Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
June 4th, 2025 (3 days ago)
|

|
Description: The Ukrainian police arrested a 35-year-old hacker who breached 5,000 accounts at an international hosting company and used them to mine cryptocurrency, resulting in $4.5 million in damages. [...]
June 4th, 2025 (3 days ago)
|

|
Description: Cisco has released patches to address three vulnerabilities with public exploit code in its Identity Services Engine (ISE) and Customer Collaboration Platform (CCP) solutions. [...]
June 4th, 2025 (3 days ago)
|

|
Description: CISA, the Federal Bureau of Investigation (FBI), and the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) have issued an updated advisory on Play ransomware, also known as Playcrypt. This advisory highlights new tactics, techniques, and procedures used by the Play ransomware group and provides updated indicators of compromise (IOCs) to enhance threat detection.
Since June 2022, Playcrypt has targeted diverse businesses and critical infrastructure across North America, South America, and Europe, becoming one of the most active ransomware groups in 2024. The FBI has identified approximately 900 entities allegedly exploited by these ransomware actors as of May 2025.
Recommended mitigations include:
Implementing multifactor authentication;
Maintaining offline data backups;
Developing and testing a recovery plan; and
Keeping all operating systems, software, and firmware updated.
Stay vigilant and take proactive measures to protect your organization.
June 4th, 2025 (3 days ago)
|

|
Description: The FBI and Dutch national police were among the law enforcement agencies that seized domains used by BidenCash, a cybercrime marketplace attributed to millions of dollars in fraud since late 2022.
June 4th, 2025 (3 days ago)
|
|
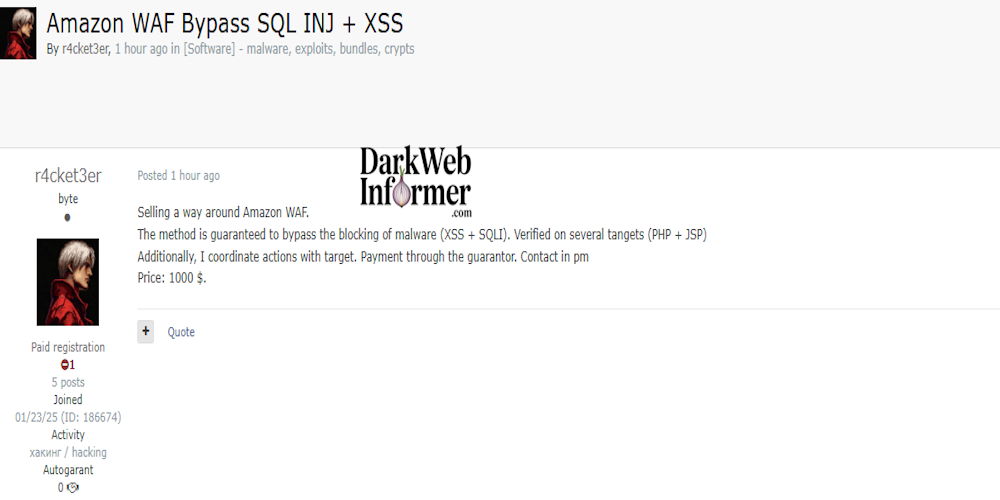
Description: Alleged Sale of an Exploit to Bypass Amazon WAF
June 4th, 2025 (3 days ago)
|
|
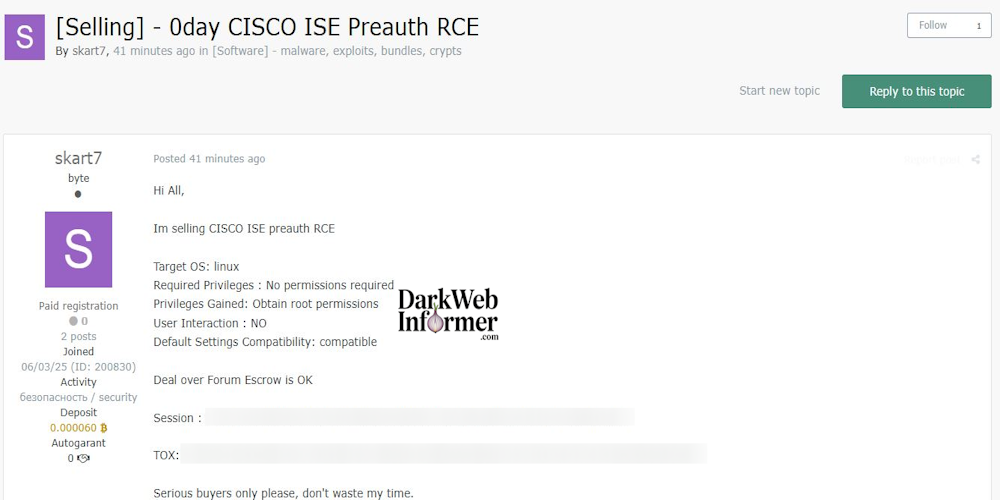
Description: Alleged sale of Cisco ISE Pre-auth Remote Code Execution (0day) Exploit
June 4th, 2025 (3 days ago)
|

|
Description: By understanding the neurological realities of human attention, organizations can build more sustainable security operations that protect not only their digital assets but also the well-being of those who defend them.
June 4th, 2025 (3 days ago)
|

|
Description: The Main Intelligence Directorate (GUR) of Ukraine's Ministry of Defense claims it hacked the Russian aerospace and defense company Tupolev, which develops Russia's supersonic strategic bombers. [...]
June 4th, 2025 (3 days ago)
|

|
Description: An international group of researchers found that simply rerecording deepfake audio with natural acoustics in the background allows it to bypass detection models at a higher-than-expected rate.
June 4th, 2025 (3 days ago)
|
