Example Searches:
CVE
Threat Actors
Countries
Vendors
Severity
Known Exploited

|
Description: Microsoft has released emergency Windows updates to address a known issue affecting local audit logon policies in Active Directory Group Policy. [...]
April 14th, 2025 (about 2 months ago)
|

|
Description: According to references spotted on OpenAI's website, the Microsoft-backed AI startup is planning to launch five new models this week, including GPT-4.1, 4.1 nano, and 4.1 mini. [...]
April 14th, 2025 (about 2 months ago)
|

|
Description: Microsoft warned IT admins that some Windows Server 2025 domain controllers might become inaccessible after a restart, causing apps and services to fail or remain unreachable. [...]
April 14th, 2025 (about 2 months ago)
|

|
Description: Phishing-as-a-service (PhaaS) platform Tycoon2FA, known for bypassing multi-factor authentication on Microsoft 365 and Gmail accounts, has received updates that improve its stealth and evasion capabilities. [...]
April 12th, 2025 (about 2 months ago)
|

|
April 11th, 2025 (about 2 months ago)
|

|
Description: Microsoft is testing a new Defender for Endpoint capability that will block traffic to and from undiscovered endpoints to thwart attackers' lateral network movement attempts. [...]
April 11th, 2025 (about 2 months ago)
|
|
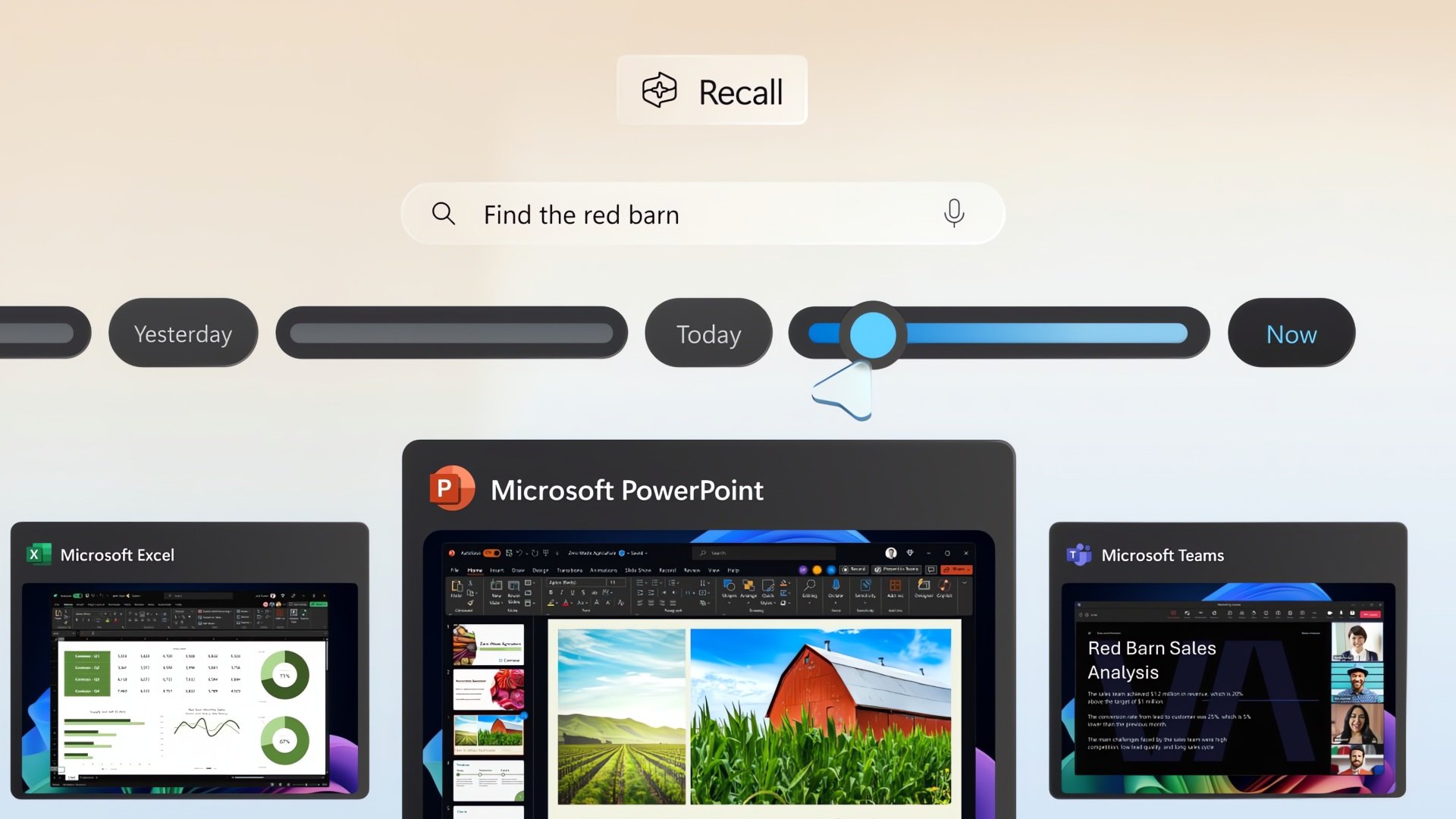
Description: Microsoft is gradually rolling out the AI-powered Windows Recall feature to Insiders in the Release Preview channel before making it generally available to all Windows users with Copilot+ PCs. [...]
April 11th, 2025 (about 2 months ago)
|

|
Description: ReliaQuest uncovered a sophisticated malware campaign that begins with Microsoft Teams phishing and escalates into a rare persistence technique involving Type Library (TypeLib) hijacking — a method never previously seen in the wild. The campaign also delivered a newly discovered PowerShell backdoor, targeting finance and professional services sectors with high precision. The investigation was initiated …
The post Novel Microsoft Teams Attack Employs Unseen Malware Persistence Method appeared first on CyberInsider.
April 11th, 2025 (about 2 months ago)
|

|
Description: Microsoft has now confirmed that an April 2025 Windows security update is creating a new empty "inetpub" folder and warned users not to delete it. [...]
April 11th, 2025 (about 2 months ago)
|

|
Description: The Chromium-based Microsoft Edge has seen up to 9% performance improvements following the release of version 134. [...]
April 11th, 2025 (about 2 months ago)
|
