CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
CVE-2025-32875 |
Description: An issue was discovered in the COROS application through 3.8.12 for Android. Bluetooth pairing and bonding is neither initiated nor enforced by the application itself. Also, the watch does not enforce pairing and bonding. As a result, any data transmitted via BLE remains unencrypted, allowing attackers within Bluetooth range to eavesdrop on the communication. Furthermore, even if a user manually initiates pairing and bonding in the Android settings, the application continues to transmit data without requiring the watch to be bonded. This fallback behavior enables attackers to exploit the communication, for example, by conducting an active machine-in-the-middle attack.
EPSS Score: 0.01% SSVC Exploitation: poc
June 20th, 2025 (27 days ago)
|

|
Description: This week, we discuss Deadheads and doxxing sites.
June 20th, 2025 (27 days ago)
|
|
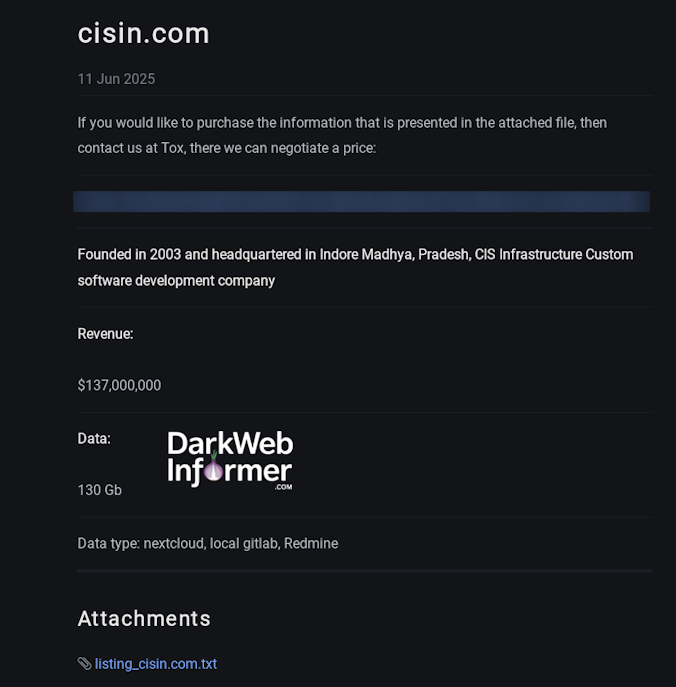
Description: Cyber Infrastructure (CIS) Falls Victim to J Group Ransomware
June 20th, 2025 (27 days ago)
|

|
Description: DNN.PLATFORM allows specially crafted content in URLs could be used with TokenReplace and not be properly sanitized by some SkinObjects. This vulnerability is fixed in 10.0.1.
References
https://github.com/dnnsoftware/Dnn.Platform/security/advisories/GHSA-pf4h-vrv6-cmvr
https://github.com/dnnsoftware/Dnn.Platform/commit/74f6de68da1572c1d7e9c6e30e9f77f7c5596b1b
https://github.com/advisories/GHSA-pf4h-vrv6-cmvr
June 20th, 2025 (27 days ago)
|

|
Description: DNN.PLATFORM allows a specially crafted request can inject scripts in the Activity Feed Attachments endpoint which will then render in the feed, resulting in a cross-site scripting attack. This vulnerability is fixed in 10.0.1.
References
https://github.com/dnnsoftware/Dnn.Platform/security/advisories/GHSA-wwc9-wmm3-2pmf
https://github.com/dnnsoftware/Dnn.Platform/commit/e739b8d5ad487509d9ef469cdb058b0398646c5b
https://github.com/advisories/GHSA-wwc9-wmm3-2pmf
June 20th, 2025 (27 days ago)
|

|
Description: On Friday, American insurance giant Aflac disclosed that its systems were breached in a broader campaign targeting insurance companies across the United States by attackers who may have stolen personal and health information. [...]
June 20th, 2025 (27 days ago)
|
|
Description: Learn how DPRK's BlueNoroff group executed a Web3 macOS intrusion. Explore the attack chain, malware, and techniques in our detailed technical report.
June 20th, 2025 (27 days ago)
|
|
CVE-2025-32880 |
Description: An issue was discovered on COROS PACE 3 devices through 3.0808.0. It implements a function to connect the watch to a WLAN. With WLAN access, the COROS Pace 3 downloads firmware files via HTTP. However, the communication is not encrypted and allows sniffing and machine-in-the-middle attacks.
EPSS Score: 0.02%
June 20th, 2025 (27 days ago)
|
|
CVE-2025-32879 |
Description: An issue was discovered on COROS PACE 3 devices through 3.0808.0. It starts advertising if no device is connected via Bluetooth. This allows an attacker to connect with the device via BLE if no other device is connected. While connected, none of the BLE services and characteristics of the device require any authentication or security level. Therefore, any characteristic, depending on their mode of operation (read/write/notify), can be used by the connected attacker. This allows, for example, configuring the device, sending notifications, resetting the device to factory settings, or installing software.
EPSS Score: 0.11%
June 20th, 2025 (27 days ago)
|
|
CVE-2025-32878 |
Description: An issue was discovered on COROS PACE 3 devices through 3.0808.0. It implements a function to connect the watch to a WLAN. This function is mainly for downloading firmware files. Before downloading firmware files, the watch requests some information about the firmware via HTTPS from the back-end API. However, the X.509 server certificate within the TLS handshake is not validated by the device. This allows an attacker within an active machine-in-the-middle position, using a TLS proxy and a self-signed certificate, to eavesdrop and manipulate the HTTPS communication. This could be abused, for example, for stealing the API access token of the assigned user account.
EPSS Score: 0.03%
June 20th, 2025 (27 days ago)
|
