CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-45490 |
Description: Linksys E5600 v1.1.0.26 was discovered to contain a command injection vulnerability in the runtime.ddnsStatus DynDNS function via the password parameter.
EPSS Score: 0.89%
May 6th, 2025 (about 2 months ago)
|
|
CVE-2025-45489 |
Description: Linksys E5600 v1.1.0.26 was discovered to contain a command injection vulnerability in the runtime.ddnsStatus DynDNS function via the hostname parameter.
EPSS Score: 0.89%
May 6th, 2025 (about 2 months ago)
|

|
Description: The Legal Aid Agency (LAA), an executive agency of the UK's Ministry of Justice that oversees billions in legal funding, warned law firms of a security incident and said the attackers might have accessed financial information. [...]
May 6th, 2025 (about 2 months ago)
|
|
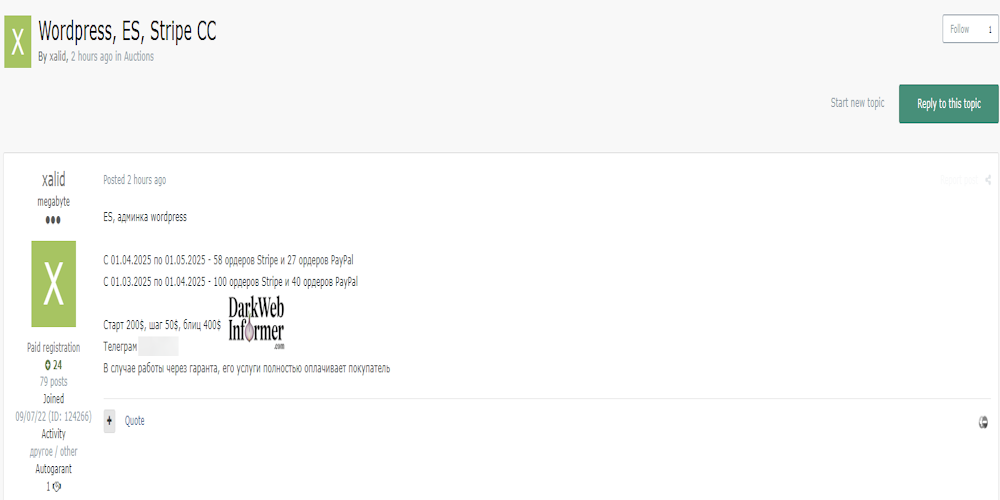
Description: Alleged Sale of WordPress Admin Access to a Spanish Website
May 6th, 2025 (about 2 months ago)
|

