CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Cybersecurity researchers are calling attention to a new botnet malware called HTTPBot that has been used to primarily single out the gaming industry, as well as technology companies and educational institutions in China.
"Over the past few months, it has expanded aggressively, continuously leveraging infected devices to launch external attacks," NSFOCUS said in a report published this week. "By
May 16th, 2025 (27 days ago)
|

|
Description: The shirts will be returned to China or will be “destroyed under CBP supervision."
May 15th, 2025 (28 days ago)
|

|
Description: Senate Intelligence Committee Chairman Tom Cotton and 16 other GOP lawmakers wrote this week to Commerce Secretary Howard Lutnick, saying his department should block future sales of TP-Link’s popular small office/home office (SOHO) internet routers.
May 15th, 2025 (28 days ago)
|

|
Description: New research shows China is quickly catching up with the US in AI innovation. Experts weigh in on what it means for cyber defenders.
May 12th, 2025 (about 1 month ago)
|

|
Description: Explore Insikt Group's in-depth 2025 report on the US-China AI race—comparing funding, talent, regulation, compute capacity, and model benchmarks. Discover why China trails the US and what could change before 2030.
May 8th, 2025 (about 1 month ago)
|

|
Description: Japan is being peppered with an overwhelming volume of spam, thanks to a new platform popular across the East China Sea.
May 8th, 2025 (about 1 month ago)
|

|
Description: Pat McFadden, the most senior minister in Britain’s Cabinet Office, told the CYBERUK conference that Beijing had “the sophistication, the scale and the seriousness” to pose an exceptional national security challenge.
May 7th, 2025 (about 1 month ago)
|
|
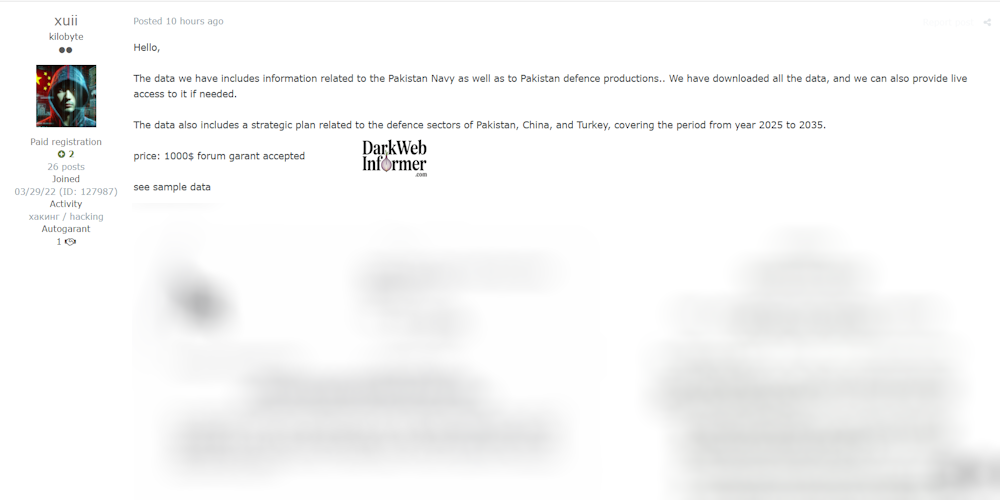
Description: Alleged Sale of Confidential Pakistan Defense Production Data, Including Strategic Plans with China and Turkey
May 6th, 2025 (about 1 month ago)
|
|
CVE-2025-4043 |
Description: View CSAF
1. EXECUTIVE SUMMARY
CVSS v4 6.1
ATTENTION: Exploitable remotely/low attack complexity
Vendor: Milesight
Equipment: UG65-868M-EA
Vulnerability: Improper Access Control for Volatile Memory Containing Boot Code
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow any user with admin privileges to inject arbitrary shell commands.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
The following versions of UG65-868M-EA, an industrial gateway, are affected:
UG65-868M-EA: Firmware versions prior to 60.0.0.46
3.2 VULNERABILITY OVERVIEW
3.2.1 Improper Access Control for Volatile Memory Containing Boot Code CWE-1274
An admin user can gain unauthorized write access to the /etc/rc.local file on the device, which is executed on a system boot.
CVE-2025-4043 has been assigned to this vulnerability. A CVSS v3.1 base score of 6.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:N/I:H/A:N).
A CVSS v4 score has also been calculated for CVE-2025-4043. A base score of 6.1 has been calculated; the CVSS vector string is (CVSS:4.0/AV:N/AC:L/AT:N/PR:H/UI:N/VC:N/VI:N/VA:N/SC:N/SI:H/SA:N).
3.3 BACKGROUND
CRITICAL INFRASTRUCTURE SECTORS: Energy
COUNTRIES/AREAS DEPLOYED: Worldwide
COMPANY HEADQUARTERS LOCATION: China
3.4 RESEARCHER
Joe Lovett of Pen Test Partners reported this vulnerability to CISA.
4. MITIGATIONS
Milesight released the latest firmware Version 60.0.0.46 for the UG65 gateway. Users can download the latest firmware from ...
EPSS Score: 0.03%
May 6th, 2025 (about 1 month ago)
|

|
May 4th, 2025 (about 1 month ago)
|
