CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Nova Scotia Power confirms it suffered a data breach after threat actors stole sensitive customer data in a cybersecurity incident discovered last month. [...]
May 15th, 2025 (about 1 month ago)
|

|
May 15th, 2025 (about 1 month ago)
|

|
Description: In a deal set to close later this year, cybersecurity giant Proofpoint is acquiring German firm Hornetsecurity, which specializes in protecting companies from risks associated with Microsoft 365.
May 15th, 2025 (about 1 month ago)
|
|
CVE-2024-52877 |
Description: An issue was discovered in Insyde InsydeH2O kernel 5.2 before version 05.29.50, kernel 5.3 before version 05.38.50, kernel 5.4 before version 05.46.50, kernel 5.5 before version 05.54.50, kernel 5.6 before version 05.61.50, and kernel 5.7 before version 05.70.50. In VariableRuntimeDxe driver, callback function SmmCreateVariableLockList () calls CreateVariableLockListInSmm (). In CreateVariableLockListInSmm (), it uses StrSize () to get variable name size and it could lead to a buffer over-read.
EPSS Score: 0.04%
May 15th, 2025 (about 1 month ago)
|

|
Description: CISA released twenty-two Industrial Control Systems (ICS) advisories on May 15, 2025. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS.
ICSA-25-135-01 Siemens RUGGEDCOM APE1808 Devices
ICSA-25-135-02 Siemens INTRALOG WMS
ICSA-25-135-03 Siemens BACnet ATEC Devices
ICSA-25-135-04 Siemens Desigo
ICSA-25-135-05 Siemens SIPROTEC and SICAM
ICSA-25-135-06 Siemens Teamcenter Visualization
ICSA-25-135-07 Siemens IPC RS-828A
ICSA-25-135-08 Siemens VersiCharge AC Series EV Chargers
ICSA-25-135-09 Siemens User Management Component (UMC)
ICSA-25-135-10 Siemens OZW Web Servers
ICSA-25-135-11 Siemens Polarion
ICSA-25-135-12 Siemens SIMATIC PCS neo
ICSA-25-135-13 Siemens SIRIUS 3SK2 Safety Relays and 3RK3 Modular Safety Systems
ICSA-25-135-14 Siemens APOGEE PXC and TALON TC Series
ICSA-25-135-15 Siemens Mendix OIDC SSOICSA-25-135-16 Siemens MS/TP Point Pickup Module
ICSA-25-135-16 Siemens MS/TP Point Pickup Module
ICSA-25-135-17 Siemens RUGGEDCOM ROX II
ICSA-25-135-18 Siemens SCALANCE LPE9403
ICSA-25-135-19 ECOVACS DEEBOT Vacuum and Base Station
ICSA-25-135-20 Schneider Electric EcoStruxure Power Build Rapsody
ICSA-24-135-04 Mitsubishi Electric Multiple FA Engineering Software Products (Update C)
ICSA-24-200-01 Mitsubishi Electric MELSOFT MaiLab and MELSOFT VIXIO (Update A)
CISA encourages users and administrators to review newly released ICS advisories for technical details and mitigations.
May 15th, 2025 (about 1 month ago)
|
|
CVE-2024-3596 |
Description: As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens' ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
View CSAF
1. EXECUTIVE SUMMARY
CVSS v4 9.1
ATTENTION: Exploitable remotely/low attack complexity
Vendor: Siemens
Equipment: SIPROTEC and SICAM
Vulnerability: Improper Enforcement of Message Integrity During Transmission in a Communication Channel
2. RISK EVALUATION
Successful exploitation of this vulnerability could cause the network access server to grant the attacker access to the network with the attacker's desired authorization and without the need of knowing or guessing legitimate access credentials.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Siemens reports the following products using the RADIUS protocol are affected:
CPC80 Central Processing/Communication: All versions
CPCI85 Central Processing/Communication: All versions
POWER METER SICAM Q100 family: All versions prior to V2.70
POWER METER SICAM Q200 family: All versions
Powerlink IP: All versions
SICAM GridPass: All versions prior to V2.50
SICORE Base system: All versions
SIPROTEC 5 Compact 7SX800 (CP050): All versions
SIPROTEC 5 7SA82 (CP100): Versions V7.80 and after
SIPROTEC 5 7SD82 (CP100): Versions V7.80 and after
SIPROTEC 5 7SJ81 (CP100): Versions V7.80 and after
SIPROTEC 5 7SJ82 (CP100): Versi...
May 15th, 2025 (about 1 month ago)
|
|
CVE-2025-30198 |
Description: View CSAF
1. EXECUTIVE SUMMARY
CVSS v4 8.6
ATTENTION: Exploitable remotely/low attack complexity
Vendor: ECOVACS
Equipment: DEEBOT Vacuum and Base Station
Vulnerabilities: Use of Hard-coded Cryptographic Key, Download of Code Without Integrity Check
2. RISK EVALUATION
Successful exploitation of these vulnerabilities could allow an attacker to send malicious updates to the devices or execute code.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
ECOVACS reports the following DEEBOT vacuum and base station devices are affected:
X1S PRO: Versions prior to 2.5.38
X1 PRO OMNI: Versions prior to 2.5.38
X1 OMNI: Versions prior to 2.4.45
X1 TURBO: Versions prior to 2.4.45
T10 Series: Versions prior to 1.11.0
T20 Series: Versions prior to 1.25.0
T30 Series: Versions prior to 1.100.0
3.2 VULNERABILITY OVERVIEW
3.2.1 Use of Hard-coded Cryptographic Key CWE-321
ECOVACS robot vacuums and base stations communicate via an insecure Wi-Fi network with a deterministic WPA2-PSK. The key can be easily derived from the device serial number.
CVE-2025-30198 has been assigned to this vulnerability. A CVSS v3.1 base score of 6.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L).
A CVSS v4 score has also been calculated for CVE-2025-30198. A base score of 5.3 has been calculated; the CVSS vector string is (CVSS:4.0/AV:A/AC:L/AT:N/PR:N/UI:N/VC:L/VI:L/VA:L/SC:N/SI:N/SA:N).
3.2.2 Download of Code Without Integrity Check CWE-494
ECOVACS vacuum robot base statio...
May 15th, 2025 (about 1 month ago)
|

