Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Luxury fashion brand Cartier is warning customers it suffered a data breach that exposed customers' personal information after its systems were compromised. [...]
June 2nd, 2025 (4 days ago)
|
|
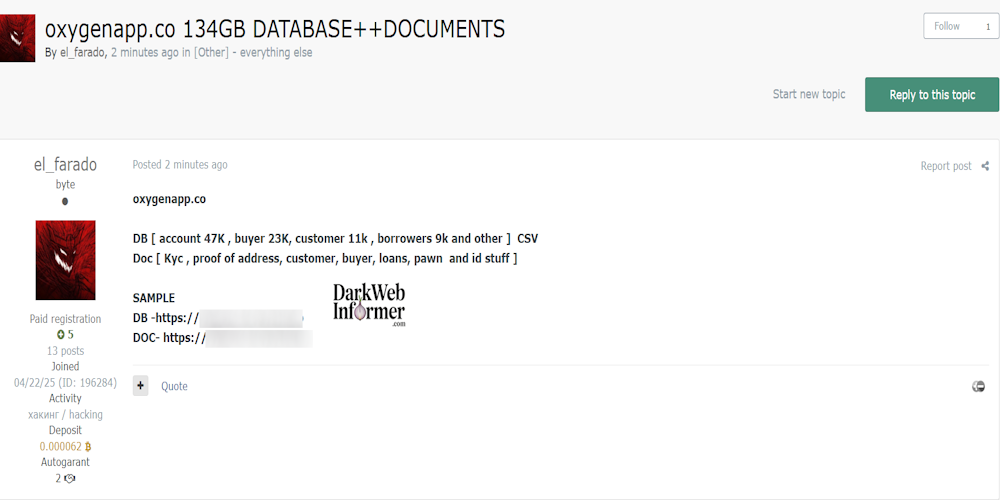
Description: Alleged data breach of Oxygen – 134GB of Financial and Identity Documents Leaked
June 2nd, 2025 (4 days ago)
|

|
Description: Outdoor gear giant The North Face has notified customers of a new credential stuffing attack that exposed personal account details, marking the second such security incident in just two months. The latest attack was detected on April 23, 2025, raising fresh concerns about the brand’s account security practices. According to the customer notice issued by …
The post The North Face Suffers New Credential Stuffing Customer Data Breach appeared first on CyberInsider.
June 2nd, 2025 (5 days ago)
|

|
Description: Pentesting isn't just about finding flaws — it's about knowing which ones matter. Pentera's 2025 State of Pentesting report uncovers which assets attackers target most, where security teams are making progress, and which exposures still fly under the radar. Focus on reducing breach impact, not just breach count. [...]
May 30th, 2025 (7 days ago)
|

|
Description: Alleged data breach of Deloitte – Internal GitHub Credentials and Source Code Leaked
May 30th, 2025 (8 days ago)
|
|
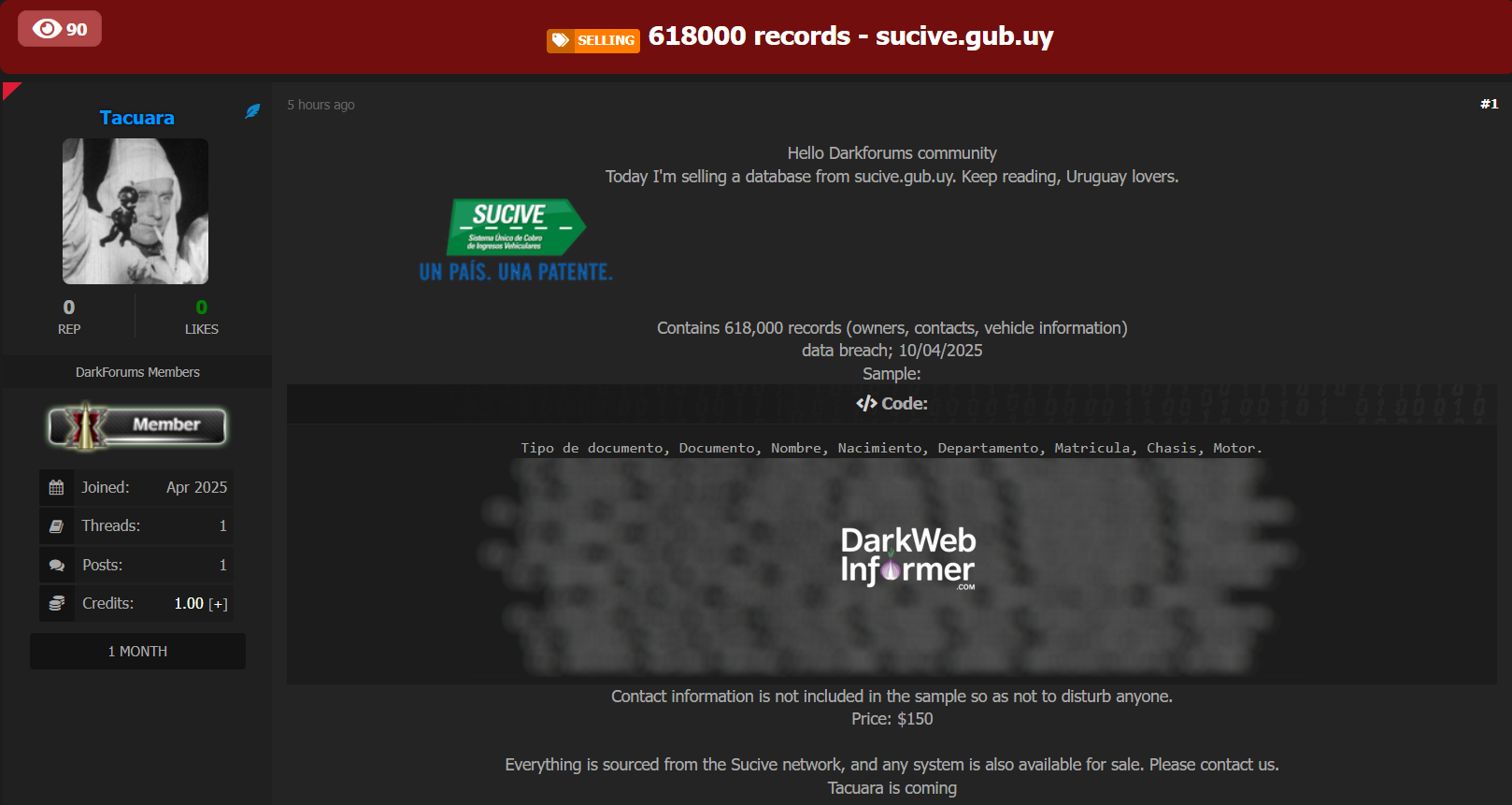
Description: Alleged data breach of Sucive – Uruguay’s Vehicle Tax and Registration Network
May 30th, 2025 (8 days ago)
|

