Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: A new malware campaign is distributing a novel Rust-based information stealer dubbed EDDIESTEALER using the popular ClickFix social engineering tactic initiated via fake CAPTCHA verification pages.
"This campaign leverages deceptive CAPTCHA verification pages that trick users into executing a malicious PowerShell script, which ultimately deploys the infostealer, harvesting sensitive data such as
May 30th, 2025 (10 days ago)
|

|
Description: Alleged data breach of Deloitte – Internal GitHub Credentials and Source Code Leaked
May 30th, 2025 (10 days ago)
|

|
Description: The latest report from Meta on social media influence operations tracked some low-impact campaigns to China, Iran and Romania.
May 30th, 2025 (10 days ago)
|
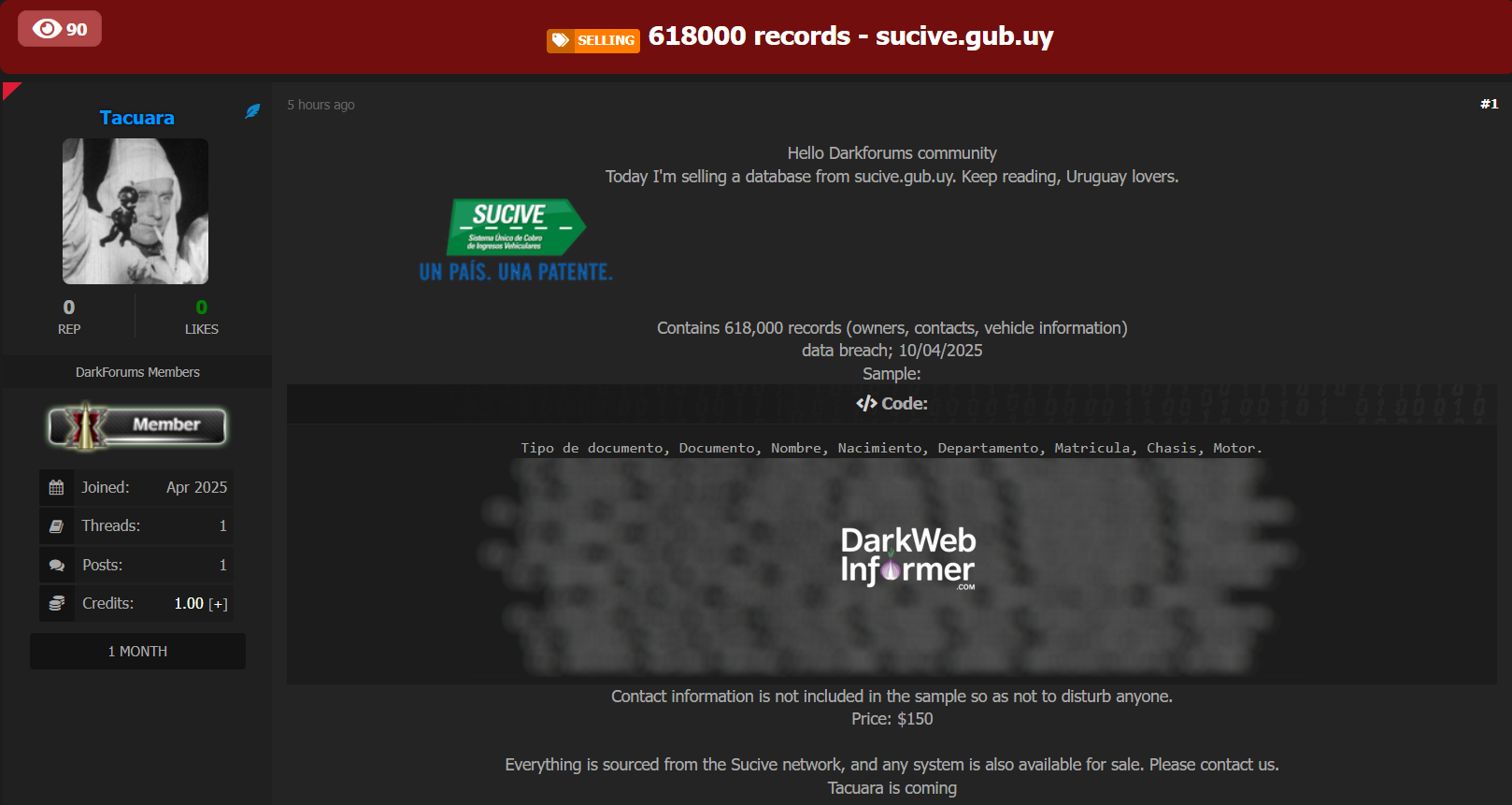
|
Description: Alleged data breach of Sucive – Uruguay’s Vehicle Tax and Registration Network
May 30th, 2025 (10 days ago)
|

|
Description: Apex will enhance Tenable's AI Aware tool by mitigating the threats of AI applications and tools not governed by organizations, while enforcing existing security policies.
May 30th, 2025 (10 days ago)
|
|
CVE-2025-4433 |
Description: Improper access control in user group management in Devolutions Server 2025.1.7.0 and earlier allows a non-administrative user with both "User Management" and "User Group Management" permissions to perform privilege escalation by adding users to groups with administrative privileges.
EPSS Score: 0.04%
May 30th, 2025 (10 days ago)
|
|
CVE-2025-40909 |
Description: Perl threads have a working directory race condition where file operations may target unintended paths.
If a directory handle is open at thread creation, the process-wide current working directory is temporarily changed in order to clone that handle for the new thread, which is visible from any third (or more) thread already running.
This may lead to unintended operations such as loading code or accessing files from unexpected locations, which a local attacker may be able to exploit.
The bug was introduced in commit 11a11ecf4bea72b17d250cfb43c897be1341861e and released in Perl version 5.13.6
EPSS Score: 0.02%
May 30th, 2025 (10 days ago)
|

|
Description: The rate of compensation gains has slowed from the COVID years, and budgets remain largely static due to economic fears, but CISOs are increasingly gaining executive status and responsibilities.
May 30th, 2025 (10 days ago)
|

|
Description: Wheel King Transhaul Inc. is a privately held Canadian company with dedicated fleet services as its core business. Our company is built upon the values and work ethics that are foundational to family operated businesses. We offer our custome ...
May 30th, 2025 (10 days ago)
|

|
Description: Check out ETSI’s new global standard for securing AI systems and models. Plus, learn how CISOs and their teams add significant value to orgs’ major initiatives. In addition, discover what webinar attendees told Tenable about their cloud security challenges. And get the latest on properly decommissioning tech products; a cyber threat targeting law firms; and more!Dive into six things that are top of mind for the week ending May 30.1 - ETSI publishes global standard for AI securityWhat is the proper way to secure your artificial intelligence models and systems? Are you confused by all the different AI security recommendations and guidance? The European Telecommunications Standards Institute (ETSI) is trying to bring clarity to this issue.ETSI, in collaboration with the U.K. National Cyber Security Center (NCSC) and the U.K. Department for Science, Innovation & Technology (DSIT), has published a global standard for AI security designed to cover the full lifecycle of an AI system.Aimed at developers, vendors, operators, integrators, buyers and other AI stakeholders, ETSI’s “Securing Artificial Intelligence (SAI); Baseline Cyber Security Requirements for AI Models and Systems” technical specification outlines a set of baseline security principles for an AI system’s entire lifecycle.Here are the details:Secure design stageRaise awareness about AI security threats and risksDesign the AI system not only for security but also for functionality and performanceEvaluate the threats an...
May 30th, 2025 (10 days ago)
|
