Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
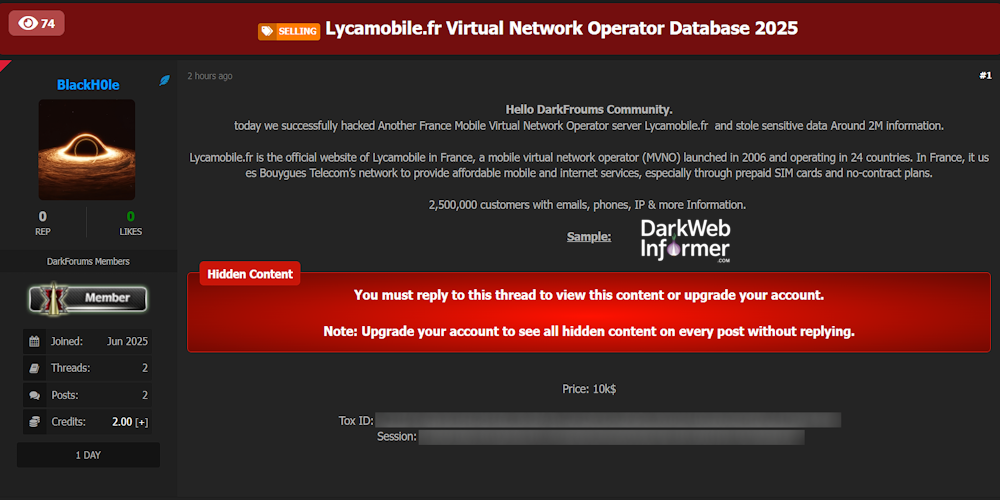
Description: Alleged data breach of Lyca Mobile France – 2.5 Million Customer Records for Sale
June 4th, 2025 (3 days ago)
|

|
Description: Publishing giant Lee Enterprises is notifying over 39,000 people whose personal information was stolen in a February 2025 ransomware attack. [...]
June 4th, 2025 (3 days ago)
|

|
Description: The parent company of apparel brand The North Face sent data breach notification letters to about 3,000 customer accounts, saying attackers used the technique known as credential stuffing.
June 4th, 2025 (3 days ago)
|

|
Description: In this fifth installment of Tenable’s “Stronger Cloud Security in Five” blog series, we offer three best practices for quickly hardening your Kubernetes environment’s security in GCP: remove wide inbound access to cluster APIs; remove root permissions from containers; and remove privileged permissions from publicly accessible groups. Securing your Kubernetes environment is critical in order to protect your cloud application development lifecycle and your container orchestration. However, properly configuring and managing Kubernetes is complicated, and this often leads to lax security controls that put organizations at an elevated risk for a breach.As the “Tenable Cloud Risk Report 2024” found, security weaknesses in Kubernetes environments aren’t the exception – they’re the norm:78% of organizations have publicly accessible Kubernetes API servers, and 41% of those are set to allow inbound internet access.44% run privileged containers, which have access to the host’s resources and kernel capabilities, making them a major risk if attackers gain access to them.58% have cluster-admin role bindings, which give some users complete control over all of their organizations’ Kubernetes environments.Here we outline three best practices that take no more than five minutes to implement and that’ll quickly boost the security of your Google Cloud Platform’s (GCP) Kubernetes environment. Read on!Remove wide inbound access to clusters’ APIsThe Google Kubernetes Engine (GKE) API lets you q...
June 4th, 2025 (3 days ago)
|

|
Description: With its head office in Salzgitter, funktel GmbH is a leading manufacturer of professional security and communication solutions based on DECT and TETRA for industry, public utilities and authorities.
funktel GmbH become a victim of the largest data breach. 3.5TB sensitive data will be published soon in our blog.
June 4th, 2025 (3 days ago)
|

|
Description: [AI generated] Jordan Kuwait Bank is a leading banking institution that offers financial and banking services. The mention of "full leak published" suggests there might've been an incident where confidential information could have been exposed or compromised, potentially impacting the bank's security and client information. Note: any data breach allegations should be thoroughly researched for verification.
June 4th, 2025 (3 days ago)
|

|
Description: A recently disclosed data breach at Coinbase has been linked to India-based customer support representatives from outsourcing firm TaskUs, who threat actors bribed to steal data from the crypto exchange. [...]
June 3rd, 2025 (3 days ago)
|

|
Description: Alleged data breach of Claro – 15.4 Million Customer Records Breached
June 3rd, 2025 (4 days ago)
|

|
Description: Luxury jewelry brand Cartier has disclosed a data breach that exposed customer information, warning clients via email that unauthorized actors gained temporary access to its systems. The company emphasized that no passwords, credit card numbers, or banking details were compromised. The breach was identified by Cartier’s internal security team, who discovered that an intruder had …
The post Cartier Alerts Customers of Data Breach Exposing Personal Information appeared first on CyberInsider.
June 3rd, 2025 (4 days ago)
|

|
Description: In May 2025, hosting provider ColoCrossing identified a data breach that impacted customers of their ColoCloud virtual server product. ColoCrossing advised the incident was isolated to their cloud/VPS platform and stemmed from a single sign-on vulnerability. 7k email addresses were exposed in the incident along with names and MD5-Crypt password hashes.
June 3rd, 2025 (4 days ago)
|
