.
CVSS: LOW (3.4) EPSS Score: 0.01%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20276 |
Description: A vulnerability in the web-based management interface of Cisco Unified CCX could allow an authenticated, remote attacker to execute arbitrary code on an affected device. To exploit this vulnerability, the attacker must have valid administrative credentials.
This vulnerability is due to insecure deserialization of Java objects by the affected software. An attacker could exploit this vulnerability by sending a crafted Java object to an affected device. A successful exploit could allow the attacker to execute arbitrary code on the underlying operating system of an affected device as a low-privilege user. A successful exploit could also allow the attacker to undertake further actions to elevate their privileges to root.
CVSS: LOW (3.8) EPSS Score: 0.11%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20275 |
Description: A vulnerability in the file opening process of Cisco Unified Contact Center Express (Unified CCX) Editor could allow an unauthenticated attacker to execute arbitrary code on an affected device.
This vulnerability is due to insecure deserialization of Java objects by the affected software. An attacker could exploit this vulnerability by persuading an authenticated, local user to open a crafted .aef file. A successful exploit could allow the attacker to execute arbitrary code on the host that is running the editor application with the privileges of the user who launched it.
CVSS: MEDIUM (5.3) EPSS Score: 0.06%
June 4th, 2025 (3 days ago)
|
