CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: TBD
May 19th, 2025 (about 1 month ago)
|

|
Description: TBD
May 19th, 2025 (about 1 month ago)
|

|
Description: TBD
May 19th, 2025 (about 1 month ago)
|

|
Description: The Pwn2Own Berlin 2025 hacking competition has concluded, with security researchers earning $1,078,750 after exploiting 29 zero-day vulnerabilities and encountering some bug collisions. [...]
May 19th, 2025 (about 1 month ago)
|

|
Description: Mozilla released emergency security updates to address two Firefox zero-day vulnerabilities demonstrated in the recent Pwn2Own Berlin 2025 hacking competition. [...]
May 19th, 2025 (about 1 month ago)
|
|
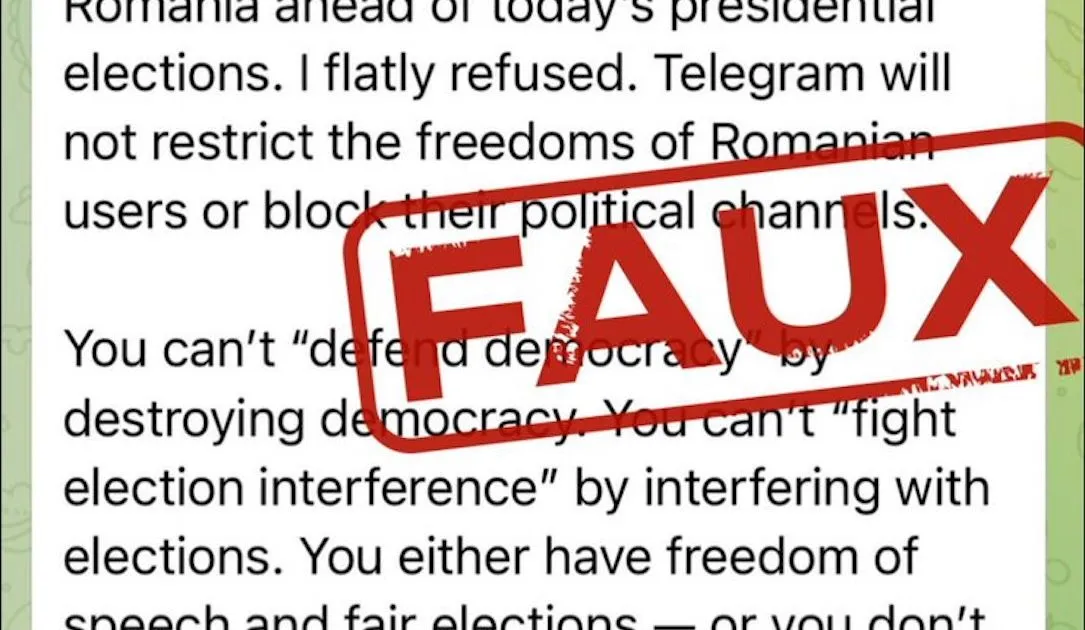
Description: France's foreign ministry said it "categorically rejects" a statement by Telegram's Pavel Durov that French intelligence had asked him to ban conservative voices in Romania ahead of its elections.
May 19th, 2025 (about 1 month ago)
|

|
Description: The tool scans for users writing certain keywords on Reddit and assigns those users a so-called “radical score,” before deploying an AI-powered bot to automatically engage with the users to de-radicalize them.
May 19th, 2025 (about 1 month ago)
|

|
Description: Mantis Creative. Visualization and creative solutions for real es
tate projects and tomorrow's emerging brands. Mantis is a leading
arch-viz & creative agency in north america, transforming ideas
into high-performing brands built to conquer their environments.
We are going to upload more than 45 GB of corporate documents suc
h as: contracts, client data, projects, some financial data, etc.
May 19th, 2025 (about 1 month ago)
|

|
Description: At the RSA Conference in San Francisco this year, Tim Brown talked about the protection CISOs need, Russia’s continued attempts to launch attacks and how companies can navigate the treacherous waters of cyber incidents.
May 19th, 2025 (about 1 month ago)
|

|
Description: Each Monday, the Tenable Exposure Management Academy provides the practical, real-world guidance you need to shift from vulnerability management to exposure management. In this Exposure Management Academy FAQ, we help CISOs understand exposure management, look at how advanced you might be and outline how to structure a program. You can read the entire Exposure Management Academy series here.Since we started the Exposure Management Academy in March, we’ve received lots of questions. To provide answers, we launched an exposure management FAQ series in April and we’re following that with a few more questions and answers. Do you have a question about exposure management? If so, fill out the form at the bottom of this page and we’ll address your question in a future post.I’m a CISO. What should I know about exposure management?This is a fundamental question we hear from many CISOs. In short, exposure management offers CISOs a unified view of the most significant cyber exposures across their organization’s entire attack surface. Toxic combinations of preventable weaknesses — including vulnerabilities, misconfigurations and excessive permissions — can lead to substantial business exposure if they’re exploited. To effectively practice exposure management, you need to be able to identify these toxic risk combinations that create attack paths leading to your most valuable assets or administrative privileges. Implementing an exposure management program can help you streamline priorit...
May 19th, 2025 (about 1 month ago)
|
