CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: The U.S. government sanctioned the Karen National Army, a militia group, and Saw Chit Thu, its leader, for their purported connections to the cyber fraud industry in Myanmar.
May 5th, 2025 (about 2 months ago)
|

|
Description: Alleged Sale of Credit Card Data from Turkish Banks
May 5th, 2025 (about 2 months ago)
|

|
Description: A 43-year-old woman was reportedly tasked with identifying and photographing the positions of Ukrainian forces near the front-line town of Pokrovsk — currently one of the most active combat zones.
May 5th, 2025 (about 2 months ago)
|

|
Description: The Skype video call and messaging service is shutting down today, 14 years after replacing Microsoft's Windows Live Messenger. [...]
May 5th, 2025 (about 2 months ago)
|
|
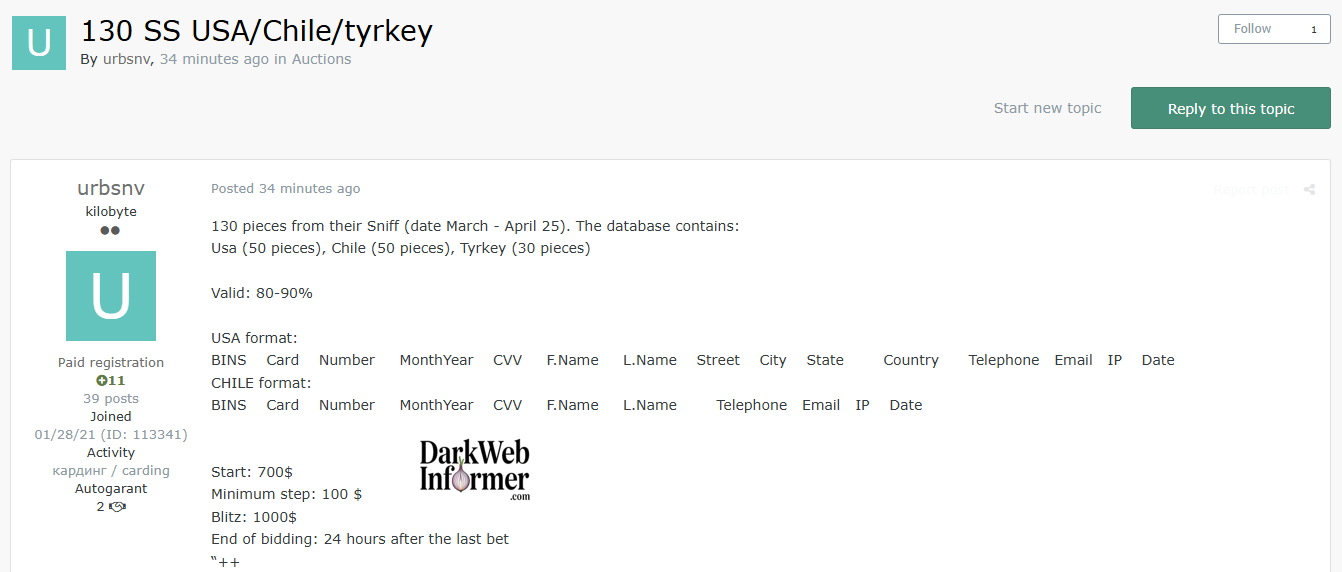
Description: Alleged Sale of Credit Card Data from Chile, Turkey, and USA
May 5th, 2025 (about 2 months ago)
|
|
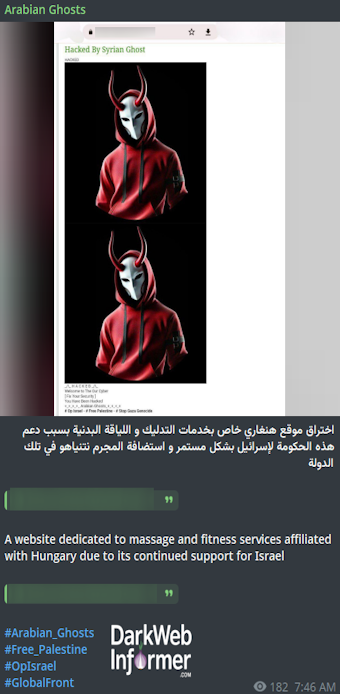
Description: Arabian Ghosts Defaced the Website of Massage Fitness Health Studio and Shop
May 5th, 2025 (about 2 months ago)
|
|
CVE-2024-58237 |
Description: In the Linux kernel, the following vulnerability has been resolved:
bpf: consider that tail calls invalidate packet pointers
Tail-called programs could execute any of the helpers that invalidate
packet pointers. Hence, conservatively assume that each tail call
invalidates packet pointers.
Making the change in bpf_helper_changes_pkt_data() automatically makes
use of check_cfg() logic that computes 'changes_pkt_data' effect for
global sub-programs, such that the following program could be
rejected:
int tail_call(struct __sk_buff *sk)
{
bpf_tail_call_static(sk, &jmp_table, 0);
return 0;
}
SEC("tc")
int not_safe(struct __sk_buff *sk)
{
int *p = (void *)(long)sk->data;
... make p valid ...
tail_call(sk);
*p = 42; /* this is unsafe */
...
}
The tc_bpf2bpf.c:subprog_tc() needs change: mark it as a function that
can invalidate packet pointers. Otherwise, it can't be freplaced with
tailcall_freplace.c:entry_freplace() that does a tail call.
EPSS Score: 0.02%
May 5th, 2025 (about 2 months ago)
|
|
CVE-2024-58100 |
Description: In the Linux kernel, the following vulnerability has been resolved:
bpf: check changes_pkt_data property for extension programs
When processing calls to global sub-programs, verifier decides whether
to invalidate all packet pointers in current state depending on the
changes_pkt_data property of the global sub-program.
Because of this, an extension program replacing a global sub-program
must be compatible with changes_pkt_data property of the sub-program
