CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-32819 |
Description:
1) CVE-2025-32819 - Post-Authentication SSLVPN user arbitrary file delete vulnerabilityA vulnerability in SMA100 allows a remote authenticated attacker with SSLVPN user privileges to bypass the path traversal checks and delete an arbitrary file potentially resulting in a reboot to factory default settings.
CVSS Score: 8.8
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
CWE-552: Files or Directories Accessible to External Parties
2) CVE-2025-32820 - Post-Authentication SSLVPN user Path Traversal vulnerabilityA vulnerability in SMA100 allows a remote authenticated attacker with SSLVPN user privileges can inject a path traversal sequence to make any directory on the SMA appliance writable.
CVSS Score: 8.3
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:H/A:H
CWE-22: Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal')
3) CVE-2025-32821 - Post-Authentication SSLVPN admin remote command injection vulnerabilityA vulnerability in SMA100 allows a remote authenticated attacker with SSLVPN admin privileges can with admin privileges can inject shell command arguments to upload a file on the appliance.CVSS Score: 6.7
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:H/A:H
CWE-78: Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection')
SonicWall SSL VPN SMA1000 series products are not affected by these vulnerabilities. SonicWall strongly advises users of the SMA 100 series products (SMA 200, 21...
EPSS Score: 0.1%
May 7th, 2025 (about 2 months ago)
|

|
Description: Bug bounty platforms are becoming overrun with fake vulnerability reports churned out by generative AI tools, undermining trust in disclosure processes and wasting the time of maintainers — sometimes even earning payouts for bogus submissions. As highlighted in a Socket report, open source security researcher Harry Sintonen flagged a fraudulent vulnerability report submitted to the …
The post Bug Bounty Platforms Are Getting Overwhelmed by AI-Generated Submissions appeared first on CyberInsider.
May 7th, 2025 (about 2 months ago)
|

|
Description: Nominee Kirsten Davies was most recently the chief information security officer at Unilever — a role she previously held at Estee Lauder Companies.
May 7th, 2025 (about 2 months ago)
|

|
Description: The FBI has issued a FLASH alert warning of widespread exploitation of outdated home and small business routers by cybercriminal groups using the 5Socks and Anyproxy services. Threat actors are hijacking end-of-life (EOL) devices to launch attacks and sell anonymized access to compromised routers, allowing other criminals to mask their identities. This campaign targets unsupported …
The post FBI Warns Hackers Are Exploiting EoL Routers in Stealthy Malware Attacks appeared first on CyberInsider.
May 7th, 2025 (about 2 months ago)
|

|
Description: Alleged Sales of Binance Crypto Leads from USA
May 7th, 2025 (about 2 months ago)
|
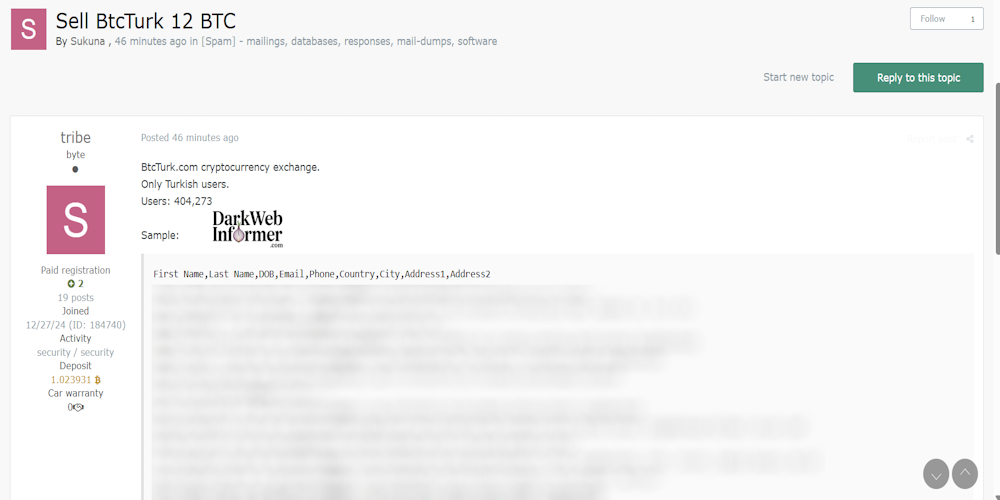
|
Description: Alleged Data for Sale of BtcTurk
May 7th, 2025 (about 2 months ago)
|
|
CVE-2025-20210 |
Description:
A vulnerability in the management API of Cisco Catalyst Center, formerly Cisco DNA Center, could allow an unauthenticated, remote attacker to read and modify the outgoing proxy configuration settings.
This vulnerability is due to the lack of authentication in an API endpoint. An attacker could exploit this vulnerability by sending a request to the affected API of a Catalyst Center device. A successful exploit could allow the attacker to view or modify the outgoing proxy configuration, which could disrupt internet traffic from Cisco Catalyst Center or may allow the attacker to intercept outbound internet traffic.
Note: For information about Cisco Catalyst Center features that require an internet connection and the corresponding internet domains used, see the Required internet URLs and fully qualified domain names section of the Cisco Catalyst Center Third-Generation Appliance Installation Guide.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-dnac-api-nBPZcJCM
Security Impact Rating: High
CVE: CVE-2025-20210
EPSS Score: 0.1%
May 7th, 2025 (about 2 months ago)
|

