CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Though Adidas said that no payment or financial information was affected in the breach, individuals who contacted the compamy's customer service help desk were impacted.
May 27th, 2025 (23 days ago)
|

|
Description: The DragonForce ransomware operation successfully breached a managed service provider and used its SimpleHelp remote monitoring and management (RMM) platform to steal data and deploy encryptors on downstream customers' systems. [...]
May 27th, 2025 (23 days ago)
|

|
Description: Alleged Data Breach of I Paid A Bribe
May 27th, 2025 (23 days ago)
|
|
CVE-2025-5222 |
Description: A stack buffer overflow was found in Internationl components for unicode (ICU ). While running the genrb binary, the 'subtag' struct overflowed at the SRBRoot::addTag function. This issue may lead to memory corruption and local arbitrary code execution.
EPSS Score: 0.02%
May 27th, 2025 (23 days ago)
|
|
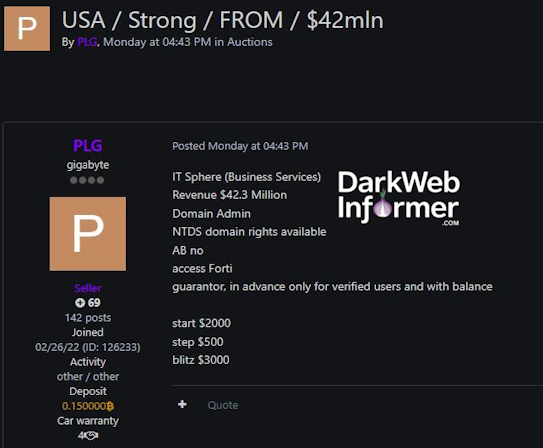
Description: Alleged Sale of FortiVPN Access to an Unidentified Business Services Company in USA
May 27th, 2025 (23 days ago)
|
|
CVE-2025-46173 |
Description: code-projects Online Exam Mastering System 1.0 is vulnerable to Cross Site Scripting (XSS) via the name field in the feedback form.
EPSS Score: 0.01%
May 27th, 2025 (23 days ago)
|
|
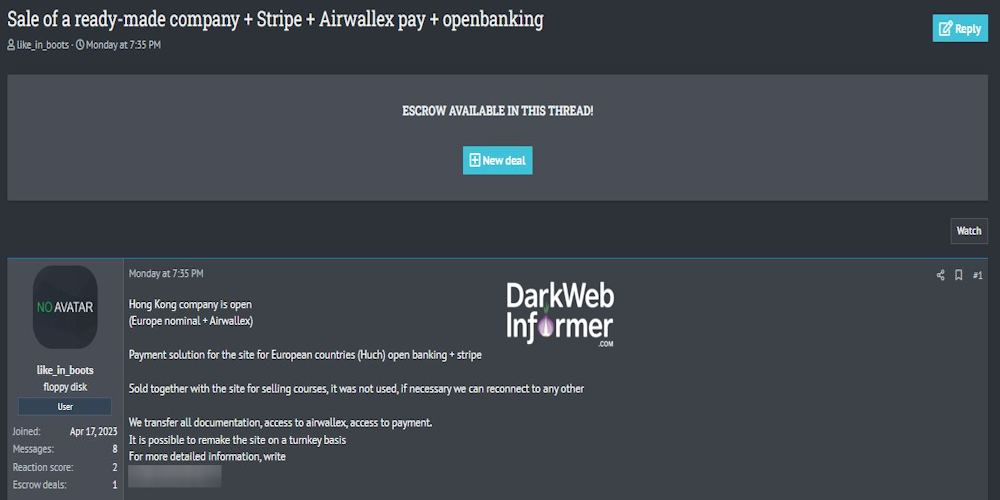
Description: Alleged Sale of Data from an Unidentified Company in Hong Kong
May 27th, 2025 (23 days ago)
|

|
Description: A validation bypass vulnerability was discovered prior to version 2.13.0, where multiple validations defined for the same attribute could be silently overridden. Due to how the framework merged validation rules across multiple contexts (such as index, store, and update actions), malicious actors could exploit this behavior by crafting requests that bypass expected validation rules, potentially injecting unexpected or dangerous parameters into the application.
Impact:
This could lead to unauthorized data being accepted or processed by the API, depending on the context in which the validation was bypassed.
Patch:
The issue was fixed in PR #172 by ensuring that multiple rule definitions are merged correctly rather than overwritten.
References
https://github.com/Lomkit/laravel-rest-api/security/advisories/GHSA-69rh-hccr-cxrj
https://github.com/Lomkit/laravel-rest-api/pull/172
https://github.com/Lomkit/laravel-rest-api/commit/88b14587b4efd7e59d7379658c606d325bb513b4
https://github.com/advisories/GHSA-69rh-hccr-cxrj
May 27th, 2025 (23 days ago)
|

|
Description: Cape Robbin is the ultimate runway-inspired fashion brand for women’s shoes, offering a combination of style and affordability. Featuring bold heels and chic sandals, each designed with the fashion-conscious woman in mind. Cape Robbin is a ...
May 27th, 2025 (23 days ago)
|

|
Description: Sina Gholinejad admitted to using the Robbinhood ransomware variant to extort ransom payments from dozens of victims.
May 27th, 2025 (23 days ago)
|
