Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
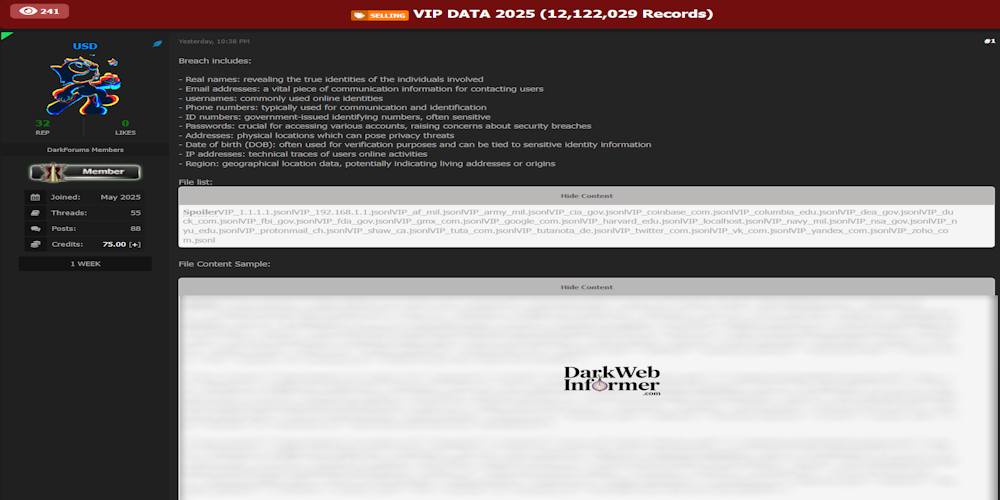
|
Description: Alleged data breach of VIP Data 2025 exposing over 12 million records
May 29th, 2025 (12 days ago)
|

|
Description: Attackers are mapping your infrastructure before you even realize what's exposed. Sprocket ASM flips the script — giving you the same recon capabilities they use, plus change detection and actionable insights to close gaps fast. See your attack surface the way hackers do and beat them to it. [...]
May 29th, 2025 (12 days ago)
|

|
Description: Cybersecurity researchers have taken the wraps off an unusual cyber attack that leveraged malware with corrupted DOS and PE headers, according to new findings from Fortinet.
The DOS (Disk Operating System) and PE (Portable Executable) headers are essential parts of a Windows PE file, providing information about the executable.
While the DOS header makes the executable file backward compatible
May 29th, 2025 (12 days ago)
|

|
Description: The retailer's domain now features a brief message to customers explaining that it has “identified and are taking steps to address a security incident.”
May 29th, 2025 (12 days ago)
|

|
Description: [AI generated] ASC Machine Tools is a prominent manufacturer of high-quality, innovative, and dependable equipment for the metal building and steel processing industries. The company was established in 1949 and has been serving clients with their proficiency and experience in designing and manufacturing machine tools. Their product offerings include roll forming machines, panel lapping machines, and other assorted equipment.
May 29th, 2025 (12 days ago)
|

|
Description: Google Threat Intelligence spotted the China-based operation known as APT41 leveraging the company's own Calendar app as part of a cyber-espionage campaign.
May 29th, 2025 (12 days ago)
|

|
Description: The acquisition of Apex Security adds a powerful new layer of visibility, context and control to the Tenable One Exposure Management Platform to govern usage, enforce policy and control exposure across both the AI that organizations use and the AI they build.Over the past 25 years, we’ve seen the attack surface shift dramatically — from traditional on-prem environments to cloud, to OT/IOT, and more. But the changes we’re seeing right now with AI feel different. Faster. More disruptive. And, frankly, more unpredictable.That’s why I’m excited to share that Tenable has signed a definitive agreement to acquire Apex Security, a company we’ve been following for some time. They've built a powerful product that solves real problems in the emerging world of AI risk. Their focus is helping organizations secure both the AI they use and the AI they build — a problem that's becoming more critical every day.It’s clear we’re in the early stages of a major shift. Developers are integrating large language models into products and internal tools. Employees are using generative tools in everyday workflows. AI is everywhere — but the tools to manage that risk at scale? Not so much.Last year, we introduced AI Aware to help organizations get visibility into shadow AI. It’s been incredible to see how quickly customers adopted it — more than 6,400 customers in over 100 countries are using it today. But we also heard loud and clear: visibility isn’t enough. Security leaders want to govern usage, e...
May 29th, 2025 (12 days ago)
|

|
Description: A new report from Stanford finds that schools, parents, police, and our legal system are not prepared to deal with the growing problem of minors using AI to generate CSAM of other minors.
May 29th, 2025 (12 days ago)
|

|
Description: www.muliaraya.co.id $34.8 Million The list of files is available at the link https://dropmefiles.com/lAZQo
May 29th, 2025 (12 days ago)
|

|
Description: [AI generated] Infinox is a UK-based financial services company that offers clients the ability to trade FX, indices, commodities and equities. It provides a variety of trading platforms, including MT4 and IXO, and offers multilingual customer support. Infinox aims for transparency and customer empowerment, offering resources for traders to increase their market knowledge. It's regulated by the FCA.
May 29th, 2025 (12 days ago)
|
