CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-3530 |
Description: The WordPress Simple Shopping Cart plugin for WordPress is vulnerable to product price manipulation in all versions up to, and including, 5.1.2. This is due to a logic flaw involving the inconsistent use of parameters during the cart addition process. The plugin uses the parameter 'product_tmp_two' for computing a security hash against price tampering while using 'wspsc_product' to display the product, allowing an unauthenticated attacker to substitute details from a cheaper product and bypass payment for a more expensive item.
CVSS: HIGH (7.5) EPSS Score: 0.1%
April 23rd, 2025 (about 2 months ago)
|
|
CVE-2025-3529 |
Description: The WordPress Simple Shopping Cart plugin for WordPress is vulnerable to Sensitive Information Exposure in all versions up to, and including, 5.1.2 via the 'file_url' parameter. This makes it possible for unauthenticated attackers to view potentially sensitive information and download a digital product without paying for it.
CVSS: HIGH (8.2) EPSS Score: 0.07%
April 23rd, 2025 (about 2 months ago)
|
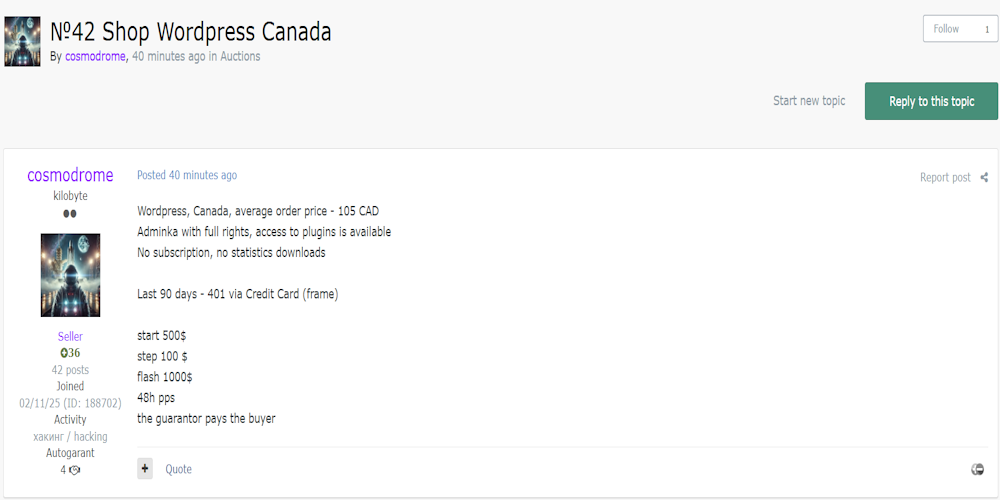
|
Description: Alleged Unauthorized Access to WordPress eCommerce Site of an Unnamed Canadian Retail Store Listed for Sale
April 22nd, 2025 (about 2 months ago)
|
|
CVE-2024-24843 |
Description: Cross-Site Request Forgery (CSRF) vulnerability in PowerPack Addons for Elementor PowerPack Pro for Elementor.This issue affects PowerPack Pro for Elementor: from n/a before 2.10.8.
CVSS: HIGH (7.1) EPSS Score: 0.1% SSVC Exploitation: none
April 22nd, 2025 (about 2 months ago)
|
|
CVE-2024-24837 |
Description: Cross-Site Request Forgery (CSRF) vulnerability in Frédéric GILLES FG PrestaShop to WooCommerce, Frédéric GILLES FG Drupal to WordPress, Frédéric GILLES FG Joomla to WordPress.This issue affects FG PrestaShop to WooCommerce: from n/a through 4.44.3; FG Drupal to WordPress: from n/a through 3.67.0; FG Joomla to WordPress: from n/a through 4.15.0.
CVSS: MEDIUM (4.3) EPSS Score: 0.07% SSVC Exploitation: none
April 22nd, 2025 (about 2 months ago)
|
|
CVE-2024-1710 |
Description: The Addon Library plugin for WordPress is vulnerable to unauthorized access of data due to a missing capability check on the onAjaxAction function action in all versions up to, and including, 1.3.76. This makes it possible for authenticated attackers, with subscriber-level access and above, to perform several unauthorized actions including uploading arbitrary files.
CVSS: HIGH (8.8) EPSS Score: 0.23% SSVC Exploitation: none
April 22nd, 2025 (about 2 months ago)
|
|
CVE-2024-1653 |
Description: The Categorify plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the categorifyAjaxUpdateFolderPosition in all versions up to, and including, 1.0.7.4. This makes it possible for authenticated attackers, with subscriber-level access and above, to update the folder position of categories as well as update the metadata of other taxonomies.
CVSS: MEDIUM (4.3) EPSS Score: 0.1% SSVC Exploitation: none
April 22nd, 2025 (about 2 months ago)
|
|
CVE-2024-1492 |
Description: The WPify Woo Czech plugin for WordPress is vulnerable to unauthorized access of data due to a missing capability check on the maybe_send_to_packeta function in all versions up to, and including, 4.0.8. This makes it possible for unauthenticated attackers to obtain shipping details for orders as long as the order number is known.
CVSS: MEDIUM (5.3) EPSS Score: 0.29% SSVC Exploitation: none
April 22nd, 2025 (about 2 months ago)
|
|
CVE-2024-1323 |
Description: The Orbit Fox by ThemeIsle plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's Post Type Grid Widget Title in all versions up to, and including, 2.10.30 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers with contributor-level and above permissions to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
CVSS: MEDIUM (6.4) EPSS Score: 0.12% SSVC Exploitation: none
April 22nd, 2025 (about 2 months ago)
|
|
CVE-2024-1318 |
Description: The RSS Aggregator by Feedzy – Feed to Post, Autoblogging, News & YouTube Video Feeds Aggregator plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the 'feedzy_wizard_step_process' and 'import_status' functions in all versions up to, and including, 4.4.2. This makes it possible for authenticated attackers, with Contributor access and above, who are normally restricted to only being able to create posts rather than pages, to draft and publish posts with arbitrary content.
CVSS: MEDIUM (6.5) EPSS Score: 0.17% SSVC Exploitation: none
April 22nd, 2025 (about 2 months ago)
|