|
Description: On the first day of Pwn2Own Berlin 2025, security researchers were awarded $260,000 after successfully demonstrating zero-day exploits for Windows 11, Red Hat Linux, Docker Desktop, and Oracle VirtualBox. [...]
May 15th, 2025 (about 1 month ago)
|

|
Description: "Thinking about your ex 24/7? There's nothing wrong with you. Chat with their AI version—and finally let it go," an ad for Closure says. I tested a bunch of the chatbot startups' personas.
May 15th, 2025 (about 1 month ago)
|
|
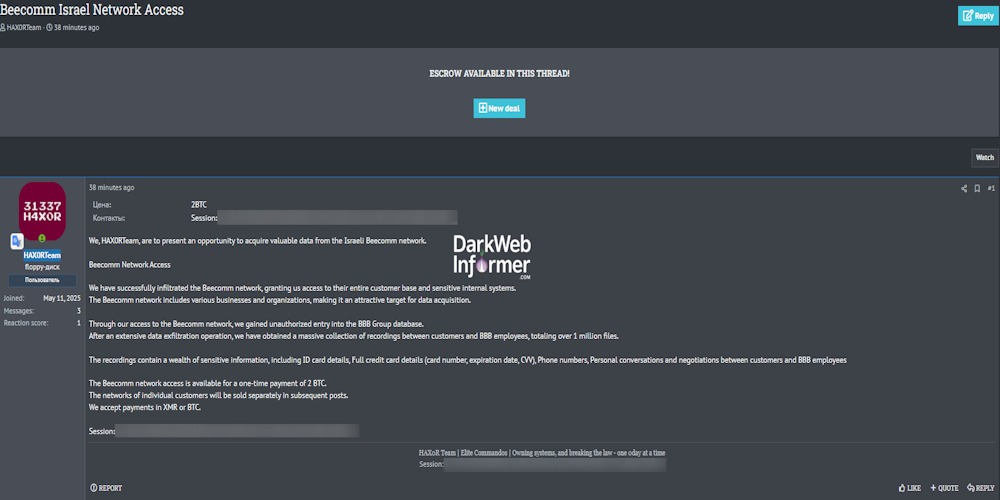
Description: Alleged Sale of Access to Beecomm’s Internal Network
May 15th, 2025 (about 1 month ago)
|