being replaced.
This commit:
- adds changes_pkt_data flag to struct bpf_prog_aux:
- this flag is set in check_cfg() for main sub-program;
- in jit_subprogs() for other sub-programs;
- modifies bpf_check_attach_btf_id() to check changes_pkt_data flag;
- moves call to check_attach_btf_id() after the call to check_cfg(),
because it needs changes_pkt_data flag to be set:
bpf_check:
... ...
- check_attach_btf_id resolve_pseudo_ldimm64
resolve_pseudo_ldimm64 --> bpf_prog_is_offloaded
bpf_prog_is_offloaded check_cfg
check_cfg + check_attach_btf_id
... ...
The following fields are set by check_attach_btf_id():
- env->ops
- prog->aux->attach_btf_trace
- prog->aux->attach_func_name
- prog->aux->attach_func_proto
- prog->aux->dst_trampoline
- prog->aux->mod
- prog->aux->saved_dst_attach_type
- prog->aux->saved_dst_prog_type
- prog->expected_attach_type
Neither of these fields are use...
EPSS Score: 0.02%
May 5th, 2025 (about 2 months ago)
|
|
CVE-2024-58098 |
Description: In the Linux kernel, the following vulnerability has been resolved:
bpf: track changes_pkt_data property for global functions
When processing calls to certain helpers, verifier invalidates all
packet pointers in a current state. For example, consider the
following program:
__attribute__((__noinline__))
long skb_pull_data(struct __sk_buff *sk, __u32 len)
{
return bpf_skb_pull_data(sk, len);
}
SEC("tc")
int test_invalidate_checks(struct __sk_buff *sk)
{
int *p = (void *)(long)sk->data;
if ((void *)(p + 1) > (void *)(long)sk->data_end) return TCX_DROP;
skb_pull_data(sk, 0);
*p = 42;
return TCX_PASS;
}
After a call to bpf_skb_pull_data() the pointer 'p' can't be used
safely. See function filter.c:bpf_helper_changes_pkt_data() for a list
of such helpers.
At the moment verifier invalidates packet pointers when processing
helper function calls, and does not traverse global sub-programs when
processing calls to global sub-programs. This means that calls to
helpers done from global sub-programs do not invalidate pointers in
the caller state. E.g. the program above is unsafe, but is not
rejected by verifier.
This commit fixes the omission by computing field
bpf_subprog_info->changes_pkt_data for each sub-program before main
verification pass.
changes_pkt_data should be set if:
- subprogram calls helper for which bpf_helper_changes_pkt_data
returns true;
- subprogram calls a global function,
fo...
EPSS Score: 0.02%
May 5th, 2025 (about 2 months ago)
|
|
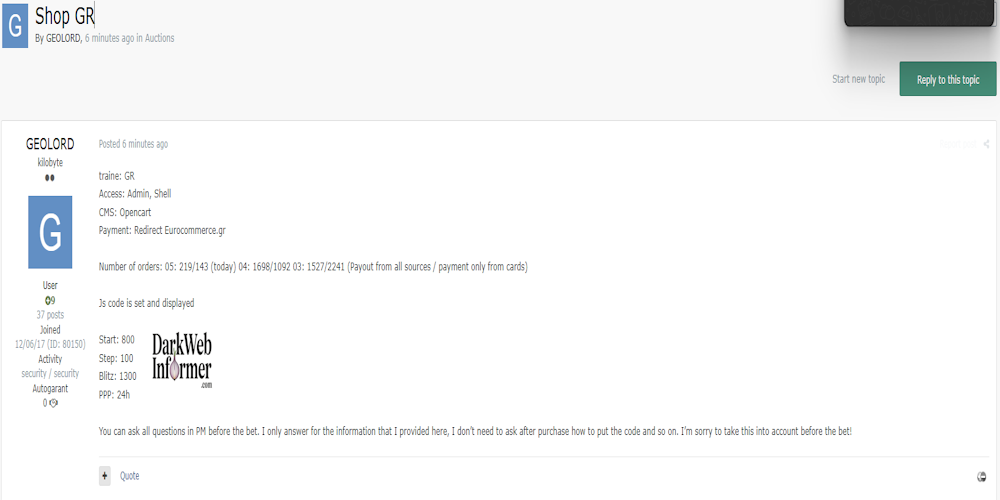
Description: Alleged Sale of Admin and Shell Access to an Unidentified Greek E-Commerce Website
May 5th, 2025 (about 2 months ago)
|