|
Description: ConnectWise, the developer of remote access and support software ScreenConnect, has disclosed that it was the victim of a cyber attack that it said was likely perpetrated by a nation-state threat actor.
"ConnectWise recently learned of suspicious activity within our environment that we believe was tied to a sophisticated nation-state actor, which affected a very small number of ScreenConnect
May 30th, 2025 (8 days ago)
|

|
Description: IT management software firm ConnectWise says a suspected state-sponsored cyberattack breached its environment and impacted a limited number of ScreenConnect customers. [...]
May 29th, 2025 (8 days ago)
|
|
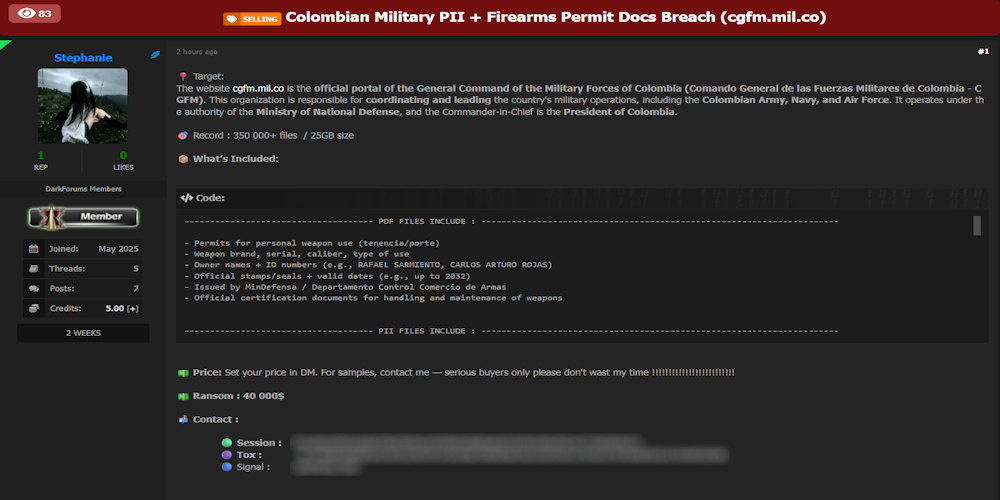
Description: Alleged data breach of Comando General de las Fuerzas Militares (cgfm.mil.co)
May 29th, 2025 (8 days ago)
|
|
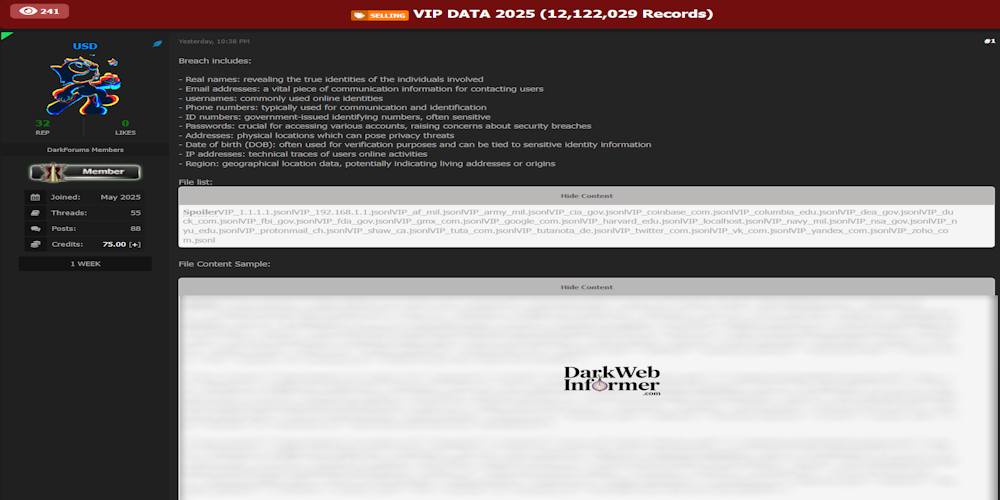
Description: Alleged data breach of VIP Data 2025 exposing over 12 million records
May 29th, 2025 (9 days ago)
|
