CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: A critical infrastructure entity within Ukraine was targeted by a previously unseen data wiper malware named PathWiper, according to new findings from Cisco Talos.
"The attack was instrumented via a legitimate endpoint administration framework, indicating that the attackers likely had access to the administrative console, that was then used to issue malicious commands and deploy PathWiper across
June 6th, 2025 (22 days ago)
|

|
Description: All data of this company will be available for download on 18.06.2025.Belvedere is one of the smallest and oldest cities in California. It was incorporated in 1896 and is located north of San Francisco across the Golden Gate Bridge in Marin C ...
June 5th, 2025 (22 days ago)
|

|
Description: The vulnerability, with a 9.9 CVSS score on a 10-point scale, results in different Cisco ISE deployments all sharing the same credentials as long as the software release and cloud platform remain the same.
June 5th, 2025 (22 days ago)
|

|
Description: Cisco Talos observed a destructive attack on a critical infrastructure entity within Ukraine, using a previously unknown wiper we are calling “PathWiper.”
June 5th, 2025 (22 days ago)
|

|
Description: Cisco has released patches to address three vulnerabilities with public exploit code in its Identity Services Engine (ISE) and Customer Collaboration Platform (CCP) solutions. [...]
June 4th, 2025 (23 days ago)
|
|
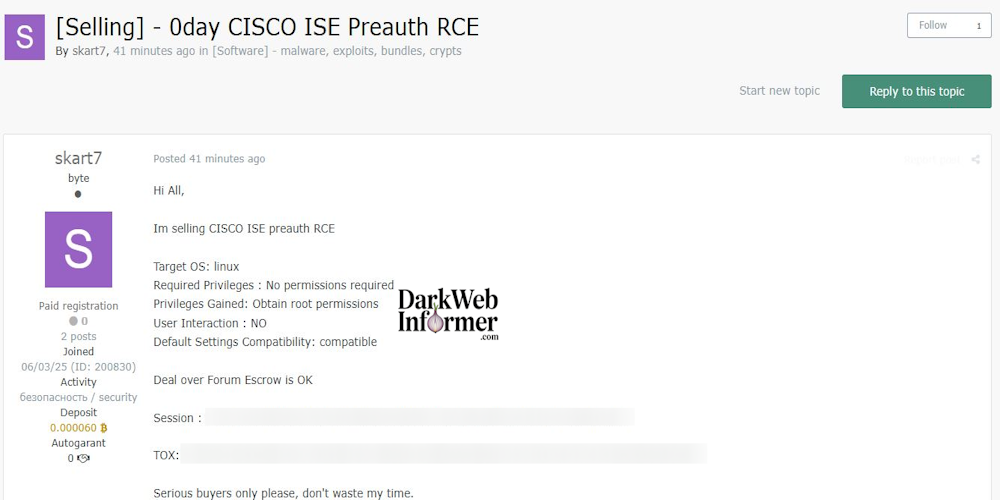
Description: Alleged sale of Cisco ISE Pre-auth Remote Code Execution (0day) Exploit
June 4th, 2025 (23 days ago)
|
|
CVE-2025-20130 |
Description:
A vulnerability in the API of Cisco Identity Services Engine (ISE) and Cisco ISE Passive Identity Connector (ISE-PIC) could allow an authenticated, remote attacker with administrative privileges to upload files to an affected device.
This vulnerability is due to improper validation of the file copy function. An attacker could exploit this vulnerability by sending a crafted file upload request to a specific API endpoint. A successful exploit could allow the attacker to upload arbitrary files to an affected system.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ise-file-upload-P4M8vwXY
Security Impact Rating: Medium
CVE: CVE-2025-20130
EPSS Score: 0.04%
June 4th, 2025 (23 days ago)
|
|
CVE-2025-20163 |
Description:
A vulnerability in the SSH implementation of Cisco Nexus Dashboard Fabric Controller (NDFC) could allow an unauthenticated, remote attacker to impersonate Cisco NDFC-managed devices.
This vulnerability is due to insufficient SSH host key validation. An attacker could exploit this vulnerability by performing a machine-in-the-middle attack on SSH connections to Cisco NDFC-managed devices, which could allow an attacker to intercept this traffic. A successful exploit could allow the attacker to impersonate a managed device and capture user credentials.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ndfc-shkv-snQJtjrp
Security Impact Rating: High
CVE: CVE-2025-20163
EPSS Score: 0.03%
June 4th, 2025 (23 days ago)
|
|
CVE-2025-20259 |
Description:
Multiple vulnerabilities in the update process of Cisco ThousandEyes Endpoint Agent for Windows could allow an authenticated, local attacker to delete arbitrary files on an affected device.
These vulnerabilities are due to improper access controls on files that are in the local file system. An attacker could exploit these vulnerabilities by using a symbolic link to perform an agent upgrade that redirects the delete operation of any protected file. A successful exploit could allow the attacker to delete arbitrary files from the file system of the affected device.
Cisco has released software updates that address these vulnerabilities. There are no workarounds that address these vulnerabilities.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-te-endagent-filewrt-zNcDqNRJ
Security Impact Rating: Medium
CVE: CVE-2025-20259
EPSS Score: 0.04%
June 4th, 2025 (23 days ago)
|
|
CVE-2025-20275 |
Description:
A vulnerability in the file opening process of Cisco Unified Contact Center Express (Unified CCX) Editor could allow an unauthenticated attacker to execute arbitrary code on an affected device.
This vulnerability is due to insecure deserialization of Java objects by the affected software. An attacker could exploit this vulnerability by persuading an authenticated, local user to open a crafted .aef file. A successful exploit could allow the attacker to execute arbitrary code on the host that is running the editor application with the privileges of the user who launched it.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-uccx-editor-rce-ezyYZte8
Security Impact Rating: Medium
CVE: CVE-2025-20275
EPSS Score: 0.07%
June 4th, 2025 (23 days ago)
|
