CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-4575 |
Description: Issue summary: Use of -addreject option with the openssl x509 application adds
a trusted use instead of a rejected use for a certificate.
Impact summary: If a user intends to make a trusted certificate rejected for
a particular use it will be instead marked as trusted for that use.
A copy & paste error during minor refactoring of the code introduced this
issue in the OpenSSL 3.5 version. If, for example, a trusted CA certificate
should be trusted only for the purpose of authenticating TLS servers but not
for CMS signature verification and the CMS signature verification is intended
to be marked as rejected with the -addreject option, the resulting CA
certificate will be trusted for CMS signature verification purpose instead.
Only users which use the trusted certificate format who use the openssl x509
command line application to add rejected uses are affected by this issue.
The issues affecting only the command line application are considered to
be Low severity.
The FIPS modules in 3.5, 3.4, 3.3, 3.2, 3.1 and 3.0 are not affected by this
issue.
OpenSSL 3.4, 3.3, 3.2, 3.1, 3.0, 1.1.1 and 1.0.2 are also not affected by this
issue.
EPSS Score: 0.03%
May 22nd, 2025 (about 1 month ago)
|

|
Description: Chinese hackers have been exploiting a remote code execution flaw in Ivanti Endpoint Manager Mobile (EPMM) to breach high-profile organizations worldwide. [...]
May 22nd, 2025 (about 1 month ago)
|

|
Description: One scheduled speaker has also pulled out of the New York-based event and specifically pointed to Trump’s mass deportation efforts.
May 22nd, 2025 (about 1 month ago)
|
|
Description: Russia-aligned TAG-110 shifts to .dotm phishing lures in a 2025 campaign against Tajikistan’s public sector, advancing cyber-espionage in Central Asia.
May 22nd, 2025 (about 1 month ago)
|

|
Description: Chinese-speaking hackers have exploited a now-patched Trimble Cityworks zero-day to breach multiple local governing bodies across the United States. [...]
May 22nd, 2025 (about 1 month ago)
|

|
Description:
Today, CISA, the National Security Agency, the Federal Bureau of Investigation, and international partners released a joint Cybersecurity Information Sheet on AI Data Security: Best Practices for Securing Data Used to Train & Operate AI Systems.
This information sheet highlights the critical role of data security in ensuring the accuracy, integrity, and trustworthiness of AI outcomes. It outlines key risks that may arise from data security and integrity issues across all phases of the AI lifecycle, from development and testing to deployment and operation.
Defense Industrial Bases, National Security Systems owners, federal agencies, and Critical Infrastructure owners and operators are encouraged to review this information sheet and implement the recommended best practices and mitigation strategies to protect sensitive, proprietary, and mission critical data in AI-enabled and machine learning systems. These include adopting robust data protection measures; proactively managing risks; and strengthening monitoring, threat detection, and network defense capabilities.
As AI systems become more integrated into essential operations, organizations must remain vigilant and take deliberate steps to secure the data that powers them. For more information on securing AI data, see CISA’s Artificial Intelligence webpage.
May 22nd, 2025 (about 1 month ago)
|

|
Description: A privilege escalation flaw has been demonstrated in Windows Server 2025 that makes it possible for attackers to compromise any user in Active Directory (AD).
"The attack exploits the delegated Managed Service Account (dMSA) feature that was introduced in Windows Server 2025, works with the default configuration, and is trivial to implement," Akamai security researcher Yuval Gordon said in a
May 22nd, 2025 (about 1 month ago)
|

|
May 22nd, 2025 (about 1 month ago)
|
|
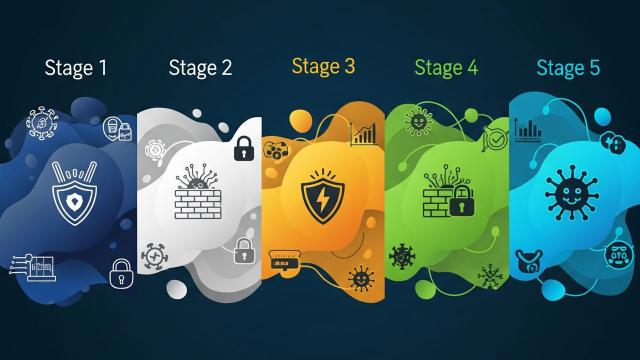
Description: While credential abuse is a primary initial access vector, identity compromise plays a key role in most stages of a cyber attack. Here’s what you need to know — and how Tenable can help.Identity compromise plays a pivotal role in how attackers move laterally through an organization. Credential abuse is the top initial access vector, implicated in 22% of breaches, according to the 2025 Verizon Data Breach Investigations Report, followed closely by vulnerability exploitation (20%). But identity compromise doesn’t stop after initial access. It plays a key role in five stages of a cyber attack.Understanding the following stages of an attack helps illuminate where identity becomes a threat vector:Initial accessReconnaissanceLateral movement and privilege escalationPersistence and detection evasionDeploymentBelow, we explore actions security teams can take to protect identities in each of these stages. While the guidance we share here is based on protecting on-premises Microsoft Active Directory environments, it’s worth considering how credential compromise can affect Microsoft Entra ID and hybrid identity infrastructure. We also discuss how Tenable Identity Exposure, available in the Tenable One Exposure Management Platform, can be used at each stage to provide security teams with valuable insights to help them proactively reduce their exposure to cyber attacks.Stage 1: Initial accessAttackers need a foothold and credential abuse enables them to get one. To prevent credentials ...
May 22nd, 2025 (about 1 month ago)
|

|
Description: The Federal Trade Commission (FTC) has finalized an order requiring web hosting giant GoDaddy to secure its services to settle charges of data security failures that led to several data breaches since 2018. [...]
May 22nd, 2025 (about 1 month ago)
|
