CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: The 19-year-old Assumption College student, Matthew Lane, also was charged Tuesday with hacking and demanding a ransom payment from an unnamed telecommunications company, according to Massachusetts federal prosecutors.
May 21st, 2025 (about 1 month ago)
|

|
Description: Earlier this month, a coordinated disruption action targeting the Lumma malware-as-a-service (MaaS) information stealer operation seized thousands of domains, part of its infrastructure backbone worldwide. [...]
May 21st, 2025 (about 1 month ago)
|

|
Description: A newly released joint advisory has exposed a long-running espionage campaign by Russia’s GRU targeting Western logistics companies and technology firms critical to aid delivery in Ukraine. The effort, attributed to GRU Unit 26165, widely tracked as APT28 or the name Fancy Bear, has exploited corporate infrastructure using credential attacks, spear phishing, and malware to …
The post Russian GRU Cyber Campaign Targets Western Logistics and Tech Firms appeared first on CyberInsider.
May 21st, 2025 (about 1 month ago)
|

|
Description: Popular VR game Gorilla Tag partnered with the company k-ID to comply with age verification laws.
May 21st, 2025 (about 1 month ago)
|
|
CVE-2025-20152 |
Description:
A vulnerability in the RADIUS message processing feature of Cisco Identity Services Engine (ISE) could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on an affected device.
This vulnerability is due to improper handling of certain RADIUS requests. An attacker could exploit this vulnerability by sending a specific authentication request to a network access device (NAD) that uses Cisco ISE for authentication, authorization, and accounting (AAA). A successful exploit could allow the attacker to cause Cisco ISE to reload.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ise-restart-ss-uf986G2Q
Security Impact Rating: High
CVE: CVE-2025-20152
EPSS Score: 0.11%
May 21st, 2025 (about 1 month ago)
|
|
CVE-2025-20267 |
Description:
A vulnerability in the web-based management interface of Cisco Identity Services Engine (ISE) could allow an authenticated, remote attacker to conduct cross-site scripting (XSS) attacks against a user of the interface.
This vulnerability is due to insufficient validation of user-supplied input by the web-based management interface of an affected system. An attacker could exploit this vulnerability by injecting malicious code into specific pages of the interface. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive, browser-based information. To exploit this vulnerability, the attacker must have valid administrative credentials.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ise-stored-xss-Yff54m73
Security Impact Rating: Medium
CVE: CVE-2025-20267
EPSS Score: 0.04%
May 21st, 2025 (about 1 month ago)
|
|
CVE-2025-20257 |
Description:
A vulnerability in an API subsystem of Cisco Secure Network Analytics Manager and Cisco Secure Network Analytics Virtual Manager could allow an authenticated, remote attacker with low privileges to generate fraudulent findings that are used to generate alarms and alerts on an affected product.
Thi vulnerability is due to insufficient authorization enforcement on a specific API. An attacker could exploit this vulnerability by authenticating as a low-privileged user and performing API calls with crafted input. A successful exploit could allow the attacker to obfuscate legitimate findings in analytics reports or create false indications with alarms and alerts on an affected device.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sna-apiacv-4B6X5ysw
Security Impact Rating: Medium
CVE: CVE-2025-20257
EPSS Score: 0.04%
May 21st, 2025 (about 1 month ago)
|
|
CVE-2025-20255 |
Description:
A vulnerability in client join services of Cisco Webex Meetings could allow an unauthenticated, remote attacker to manipulate cached HTTP responses within the meeting join service.
This vulnerability is due to improper handling of malicious HTTP requests to the affected service. An attacker could exploit this vulnerability by manipulating stored HTTP responses within the service, also known as HTTP cache poisoning. A successful exploit could allow the attacker to cause the Webex Meetings service to return incorrect HTTP responses to clients.
Cisco has addressed this vulnerability in the service, and no customer action is necessary to update on-premises software or devices. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-webex-cache-Q4xbkQBG
Security Impact Rating: Medium
CVE: CVE-2025-20255
EPSS Score: 0.02%
May 21st, 2025 (about 1 month ago)
|
|
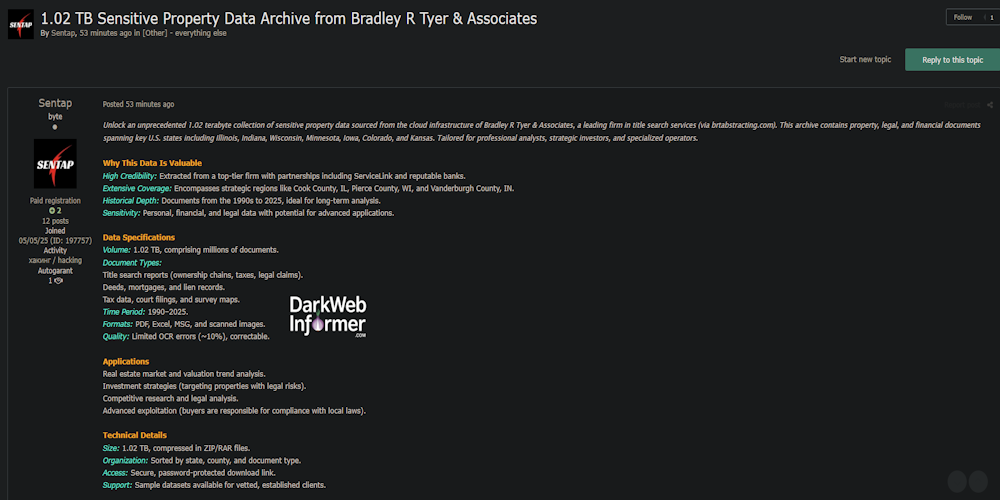
Description: Alleged Data for Sale of Bradley R. Tyer & Associates
May 21st, 2025 (about 1 month ago)
|

|
May 21st, 2025 (about 1 month ago)
|
