CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
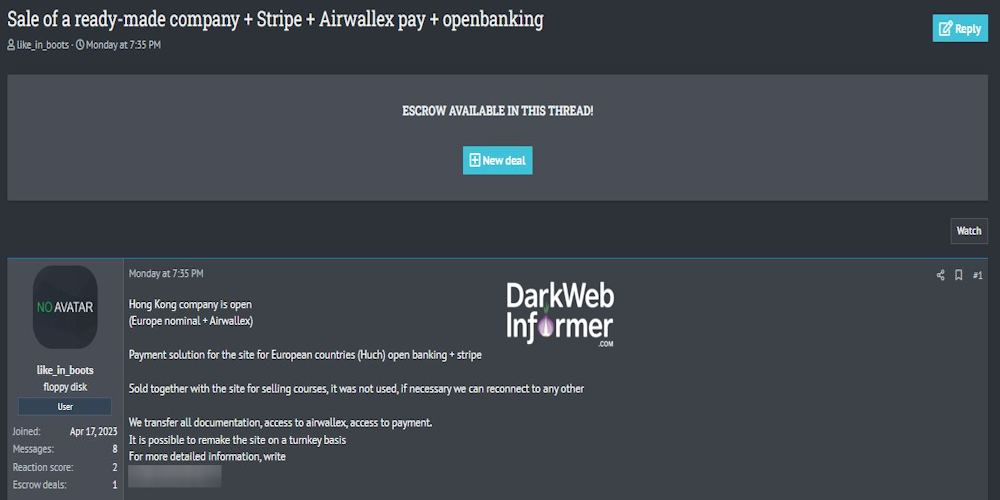
Description: Alleged Sale of Data from an Unidentified Company in Hong Kong
May 27th, 2025 (23 days ago)
|

|
Description: A validation bypass vulnerability was discovered prior to version 2.13.0, where multiple validations defined for the same attribute could be silently overridden. Due to how the framework merged validation rules across multiple contexts (such as index, store, and update actions), malicious actors could exploit this behavior by crafting requests that bypass expected validation rules, potentially injecting unexpected or dangerous parameters into the application.
Impact:
This could lead to unauthorized data being accepted or processed by the API, depending on the context in which the validation was bypassed.
Patch:
The issue was fixed in PR #172 by ensuring that multiple rule definitions are merged correctly rather than overwritten.
References
https://github.com/Lomkit/laravel-rest-api/security/advisories/GHSA-69rh-hccr-cxrj
https://github.com/Lomkit/laravel-rest-api/pull/172
https://github.com/Lomkit/laravel-rest-api/commit/88b14587b4efd7e59d7379658c606d325bb513b4
https://github.com/advisories/GHSA-69rh-hccr-cxrj
May 27th, 2025 (23 days ago)
|

|
Description: Cape Robbin is the ultimate runway-inspired fashion brand for women’s shoes, offering a combination of style and affordability. Featuring bold heels and chic sandals, each designed with the fashion-conscious woman in mind. Cape Robbin is a ...
May 27th, 2025 (23 days ago)
|

|
Description: Sina Gholinejad admitted to using the Robbinhood ransomware variant to extort ransom payments from dozens of victims.
May 27th, 2025 (23 days ago)
|

|
Description: Lasercam specializes in providing advanced milling machines and a variety of cutting tools including dies, blanking tools, and stripping tools. Their products cater to industries that require precision machining and tool-making solutions. Whi ...
May 27th, 2025 (23 days ago)
|

