Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: The incident should serve as a critical wake-up call. The stakes are simply too high to treat AI security as an afterthought — especially when the Dark Web stands ready to capitalize on every vulnerability.
April 22nd, 2025 (about 2 months ago)
|

|
Description: Microsoft on Monday announced that it has moved the Microsoft Account (MSA) signing service to Azure confidential virtual machines (VMs) and that it's also in the process of migrating the Entra ID signing service as well.
The disclosure comes about seven months after the tech giant said it completed updates to Microsoft Entra ID and MS for both public and United States government clouds to
April 22nd, 2025 (about 2 months ago)
|

|
Description: Cybersecurity researchers have flagged a new malicious campaign related to the North Korean state-sponsored threat actor known as Kimsuky that exploits a now-patched vulnerability impacting Microsoft Remote Desktop Services to gain initial access.
The activity has been named Larva-24005 by the AhnLab Security Intelligence Center (ASEC).
"In some systems, initial access was gained through
April 21st, 2025 (about 2 months ago)
|
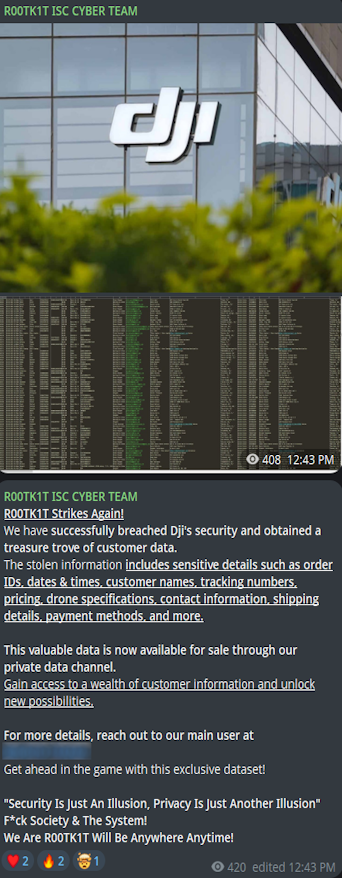
|
Description: Alleged Data Breach of DJI
April 21st, 2025 (about 2 months ago)
|

|
Description: ClickFix attacks are being increasingly adopted by threat actors of all levels, with researchers now seeing multiple advanced persistent threat (APT) groups from North Korea, Iran, and Russia utilizing the tactic to breach networks. [...]
April 21st, 2025 (about 2 months ago)
|

|
Description: The problem is simple: all breaches start with initial access, and initial access comes down to two primary attack vectors – credentials and devices. This is not news; every report you can find on the threat landscape depicts the same picture.
The solution is more complex. For this article, we’ll focus on the device threat vector. The risk they pose is significant, which is why device
April 21st, 2025 (about 2 months ago)
|

|
Description: The Interlock ransomware gang now uses ClickFix attacks that impersonate IT tools to breach corporate networks and deploy file-encrypting malware on devices. [...]
April 18th, 2025 (about 2 months ago)
|

|
Description: The agency is recommending that organizations and individuals implement its recommendations to prevent the misuse of stolen data, though Oracle has yet to publicly do the same for its customers.
April 18th, 2025 (about 2 months ago)
|

|
Description: The agency is recommending that organizations and individuals implement its recommendations to prevent the misuse of stolen data, though Oracle has yet to publicly do the same for its customers.
April 18th, 2025 (about 2 months ago)
|

|
Description: Around the world, governments are setting higher-bar regulations with clear corporate accountability for breaches on the belief organizations won't drive up security maturity for operational technology unless they're made to.
April 18th, 2025 (about 2 months ago)
|
