CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-3844 |
Description: The PeproDev Ultimate Profile Solutions plugin for WordPress is vulnerable to Authentication Bypass in versions 1.9.1 to 7.5.2. This is due to handel_ajax_req() function not having proper restrictions on the change_user_meta functionality that makes it possible to set a OTP code and subsequently log in with that OTP code. This makes it possible for unauthenticated attackers to login as other users on the site, including administrators.
CVSS: CRITICAL (9.8) EPSS Score: 0.31%
May 7th, 2025 (about 1 month ago)
|
|
CVE-2025-2821 |
Description: The Search Exclude plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the get_rest_permission function in all versions up to, and including, 2.4.9. This makes it possible for unauthenticated attackers to modify plugin settings, excluding content from search results.
CVSS: MEDIUM (5.3) EPSS Score: 0.06%
May 7th, 2025 (about 1 month ago)
|
|
CVE-2025-0856 |
Description: The PGS Core plugin for WordPress is vulnerable to unauthorized access, modification, and loss of data due to a missing capability check on multiple functions in all versions up to, and including, 5.8.0. This makes it possible for unauthenticated attackers to add, modify, or plugin options.
CVSS: HIGH (7.3) EPSS Score: 0.09%
May 6th, 2025 (about 1 month ago)
|
|
CVE-2025-0855 |
Description: The PGS Core plugin for WordPress is vulnerable to PHP Object Injection in all versions up to, and including, 5.8.0 via deserialization of untrusted input in the 'import_header' function. This makes it possible for unauthenticated attackers to inject a PHP Object. No known POP chain is present in the vulnerable software. If a POP chain is present via an additional plugin or theme installed on the target system, it could allow the attacker to delete arbitrary files, retrieve sensitive data, or execute code.
CVSS: CRITICAL (9.8) EPSS Score: 0.15%
May 6th, 2025 (about 1 month ago)
|
|
CVE-2025-0853 |
Description: The PGS Core plugin for WordPress is vulnerable to SQL Injection via the 'event' parameter in the 'save_header_builder' function in all versions up to, and including, 5.8.0 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for unauthenticated attackers to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database.
CVSS: HIGH (7.5) EPSS Score: 0.08%
May 6th, 2025 (about 1 month ago)
|
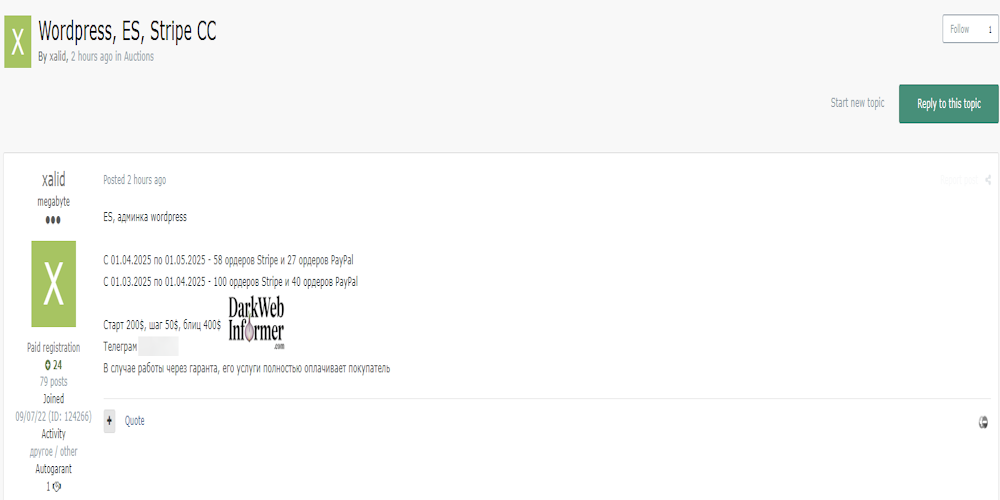
|
Description: Alleged Sale of WordPress Admin Access to a Spanish Website
May 6th, 2025 (about 1 month ago)
|
|
CVE-2025-3782 |
Description: The Cision Block plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the ‘id’ parameter in all versions up to, and including, 4.3.0 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
CVSS: MEDIUM (6.4) EPSS Score: 0.03%
May 6th, 2025 (about 1 month ago)
|
|
CVE-2025-2011 |
Description: The Slider & Popup Builder by Depicter plugin for WordPress is vulnerable to generic SQL Injection via the ‘s' parameter in all versions up to, and including, 3.6.1 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for unauthenticated attackers to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database.
CVSS: HIGH (7.5) EPSS Score: 53.37%
May 6th, 2025 (about 1 month ago)
|
|
CVE-2025-3281 |
Description: The User Registration & Membership – Custom Registration Form, Login Form, and User Profile plugin for WordPress is vulnerable to Insecure Direct Object Reference in all versions up to, and including, 4.2.1 via the create_stripe_subscription() function, due to missing validation on the 'member_id' user controlled key. This makes it possible for unauthenticated attackers to delete arbitrary user accounts that have registered through the plugin.
CVSS: MEDIUM (5.3) EPSS Score: 0.03%
May 6th, 2025 (about 1 month ago)
|
|
CVE-2025-4337 |
Description: The AHAthat Plugin plugin for WordPress is vulnerable to Cross-Site Request Forgery in all versions up to, and including, 1.6. This is due to missing or incorrect nonce validation on the aha_plugin_page() function. This makes it possible for unauthenticated attackers to delete AHA pages via a forged request granted they can trick a site administrator into performing an action such as clicking on a link.
CVSS: MEDIUM (4.3) EPSS Score: 0.01%
May 6th, 2025 (about 1 month ago)
|