|
Description: An Iranian national has pleaded guilty to participating in the Robbinhood ransomware operation, which was used to breach the networks, steal data, and encrypt devices of U.S. cities and organizations in an attempt to extort millions of dollars over a five-year span. [...]
May 27th, 2025 (23 days ago)
|
|
CVE-2025-45475 |
Description: maccms10 v2025.1000.4047 is vulnerable to Server-Side request forgery (SSRF) in Friend Link Management.
EPSS Score: 0.04%
May 27th, 2025 (23 days ago)
|
|
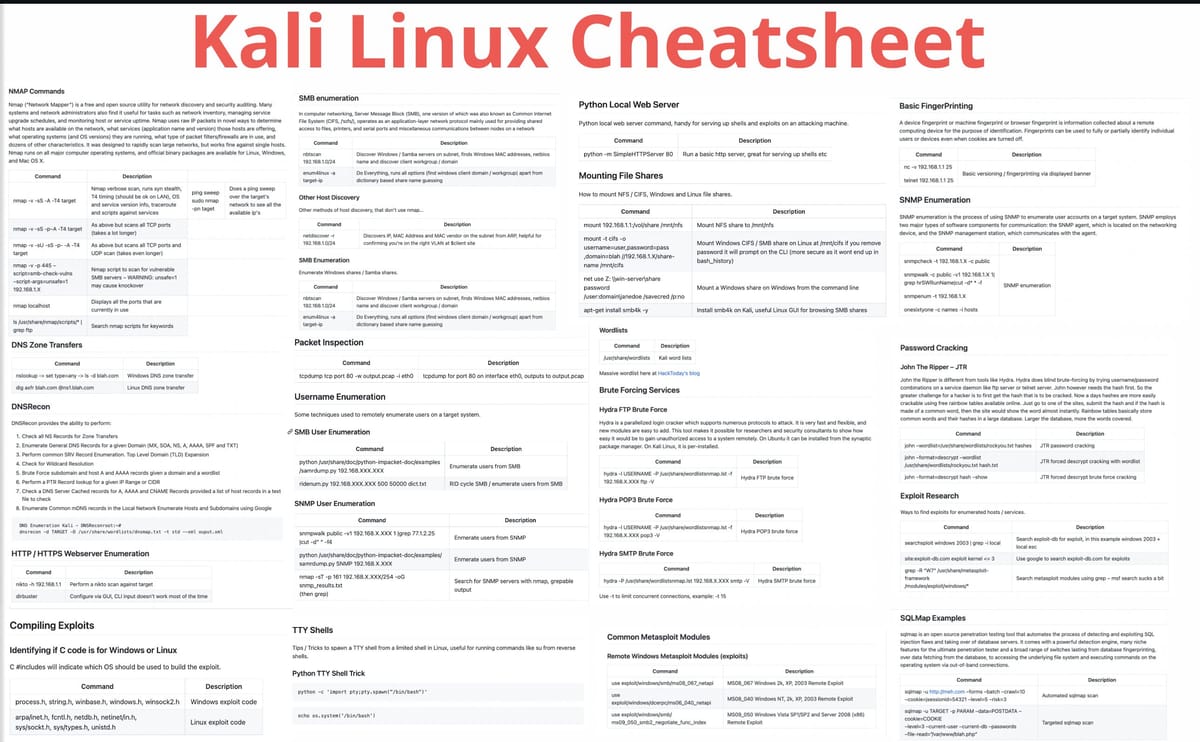
Description: Kali Linux Cheatsheet (2023)
May 27th, 2025 (23 days ago)
|

|
Description: Description
In Strapi latest version, at function Settings -> Webhooks, the application allows us to input a URL in order to create a Webook connection. However, we can input into this field the local domains such as localhost, 127.0.0.1, 0.0.0.0,.... in order to make the Application fetching into the internal itself, which causes the vulnerability Server - Side Request Forgery (SSRF).
Payloads
http://127.0.0.1:80 -> The Port is not open
http://127.0.0.1:1337 -> The Port which Strapi is running on
Steps to Reproduce
First of all, let's input the URL http://127.0.0.1:80 into the URL field, and click "Save".
Next, use the "Trigger" function and use Burp Suite to capture the request / response
The server return request to http://127.0.0.1/ failed, reason: connect ECONNREFUSED 127.0.0.1:80, BECAUSE the Port 80 is not open, since we are running Strapi on Port 1337, let's change the URL we input above into http://127.0.0.1:1337
Continue to click the "Trigger" function, use Burp to capture the request / response
The server returns Method Not Allowed, which means that there actually is a Port 1337 running the machine.
PoC
Here is the Poc Video, please check:
https://drive.google.com/file/d/1EvVp9lMpYnGLmUyr16gQ_2RetI-GqYjV/view?usp=sharing
Impact
If there is a real server running Strapi with many ports open, by using this SSRF vulnerability, the attacker can brute-force through all 65535 ports to know what ports are open.
References
https://github.com/strapi/st...
May 27th, 2025 (23 days ago)
|

|
Description: Impact
The library functions getUserById, deleteUser, updateUserById, listFactors and deleteFactor did not require the user supplied values to be valid UUIDs. This could lead to a URL path traversal, resulting in the wrong API function being called.
Implementations that follow security best practice and validate user controlled inputs, such as the userId are not affected by this.
Patches
Strict value checks have been added to all affected functions. These functions now require that the userId and factorId parameters MUST be valid UUID (v4).
Patched version: >= 2.69.1
Workarounds
Implementations that follow security best practice and validate user controlled inputs, such as the userId are not affected by this. It is recommended that users of the auth-js library always follow security best practice and validate all inputs, before passing these to other functions or libraries.
References
https://github.com/supabase/auth-js/pull/1063
References
https://github.com/supabase/auth-js/security/advisories/GHSA-8r88-6cj9-9fh5
https://github.com/supabase/auth-js/pull/1063
https://github.com/supabase/auth-js/commit/1bcb76e479e51cd9bca2d7732d0bf3199e07a693
https://github.com/advisories/GHSA-8r88-6cj9-9fh5
May 27th, 2025 (23 days ago)
|
