CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Arch Linux has pulled three malicious packages uploaded to the Arch User Repository (AUR) were used to install the CHAOS remote access trojan (RAT) on Linux devices. [...]
July 18th, 2025 (1 day ago)
|

|
Description: CB Machining & Engineering specializes in providing contract manufacturing services, including contract milling, turning, assembly, and supply chain management. Located in Buffalo, Minnesota, the company serves customers in industries such as aerospace, defense, medical, and energy.
July 18th, 2025 (1 day ago)
|

|
Description: CB Machining & Engineering specializes in providing contract manufacturing services, including contract milling, turning, assembly, and supply chain management. Located in Buffalo, Minnesota, the company serves customers in industries such as aerospace, defense, medical, and energy.
July 18th, 2025 (1 day ago)
|

|
Description: Anderson & Karrenberg is a law firm that focuses on representing its clients' interests and achieving results for them. The firm uses its collective knowledge and experience to provide legal services. The firm serves clients who expect high standards and results. The firm is based in Salt Lake City, Utah.
July 18th, 2025 (1 day ago)
|
|
CVE-2025-50708 |
Description: An issue in Perplexity AI GPT-4 v.2.51.0 allows a remote attacker to obtain sensitive information via the token component in the shared chat URL
EPSS Score: 0.05%
July 18th, 2025 (1 day ago)
|
|
CVE-2025-50584 |
Description: StudentManage v1.0 was discovered to contain a cross-site scripting (XSS) vulnerability via the Add A New Teacher module.
EPSS Score: 0.02%
July 18th, 2025 (1 day ago)
|

|
Description: Alleged Data Breach of Hubla
July 18th, 2025 (1 day ago)
|
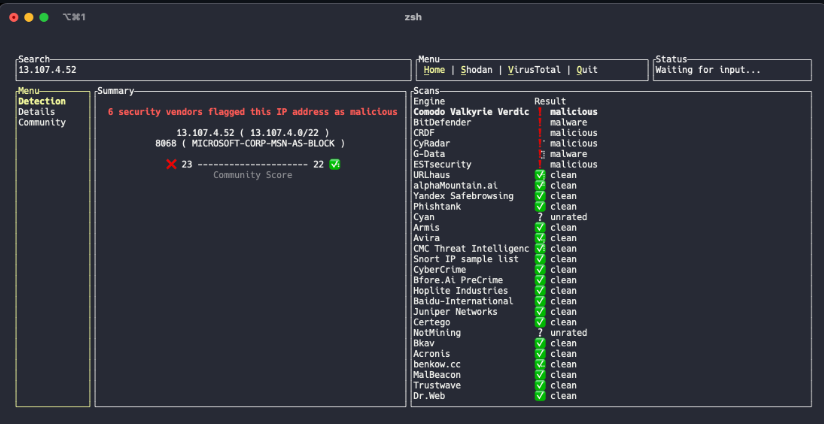
|
Description: osintui: Open Source Intelligence Terminal User Interface
July 18th, 2025 (1 day ago)
|

|
Description: Alleged Data Breach of the European Economic Association (EEA)
July 18th, 2025 (1 day ago)
|

|
Description: A top official did not disclose details of UNC3886’s activity but said “it is serious and it’s ongoing … and we will assess whether it is in our interest to disclose more details later.”
July 18th, 2025 (1 day ago)
|
