CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
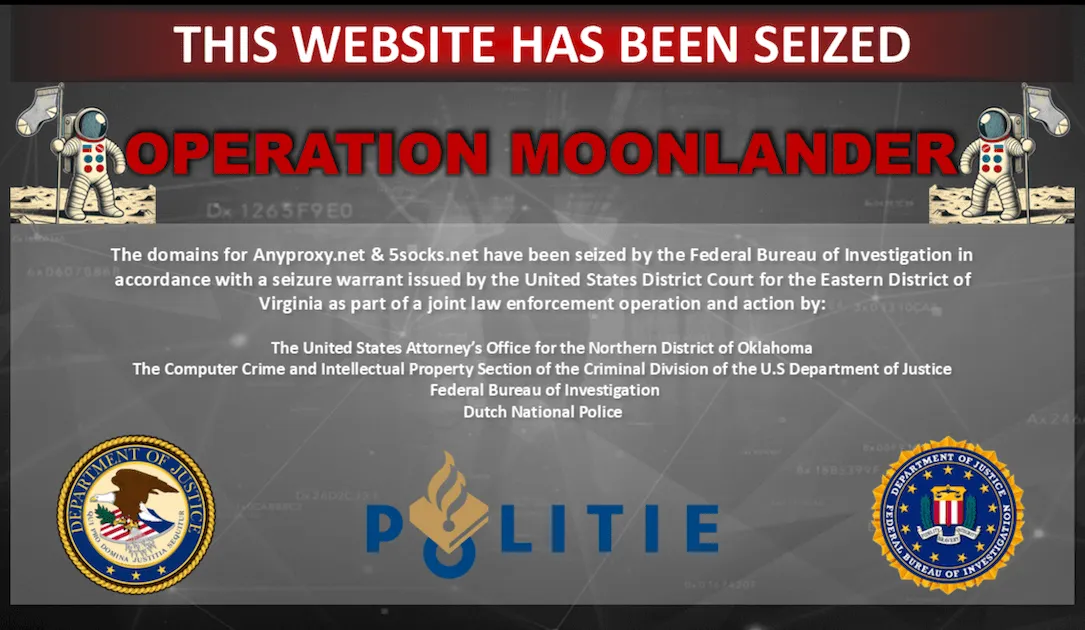
Description: U.S. prosecutors charged four foreign nationals and said a law enforcement operation seized internet domains associated with two powerful botnets.
May 9th, 2025 (about 1 month ago)
|

|
Description: A joint law enforcement operation undertaken by Dutch and U.S. authorities has dismantled a criminal proxy network that's powered by thousands of infected Internet of Things (IoT) and end-of-life (EoL) devices, enlisting them into a botnet for providing anonymity to malicious actors.
In conjunction with the domain seizure, Russian nationals, Alexey Viktorovich Chertkov, 37, Kirill Vladimirovich
May 9th, 2025 (about 1 month ago)
|
|
Description:
Quick Post: These short-form updates provide fast, digestible summaries of breaches, DDoS attacks, and defacements—ideal when full details aren't yet available.
Because having a reliable source and critical data when you need it matters.
×
💡 Subscribe to DarkWebInformer.com for Unmatched Cyber Threat Intelligence 💡
May 9th, 2025 (about 1 month ago)
|

|
Description: Since the start of the year, the Russian state-backed ColdRiver hacking group has been using new LostKeys malware to steal files in espionage attacks targeting Western governments, journalists, think tanks, and non-governmental organizations. [...]
May 8th, 2025 (about 1 month ago)
|

|
Description: A Russian cyber-espionage group tracked as Coldriver by Google researchers has updated its malware toolset.
May 8th, 2025 (about 1 month ago)
|

|
Description: Google's Threat Intelligence Group (GTIG) has uncovered a new espionage tool called LOSTKEYS, attributed to the Russia-linked threat group COLDRIVER. The malware, observed in active campaigns throughout early 2025, marks a shift in the group's capabilities — from credential theft to direct data exfiltration from infected systems. Google's analysis outlines a multi-stage attack chain used …
The post Russian State Actors Use New ‘LOSTKEYS’ Malware to Steal Docs From Western Orgs appeared first on CyberInsider.
May 8th, 2025 (about 1 month ago)
|

|
Description: The Russia-linked threat actor known as COLDRIVER has been observed distributing a new malware called LOSTKEYS as part of an espionage-focused campaign using ClickFix-like social engineering lures.
"LOSTKEYS is capable of stealing files from a hard-coded list of extensions and directories, along with sending system information and running processes to the attacker," the Google Threat
May 8th, 2025 (about 1 month ago)
|

|
Description: Cyber chief Richard Horne said intelligence agencies were seeing the hacking threat from Russia manifesting “on the streets of the UK."
May 7th, 2025 (about 1 month ago)
|

|
Description: Written by: Wesley Shields
Google Threat Intelligence Group (GTIG) has identified a new piece of malware called LOSTKEYS, attributed to the Russian government-backed threat group COLDRIVER (also known as UNC4057, Star Blizzard, and Callisto). LOSTKEYS is capable of stealing files from a hard-coded list of extensions and directories, along with sending system information and running processes to the attacker. Observed in January, March, and April 2025, LOSTKEYS marks a new development in the toolset of COLDRIVER, a group primarily known for credential phishing against high-profile targets like NATO governments, non-governmental organizations (NGOs), and former intelligence and diplomatic officers. GTIG has been tracking COLDRIVER for many years, including their SPICA malware in 2024.
COLDRIVER typically targets high-profile individuals at their personal email addresses or at NGO addresses. They are known for stealing credentials and after gaining access to a target’s account they exfiltrate emails and steal contact lists from the compromised account. In select cases, COLDRIVER also delivers malware to target devices and may attempt to access files on the system.
Recent targets in COLDRIVER’s campaigns have included current and former advisors to Western governments and militaries, as well as journalists, think tanks, and NGOs. The group has also continued targeting individuals connected to Ukraine. We believe the primary goal of COLDRIVER’s operations is intelligence colle...
May 7th, 2025 (about 1 month ago)
|

|
Description: The Kremlin said there were "restrictions for understandable reasons" on mobile internet service ahead of this year's Victory Day celebrations.
May 7th, 2025 (about 1 month ago)
|