|
Description: Impact
Two minor vulnerabilities were identified in the Graylog2 enterprise server, which can be combined to carry out a stored cross-site scripting attack.
An attacker with the permission FILES_CREATE can exploit these vulnerabilities to upload arbitrary Javascript code to the Graylog2 server, which - upon requesting of the file by a user of the API browser - results in the execution of this Javascript code in the context of the Graylog frontend application.
This enables the attacker to carry out authenticated API requests with the permissions of the logged-in user, thereby taking over the user session.
Patches
The generic API has been removed in 6.2.0 rendering the attack vector unreachable and additional escaping has been added.
Analysis provided by Fabian Yamaguchi - Whirly Labs (Pty) Ltd
References
https://github.com/Graylog2/graylog2-server/security/advisories/GHSA-q9q2-3ppx-mwqf
https://github.com/advisories/GHSA-q9q2-3ppx-mwqf
May 7th, 2025 (about 2 months ago)
|

|
Description: Impact
It is possible to obtain user session cookies by submitting an HTML form as part of an Event Definition Remediation Step field.
For this attack to succeed, the attacker needs a user account with permissions to create event definitions, while the user must have permissions to view alerts. Additionally, an active Input must be present on the Graylog server that is capable of receiving form data (e.g. a HTTP input, TCP raw or syslog etc).
Patches
Workarounds
None, as long as the relatively rare prerequisites are met.
Analysis provided by Fabian Yamaguchi - Whirly Labs (Pty) Ltd
References
https://github.com/Graylog2/graylog2-server/security/advisories/GHSA-76vf-mpmx-777j
https://github.com/advisories/GHSA-76vf-mpmx-777j
May 7th, 2025 (about 2 months ago)
|
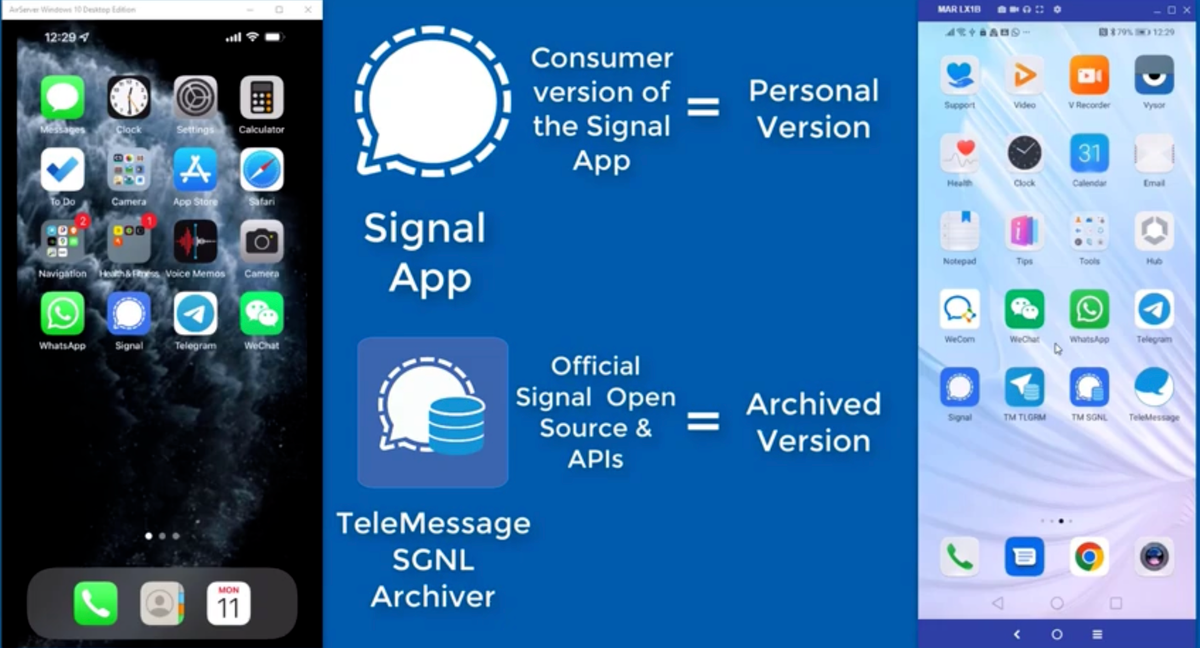
|
Description: A hacker compromised TeleMessage, a company that provides Signal chat archiving services to the Trump administration. TeleMessage has now hidden a video on YouTube that explained its Signal service.
May 7th, 2025 (about 2 months ago)
|
