CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: At least two different cybercrime groups BianLian and RansomExx are said to have exploited a recently disclosed security flaw in SAP NetWeaver, indicating that multiple threat actors are taking advantage of the bug.
Cybersecurity firm ReliaQuest, in a new update published today, said it uncovered evidence suggesting involvement from the BianLian data extortion crew and the RansomExx ransomware
May 14th, 2025 (about 1 month ago)
|

|
Description: Impact
Setting lower EVM call gas allows users to partially execute precompiles and error at specific points in the precompile code without reverting the partially written state.
If executed on the distribution precompile when claiming funds, it could cause funds to be transferred to a user without resetting the claimable rewards to 0. The vulnerability could also be used to cause indeterministic execution by failing at other points in the code, halting validators.
Any evmOS or Cosmos EVM chain using precompiles is affected.
Patches
The vulnerability was patched by wrapping each precompile execution into an atomic function that reverts any partially committed state on error.
evmos/os patch file: https://drive.google.com/file/d/1LfC0WSrQOqwTOW3qfaE6t8Jqf1PLVtS_/
For chains using a different file structure, you must manually apply the diff:
In x/evm/statedb.go:
Add the following function:
func (s *StateDB) RevertMultiStore(cms storetypes.CacheMultiStore, events sdk.Events) {
s.cacheCtx = s.cacheCtx.WithMultiStore(cms)
s.writeCache = func() {
// rollback the events to the ones
// on the snapshot
s.ctx.EventManager().EmitEvents(events)
cms.Write()
}
}
In x/evm/statedb/journal.go:
Replace the Revert function with the following:
func (pc precompileCallChange) Revert(s *StateDB) {
// rollback multi store from cache ctx to the previous
// state stored in the snapshot
s.RevertMultiStore(pc.multiStore, pc.events)
}
In prec...
May 14th, 2025 (about 1 month ago)
|

|
Description: Ransomware gangs have joined ongoing SAP NetWeaver attacks, exploiting a maximum-severity vulnerability that allows threat actors to gain remote code execution on vulnerable servers. [...]
May 14th, 2025 (about 1 month ago)
|

|
May 14th, 2025 (about 1 month ago)
|

|
Description: Remote Desktop Protocols
May 14th, 2025 (about 1 month ago)
|

|
Description: "US retailers should take note" of recent cyberattacks on British companies, according to Google's Threat Intelligence Group, as the financially motivated collective known as Scattered Spider appears to be connected.
May 14th, 2025 (about 1 month ago)
|

|
Description: A Chinese-language, Telegram-based marketplace called Xinbi Guarantee has facilitated no less than $8.4 billion in transactions since 2022, making it the second major black market to be exposed after HuiOne Guarantee.
According to a report published by blockchain analytics firm Elliptic, merchants on the marketplace have been found to peddle technology, personal data, and money laundering
May 14th, 2025 (about 1 month ago)
|

|
May 14th, 2025 (about 1 month ago)
|
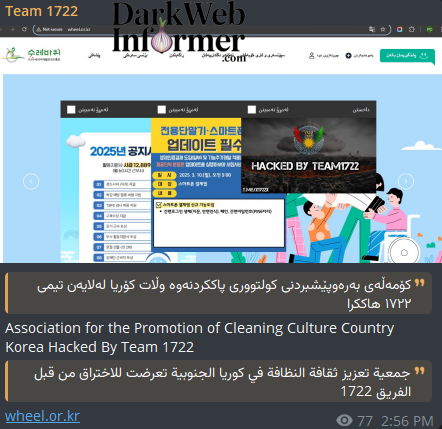
|
Description: Team 1722 Defaced the Website of The Association for the Promotion of Cleaning Culture Korea
May 14th, 2025 (about 1 month ago)
|
|
Description: The Australian Human Rights Commission (AHRC) disclosed a data breach incident where private documents leaked online and were indexed by major search engines. [...]
May 14th, 2025 (about 1 month ago)
|
