Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Summary
A security vulnerability has been identified in go-gh where an attacker-controlled GitHub Enterprise Server could result in executing arbitrary commands on a user's machine by replacing HTTP URLs provided by GitHub with local file paths for browsing.
Details
The GitHub CLI and CLI extensions allow users to transition from their terminal for a variety of use cases through the Browser capability in github.com/cli/go-gh/v2/pkg/browser:
Using the -w, --web flag, GitHub CLI users can view GitHub repositories, issues, pull requests, and more using their web browser
Using the gh codespace command set, GitHub CLI users can transition to Visual Studio Code to work with GitHub Codespaces
This is done by using URLs provided through API responses from authenticated GitHub hosts when users execute gh commands.
Prior to 2.12.1, Browser.Browse() would attempt to open the provided URL using a variety of OS-specific approaches regardless of the scheme. An attacker-controlled GitHub Enterprise Server could modify API responses to use a specially tailored local executable path instead of HTTP URLs to resources. This could allow the attacker to execute arbitrary executables on the user's machine.
In 2.12.1, Browser.Browse() has been enhanced to allow and disallow a variety of scenarios to avoid opening or executing files on the filesystem without unduly impacting HTTP URLs:
URLs with http://, https://, vscode://, vscode-insiders:// protocols are supported
URLs with file:// prot...
May 30th, 2025 (10 days ago)
|

|
Description: Pentesting isn't just about finding flaws — it's about knowing which ones matter. Pentera's 2025 State of Pentesting report uncovers which assets attackers target most, where security teams are making progress, and which exposures still fly under the radar. Focus on reducing breach impact, not just breach count. [...]
May 30th, 2025 (10 days ago)
|

|
Description: The Federal Criminal Police Office of Germany (Bundeskriminalamt or BKA) claims that Stern, the leader of the Trickbot and Conti cybercrime gangs, is a 36-year-old Russian named Vitaly Nikolaevich Kovalev. [...]
May 30th, 2025 (10 days ago)
|

|
Description: A 28-year-old civilian IT worker at the Defense Intelligence Agency has been arrested in Northern Virginia on suspicion that he leaked secrets to a foreign government.
May 30th, 2025 (10 days ago)
|
|
CVE-2024-23725 |
Description: Ghost before 5.76.0 allows XSS via a post excerpt in excerpt.js. An XSS payload can be rendered in post summaries.
EPSS Score: 0.16% SSVC Exploitation: none
May 30th, 2025 (10 days ago)
|
|
CVE-2024-23689 |
Description: Exposure of sensitive information in exceptions in ClichHouse's clickhouse-r2dbc, com.clickhouse:clickhouse-jdbc, and com.clickhouse:clickhouse-client versions less than 0.4.6 allows unauthorized users to gain access to client certificate passwords via client exception logs. This occurs when 'sslkey' is specified and an exception, such as a ClickHouseException or SQLException, is thrown during database operations; the certificate password is then included in the logged exception message.
EPSS Score: 0.71% SSVC Exploitation: poc
May 30th, 2025 (10 days ago)
|
|
CVE-2024-23679 |
Description: Enonic XP versions less than 7.7.4 are vulnerable to a session fixation issue. An remote and unauthenticated attacker can use prior sessions due to the lack of invalidating session attributes.
EPSS Score: 0.66% SSVC Exploitation: none
May 30th, 2025 (10 days ago)
|
|
CVE-2024-22915 |
Description: A heap-use-after-free was found in SWFTools v0.9.2, in the function swf_DeleteTag at rfxswf.c:1193. It allows an attacker to cause code execution.
EPSS Score: 0.06% SSVC Exploitation: poc
May 30th, 2025 (10 days ago)
|
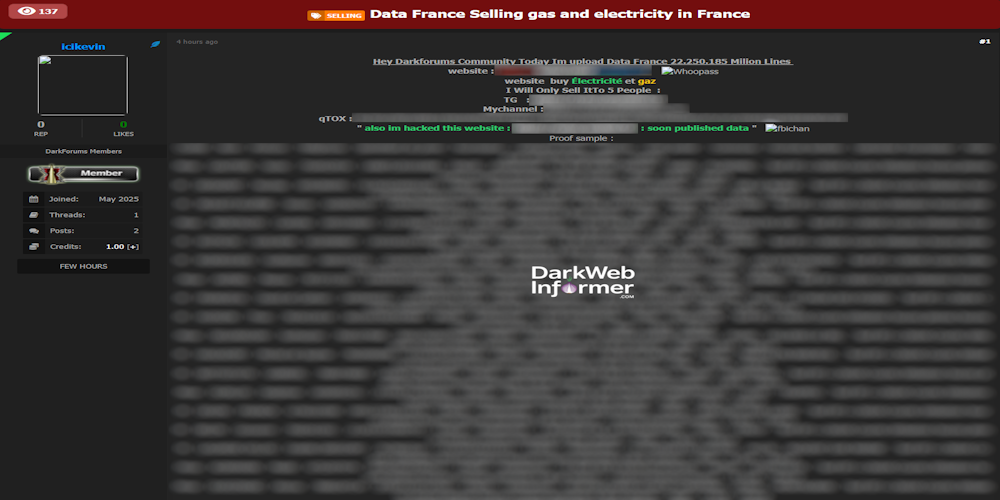
|
Description: Alleged data sale of TotalEnergies Power & Gas – 22.25 Million Records
May 30th, 2025 (10 days ago)
|

|
Description: AI tools changed your development process. Now product security must change too.
May 30th, 2025 (10 days ago)
|
