CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Access expert insights on how brand impersonation, online ads, and malicious merchants help a purchase scam network prey on victims
May 20th, 2025 (about 1 month ago)
|

|
Description: SK Telecom says that a recently disclosed cybersecurity incident in April, first occurred all the way back in 2022, ultimately exposing the USIM data of 27 million subscribers. [...]
May 20th, 2025 (about 1 month ago)
|

|
Description: A threat actor known as Hazy Hawk has been observed hijacking abandoned cloud resources of high-profile organizations, including Amazon S3 buckets and Microsoft Azure endpoints, by leveraging misconfigurations in the Domain Name System (DNS) records.
The hijacked domains are then used to host URLs that direct users to scams and malware via traffic distribution systems (TDSes), according to
May 20th, 2025 (about 1 month ago)
|

|
Description: Rommel's Ace is part of Rommel Holdings, Inc., a mid-sized holdin
g company located in Fruitland, MD. Rommel Holdings has owned and
operated a variety of businesses dating back to the 1950's.
We are going to upload about 2 GB of corporate data. This is not
much but there is so much personal information of almost every em
ployee including terminated ones. Passport numbers, addresses, pe
rsonal emails, SSNs, medical records and is on. You will also fin
d a lot of accounting and projects files of Rommel Electric and R
ommel Harley - Davidson companies.
May 20th, 2025 (about 1 month ago)
|
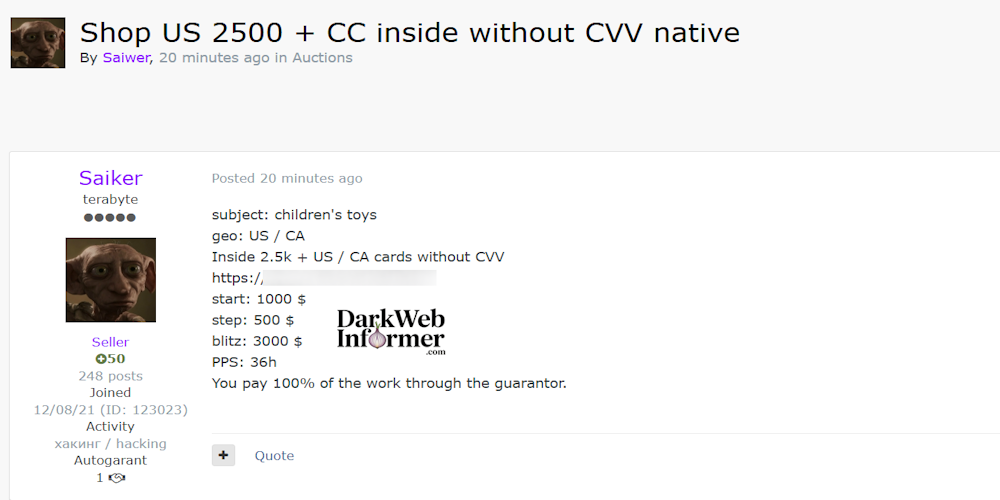
|
Description: Alleged Sale of Credit Card Records from USA and Canada
May 20th, 2025 (about 1 month ago)
|

