CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2024-24304 |
Description: In the module "Mailjet" (mailjet) from Mailjet for PrestaShop before versions 3.5.1, a guest can download technical information without restriction.
EPSS Score: 0.07% SSVC Exploitation: none
June 9th, 2025 (6 days ago)
|
|
CVE-2024-24188 |
Description: Jsish v3.5.0 was discovered to contain a heap-buffer-overflow in ./src/jsiUtils.c.
EPSS Score: 0.59% SSVC Exploitation: none
June 9th, 2025 (6 days ago)
|
|
CVE-2024-24021 |
Description: A SQL injection vulnerability exists in Novel-Plus v4.3.0-RC1 and prior. An attacker can pass specially crafted offset, limit, and sort parameters to perform SQL injection via /novel/userFeedback/list.
CVSS: CRITICAL (9.8) EPSS Score: 0.05% SSVC Exploitation: none
June 9th, 2025 (6 days ago)
|

|
June 9th, 2025 (6 days ago)
|
|
|
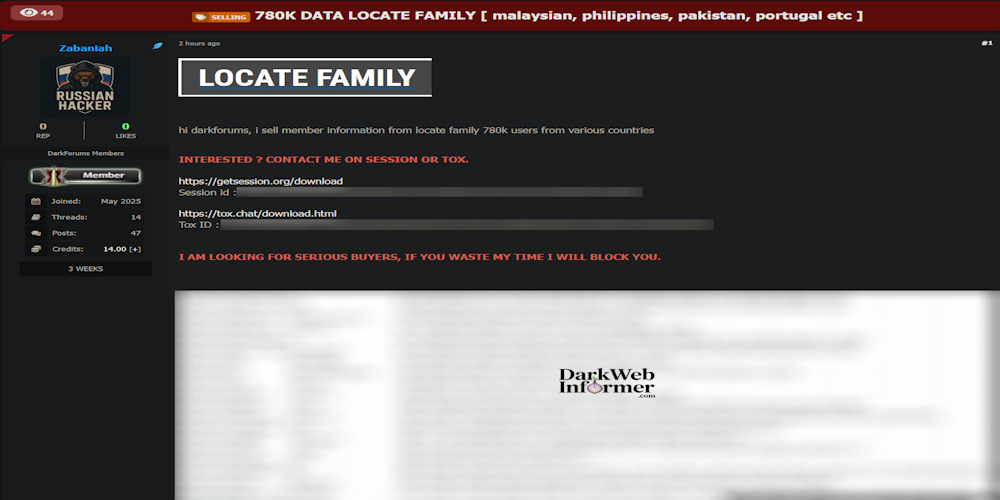
|
Description: Alleged Data Breach of Locate Family
June 9th, 2025 (6 days ago)
|

|
Description: A longtime FBI official with deep cybersecurity experience is the new leader for the bureau's Cyber Division.
June 9th, 2025 (6 days ago)
|
|
CVE-2025-5886 |
Description: A vulnerability was found in Emlog up to 2.5.7 and classified as problematic. This issue affects some unknown processing of the file /admin/article.php. The manipulation of the argument active_post leads to cross site scripting. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. Eine problematische Schwachstelle wurde in Emlog bis 2.5.7 gefunden. Dies betrifft einen unbekannten Teil der Datei /admin/article.php. Mittels dem Manipulieren des Arguments active_post mit unbekannten Daten kann eine cross site scripting-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk passieren. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (5.1) EPSS Score: 0.03%
June 9th, 2025 (6 days ago)
|
|
CVE-2025-49297 |
Description: Path Traversal vulnerability in Mikado-Themes Grill and Chow allows PHP Local File Inclusion. This issue affects Grill and Chow: from n/a through 1.6.
CVSS: HIGH (8.1) EPSS Score: 0.05%
June 9th, 2025 (6 days ago)
|
|
CVE-2025-49296 |
Description: Path Traversal vulnerability in Mikado-Themes GrandPrix allows PHP Local File Inclusion. This issue affects GrandPrix: from n/a through 1.6.
CVSS: HIGH (8.1) EPSS Score: 0.05%
June 9th, 2025 (6 days ago)
|
