Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-20130 |
Description:
A vulnerability in the API of Cisco Identity Services Engine (ISE) and Cisco ISE Passive Identity Connector (ISE-PIC) could allow an authenticated, remote attacker with administrative privileges to upload files to an affected device.
This vulnerability is due to improper validation of the file copy function. An attacker could exploit this vulnerability by sending a crafted file upload request to a specific API endpoint. A successful exploit could allow the attacker to upload arbitrary files to an affected system.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ise-file-upload-P4M8vwXY
Security Impact Rating: Medium
CVE: CVE-2025-20130
EPSS Score: 0.03%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20163 |
Description:
A vulnerability in the SSH implementation of Cisco Nexus Dashboard Fabric Controller (NDFC) could allow an unauthenticated, remote attacker to impersonate Cisco NDFC-managed devices.
This vulnerability is due to insufficient SSH host key validation. An attacker could exploit this vulnerability by performing a machine-in-the-middle attack on SSH connections to Cisco NDFC-managed devices, which could allow an attacker to intercept this traffic. A successful exploit could allow the attacker to impersonate a managed device and capture user credentials.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ndfc-shkv-snQJtjrp
Security Impact Rating: High
CVE: CVE-2025-20163
EPSS Score: 0.02%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20259 |
Description:
Multiple vulnerabilities in the update process of Cisco ThousandEyes Endpoint Agent for Windows could allow an authenticated, local attacker to delete arbitrary files on an affected device.
These vulnerabilities are due to improper access controls on files that are in the local file system. An attacker could exploit these vulnerabilities by using a symbolic link to perform an agent upgrade that redirects the delete operation of any protected file. A successful exploit could allow the attacker to delete arbitrary files from the file system of the affected device.
Cisco has released software updates that address these vulnerabilities. There are no workarounds that address these vulnerabilities.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-te-endagent-filewrt-zNcDqNRJ
Security Impact Rating: Medium
CVE: CVE-2025-20259
EPSS Score: 0.03%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20275 |
Description:
A vulnerability in the file opening process of Cisco Unified Contact Center Express (Unified CCX) Editor could allow an unauthenticated attacker to execute arbitrary code on an affected device.
This vulnerability is due to insecure deserialization of Java objects by the affected software. An attacker could exploit this vulnerability by persuading an authenticated, local user to open a crafted .aef file. A successful exploit could allow the attacker to execute arbitrary code on the host that is running the editor application with the privileges of the user who launched it.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-uccx-editor-rce-ezyYZte8
Security Impact Rating: Medium
CVE: CVE-2025-20275
EPSS Score: 0.06%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20276 |
Description:
Multiple vulnerabilities in the web-based management interface of Cisco Unified Contact Center Express (Unified CCX) could allow an authenticated, remote attacker to perform a stored cross-site scripting (XSS) attack or execute arbitrary code on an affected device. To exploit these vulnerabilities, the attacker must have valid administrative credentials.
For more information about these vulnerabilities, see the Details section of this advisory.
Cisco has released software updates that address these vulnerabilities. There are no workarounds that address these vulnerabilities.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-uccx-multi-UhOTvPGL
Security Impact Rating: Medium
CVE: CVE-2025-20276,CVE-2025-20277,CVE-2025-20279
EPSS Score: 0.11%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20278 |
Description:
A vulnerability in the CLI of multiple Cisco Unified Communications products could allow an authenticated, local attacker to execute arbitrary commands on the underlying operating system of an affected device as the root user.
This vulnerability is due to improper validation of user-supplied command arguments. An attacker could exploit this vulnerability by executing crafted commands on the CLI of an affected device. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system of an affected device as the root user. To exploit this vulnerability, the attacker must have valid administrative credentials.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-vos-command-inject-65s2UCYy
Security Impact Rating: Medium
CVE: CVE-2025-20278
EPSS Score: 0.01%
June 4th, 2025 (3 days ago)
|
|
CVE-2025-20129 |
Description:
A vulnerability in the web-based chat interface of Cisco Customer Collaboration Platform (CCP), formerly Cisco SocialMiner, could allow an unauthenticated, remote attacker to persuade users to disclose sensitive data.
This vulnerability is due to improper sanitization of HTTP requests that are sent to the web-based chat interface. An attacker could exploit this vulnerability by sending crafted HTTP requests to the chat interface of a targeted user on a vulnerable server. A successful exploit could allow the attacker to redirect chat traffic to a server that is under their control, resulting in sensitive information being redirected to the attacker.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ccp-info-disc-ZyGerQpd
Security Impact Rating: Medium
CVE: CVE-2025-20129
EPSS Score: 0.07%
June 4th, 2025 (3 days ago)
|

|
Description: Google's Threat Intelligence Group (GTIG) revealed that financially motivated threat actors are exploiting Mullvad VPN to mask data exfiltration operations targeting Salesforce environments. The attackers, tracked under the cluster UNC6040, have successfully compromised multiple organizations by leveraging voice phishing (vishing) tactics to gain unauthorized access to sensitive cloud data. UNC6040's campaigns have been active for …
The post Hackers Abuse Mullvad VPN to Steal Salesforce Data from Companies appeared first on CyberInsider.
June 4th, 2025 (3 days ago)
|
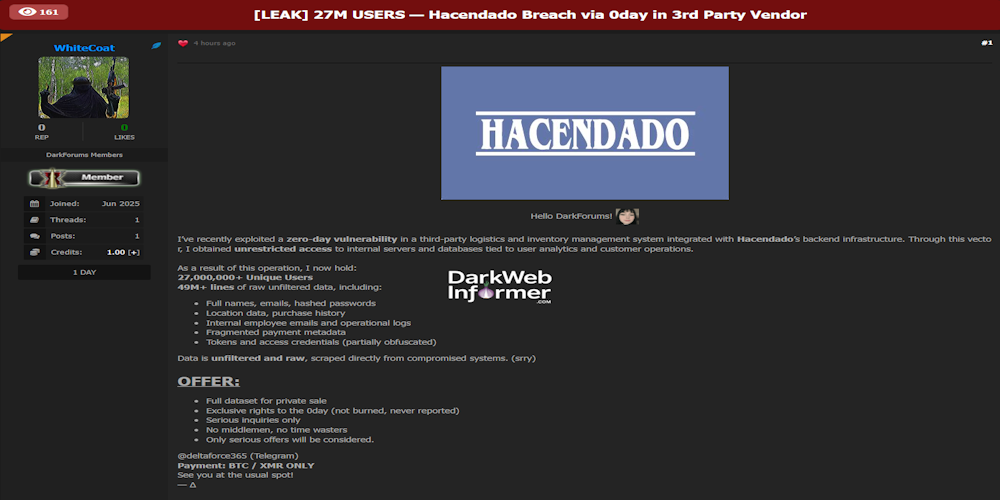
|
Description: Alleged breach of Hacendado via 0-day in third-party vendor – 27M User Records Exposed
June 4th, 2025 (3 days ago)
|

|
Description: [AI generated] J-Kraft, Inc. is a manufacturing company based in Houston, Texas. They produce high-quality, custom-made doors and millwork for both residential and commercial applications. Since 1990, they've combined advanced technology with skilled artisanship to deliver superior products. They value customer satisfaction, quality craftsmanship, and attention to detail.
June 4th, 2025 (3 days ago)
|