|
Description: Civitai, a huge platform for sharing AI models and generating videos and images, has been cut off from its payment processor.
May 20th, 2025 (about 1 month ago)
|
|
CVE-2025-37922 |
🚨 Marked as known exploited on May 20th, 2025 (about 1 month ago).
Description: In the Linux kernel, the following vulnerability has been resolved:
book3s64/radix : Align section vmemmap start address to PAGE_SIZE
A vmemmap altmap is a device-provided region used to provide
backing storage for struct pages. For each namespace, the altmap
should belong to that same namespace. If the namespaces are
created unaligned, there is a chance that the section vmemmap
start address could also be unaligned. If the section vmemmap
start address is unaligned, the altmap page allocated from the
current namespace might be used by the previous namespace also.
During the free operation, since the altmap is shared between two
namespaces, the previous namespace may detect that the page does
not belong to its altmap and incorrectly assume that the page is a
normal page. It then attempts to free the normal page, which leads
to a kernel crash.
Kernel attempted to read user page (18) - exploit attempt? (uid: 0)
BUG: Kernel NULL pointer dereference on read at 0x00000018
Faulting instruction address: 0xc000000000530c7c
Oops: Kernel access of bad area, sig: 11 [#1]
LE PAGE_SIZE=64K MMU=Radix SMP NR_CPUS=2048 NUMA pSeries
CPU: 32 PID: 2104 Comm: ndctl Kdump: loaded Tainted: G W
NIP: c000000000530c7c LR: c000000000530e00 CTR: 0000000000007ffe
REGS: c000000015e57040 TRAP: 0300 Tainted: G W
MSR: 800000000280b033 CR: 84482404
CFAR: c000000000530dfc DAR: 0000000000000018 DSISR: 40000000 IRQMASK: 0
GPR00: c000000000530e00 c000000015e572e0 c000000002c5cb00 c00c00...
EPSS Score: 0.02%
May 20th, 2025 (about 1 month ago)
|
|
CVE-2025-37921 |
Description: In the Linux kernel, the following vulnerability has been resolved:
vxlan: vnifilter: Fix unlocked deletion of default FDB entry
When a VNI is deleted from a VXLAN device in 'vnifilter' mode, the FDB
entry associated with the default remote (assuming one was configured)
is deleted without holding the hash lock. This is wrong and will result
in a warning [1] being generated by the lockdep annotation that was
added by commit ebe642067455 ("vxlan: Create wrappers for FDB lookup").
Reproducer:
# ip link add vx0 up type vxlan dstport 4789 external vnifilter local 192.0.2.1
# bridge vni add vni 10010 remote 198.51.100.1 dev vx0
# bridge vni del vni 10010 dev vx0
Fix by acquiring the hash lock before the deletion and releasing it
afterwards. Blame the original commit that introduced the issue rather
than the one that exposed it.
[1]
WARNING: CPU: 3 PID: 392 at drivers/net/vxlan/vxlan_core.c:417 vxlan_find_mac+0x17f/0x1a0
[...]
RIP: 0010:vxlan_find_mac+0x17f/0x1a0
[...]
Call Trace:
__vxlan_fdb_delete+0xbe/0x560
vxlan_vni_delete_group+0x2ba/0x940
vxlan_vni_del.isra.0+0x15f/0x580
vxlan_process_vni_filter+0x38b/0x7b0
vxlan_vnifilter_process+0x3bb/0x510
rtnetlink_rcv_msg+0x2f7/0xb70
netlink_rcv_skb+0x131/0x360
netlink_unicast+0x426/0x710
netlink_sendmsg+0x75a/0xc20
__sock_sendmsg+0xc1/0x150
____sys_sendmsg+0x5aa/0x7b0
___sys_sendmsg+0xfc/0x180
__sys_sendmsg+0x121/0x1b0
do_syscall_64+0xbb/0x1d0
entry_SYSCALL_64_after_hwframe+0x4b/0x53
EPSS Score: 0.04%
May 20th, 2025 (about 1 month ago)
|
|
CVE-2025-37920 |
Description: In the Linux kernel, the following vulnerability has been resolved:
xsk: Fix race condition in AF_XDP generic RX path
Move rx_lock from xsk_socket to xsk_buff_pool.
Fix synchronization for shared umem mode in
generic RX path where multiple sockets share
single xsk_buff_pool.
RX queue is exclusive to xsk_socket, while FILL
queue can be shared between multiple sockets.
This could result in race condition where two
CPU cores access RX path of two different sockets
sharing the same umem.
Protect both queues by acquiring spinlock in shared
xsk_buff_pool.
Lock contention may be minimized in the future by some
per-thread FQ buffering.
It's safe and necessary to move spin_lock_bh(rx_lock)
after xsk_rcv_check():
* xs->pool and spinlock_init is synchronized by
xsk_bind() -> xsk_is_bound() memory barriers.
* xsk_rcv_check() may return true at the moment
of xsk_release() or xsk_unbind_dev(),
however this will not cause any data races or
race conditions. xsk_unbind_dev() removes xdp
socket from all maps and waits for completion
of all outstanding rx operations. Packets in
RX path will either complete safely or drop.
EPSS Score: 0.02%
May 20th, 2025 (about 1 month ago)
|
|
CVE-2025-37919 |
Description: In the Linux kernel, the following vulnerability has been resolved:
ASoC: amd: acp: Fix NULL pointer deref in acp_i2s_set_tdm_slot
Update chip data using dev_get_drvdata(dev->parent) to fix
NULL pointer deref in acp_i2s_set_tdm_slot.
EPSS Score: 0.02%
May 20th, 2025 (about 1 month ago)
|