|
🚨 Marked as known exploited on May 6th, 2025 (about 2 months ago).
Description: The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has tagged a Langflow remote code execution vulnerability as actively exploited, urging organizations to apply security updates and mitigations as soon as possible. [...]
May 6th, 2025 (about 2 months ago)
|
|
CVE-2025-4043 |
Description: View CSAF
1. EXECUTIVE SUMMARY
CVSS v4 6.1
ATTENTION: Exploitable remotely/low attack complexity
Vendor: Milesight
Equipment: UG65-868M-EA
Vulnerability: Improper Access Control for Volatile Memory Containing Boot Code
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow any user with admin privileges to inject arbitrary shell commands.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
The following versions of UG65-868M-EA, an industrial gateway, are affected:
UG65-868M-EA: Firmware versions prior to 60.0.0.46
3.2 VULNERABILITY OVERVIEW
3.2.1 Improper Access Control for Volatile Memory Containing Boot Code CWE-1274
An admin user can gain unauthorized write access to the /etc/rc.local file on the device, which is executed on a system boot.
CVE-2025-4043 has been assigned to this vulnerability. A CVSS v3.1 base score of 6.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:N/I:H/A:N).
A CVSS v4 score has also been calculated for CVE-2025-4043. A base score of 6.1 has been calculated; the CVSS vector string is (CVSS:4.0/AV:N/AC:L/AT:N/PR:H/UI:N/VC:N/VI:N/VA:N/SC:N/SI:H/SA:N).
3.3 BACKGROUND
CRITICAL INFRASTRUCTURE SECTORS: Energy
COUNTRIES/AREAS DEPLOYED: Worldwide
COMPANY HEADQUARTERS LOCATION: China
3.4 RESEARCHER
Joe Lovett of Pen Test Partners reported this vulnerability to CISA.
4. MITIGATIONS
Milesight released the latest firmware Version 60.0.0.46 for the UG65 gateway. Users can download the latest firmware from ...
EPSS Score: 0.03%
May 6th, 2025 (about 2 months ago)
|
|
CVE-2025-4041 |
Description: View CSAF
1. EXECUTIVE SUMMARY
CVSS v4 9.3
ATTENTION: Exploitable remotely/low attack complexity
Vendor: Optigo Networks
Equipment: ONS NC600
Vulnerability: Use of Hard-coded Credentials
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow an attacker to establish an authenticated connection with the hard-coded credentials and perform OS command executions.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
The following versions of Optigo Networks ONS NC600 are affected:
ONS NC600: Versions 4.2.1-084 through 4.7.2-330
3.2 VULNERABILITY OVERVIEW
3.2.1 USE OF HARD-CODED CREDENTIALS CWE-798
In Optigo Networks ONS NC600 versions 4.2.1-084 through 4.7.2-330, an attacker could connect with the device's ssh server and utilize the system's components to perform OS command executions.
CVE-2025-4041 has been assigned to this vulnerability. A CVSS v3.1 base score of 9.8 has been calculated; the CVSS vector string is (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
A CVSS v4 score has also been calculated for CVE-2025-4041. A base score of 9.3 has been calculated; the CVSS vector string is (AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N).
3.3 BACKGROUND
CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
COUNTRIES/AREAS DEPLOYED: Worldwide
COMPANY HEADQUARTERS LOCATION: Canada
3.4 RESEARCHER
Tomer Goldschmidt of Claroty Team82 reported this vulnerability to CISA.
4. MITIGATIONS
Optigo Networks recommends users implement at least one of the following additional...
EPSS Score: 0.07%
May 6th, 2025 (about 2 months ago)
|
|
CVE-2025-3925 |
Description: View CSAF
1. EXECUTIVE SUMMARY
CVSS v4 8.5
ATTENTION: Exploitable remotely/low attack complexity
Vendor: BrightSign
Equipment: Brightsign Players
Vulnerabilities: Execution with Unnecessary Privileges
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow for privilege escalation on the device, easily guessed passwords, or for arbitrary code to be executed on the underlying operating system.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Products using the following versions of BrightSign OS are affected:
BrightSign OS series 4 players: Versions prior to v8.5.53.1
BrightSign OS series 5 players: Versions prior to v9.0.166
3.2 VULNERABILITY OVERVIEW
3.2.1 EXECUTION WITH UNNECESSARY PRIVILEGES CWE-250
BrightSign players running BrightSign OS series 4 prior to v8.5.53.1 or series 5 prior to v9.0.166 contain an execution with unnecessary privileges vulnerability, allowing for privilege escalation on the device once code execution has been obtained.
CVE-2025-3925 has been assigned to this vulnerability. A CVSS v3.1 base score of 7.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H).
A CVSS v4 score has also been calculated for CVE-2025-3925. A base score of 8.5 has been calculated; the CVSS vector string is (CVSS:4.0/AV:L/AC:L/AT:N/PR:L/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N).
3.3 BACKGROUND
CRITICAL INFRASTRUCTURE SECTORS: Commercial Facilities, Financial Services, Food and Agriculture, Healthcare and Public Health...
EPSS Score: 0.02%
May 6th, 2025 (about 2 months ago)
|

|
Description: Daniels & Taylor, P.C. is a full-service law firm in Lawrencevill
e that has been serving clients thorough Gwinnett County
We are going to upload more than 70GB of essential corporate docu
ments such as: a lot of detailed client personal information and
documents (passports, medical records, drivers licenses), confide
ntial court files, financial data of clients, NDAs, etc.
May 6th, 2025 (about 2 months ago)
|
|
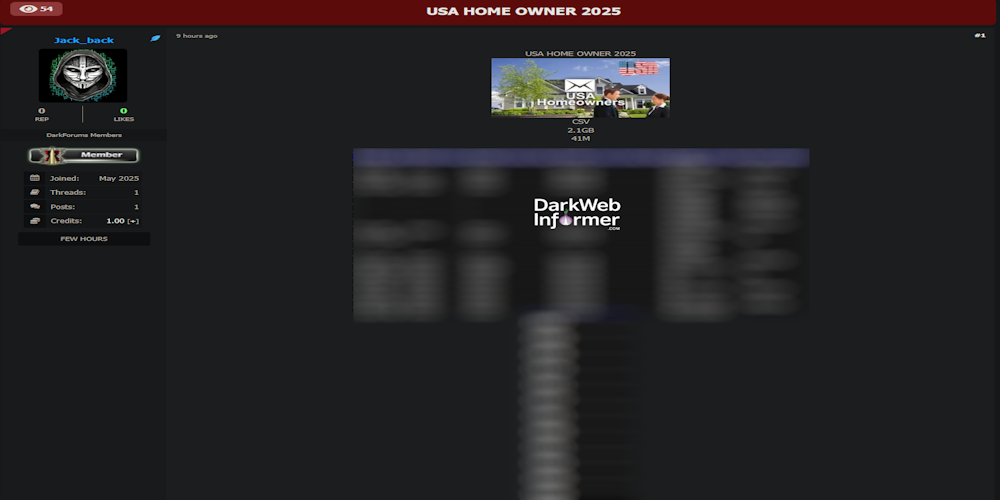
Description: Alleged Data for Sale of 41 Million American Homeowners Data
May 6th, 2025 (about 2 months ago)
|
