Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Data broker giant LexisNexis Risk Solutions has revealed that unknown attackers stole the personal information of over 364,000 individuals in a December breach. [...]
May 29th, 2025 (9 days ago)
|

|
Description: A newly discovered Go-based Linux botnet malware named PumaBot is brute-forcing SSH credentials on embedded IoT devices to deploy malicious payloads. [...]
May 28th, 2025 (9 days ago)
|

|
Description: The Czech Republic on Wednesday formally accused a threat actor associated with the People's Republic of China (PRC) of targeting its Ministry of Foreign Affairs.
In a public statement, the government said it identified China as the culprit behind a malicious campaign targeting one of the unclassified networks of the Czech Ministry of Foreign Affairs. The extent of the breach is presently not
May 28th, 2025 (9 days ago)
|

|
Description: An Iranian national has pleaded guilty in the U.S. over his involvement in an international ransomware and extortion scheme involving the Robbinhood ransomware.
Sina Gholinejad (aka Sina Ghaaf), 37, and his co-conspirators are said to have breached the computer networks of various organizations in the United States and encrypted files with Robbinhood ransomware to demand Bitcoin ransom payments.
May 28th, 2025 (9 days ago)
|

|
Description: Alleged data breach of Centro Nacional de Estimación, Prevención y Reducción del Riesgo de Desastres (CENEPRED)
May 28th, 2025 (9 days ago)
|
|
Description: The company said data held in GitHub pertaining to LexisNexis Risk Solutions had been acquired by an unknown third party.
May 28th, 2025 (9 days ago)
|
|
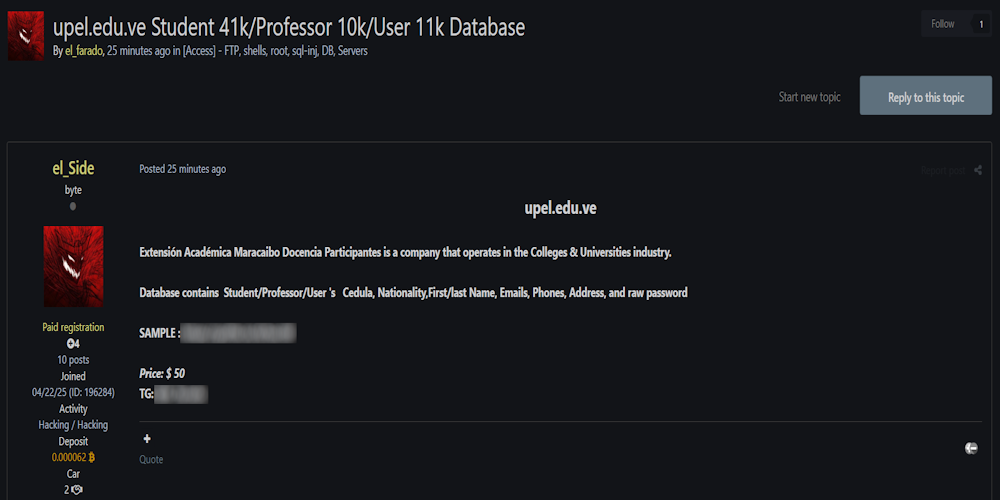
Description: Alleged Data Breach of Universidad Pedagógica Experimental Libertador (UPEL)
May 28th, 2025 (10 days ago)
|

|
Description: Estonia said a man is suspected of unlawfully accessing a customer card database managed by Allium UPI, the parent company of the Apotheka pharmacy chain, in February 2024.
May 28th, 2025 (10 days ago)
|

|
Description: For The Council Of L*S GROUP We have breached your main system l*s.com.vn We also took backup copy of all […]
May 28th, 2025 (10 days ago)
|

|
Description: The online service has since been shut down as the agency grapples with the cyberattack, though it assures the public that those most in need of legal assistance will still be able to access help.
May 27th, 2025 (10 days ago)
|
